Unveiling Zero Trust Network Access (ZTNA): The Future of Secure Networking
In today’s digital landscape, the traditional network security model is increasingly insufficient to protect against sophisticated cyber threats. As businesses adapt to remote work and cloud-based infrastructures, the need for a more robust and adaptive security framework has never been greater. Enter Zero Trust Network Access (ZTNA), a revolutionary approach that’s reshaping the way we think about network security.
What is Zero Trust Network Access (ZTNA)?
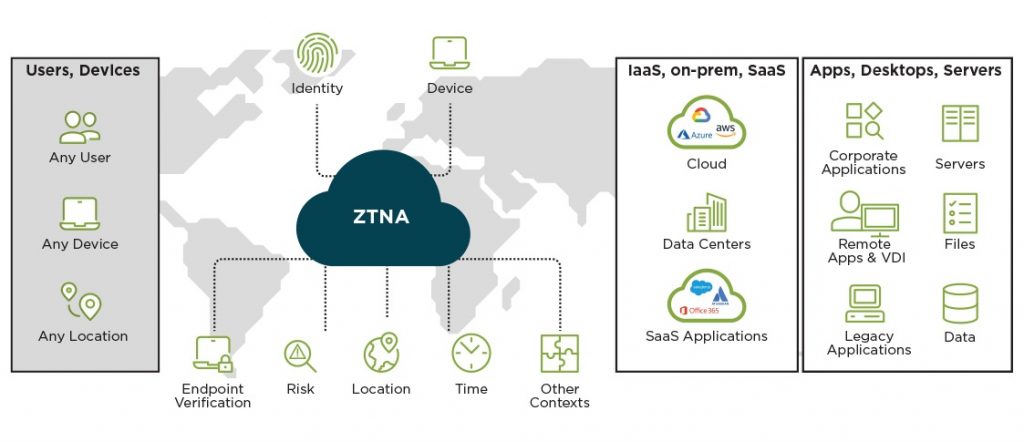
Zero Trust Network Access (ZTNA) is a security model based on the principle of “never trust, always verify.” Unlike traditional security models that rely on perimeter defenses to keep threats out, ZTNA assumes that threats can exist both inside and outside the network. Therefore, it enforces strict identity verification and access controls, regardless of where the user or device is located.
ZTNA operates on the assumption that no user or device, whether inside or outside the network, should be trusted by default. Every access request is verified as though it originates from an open, untrusted network. This model aims to minimize the risk of internal and external threats by continuously validating user identity and device integrity.

Core Principles of ZTNA
- Least Privilege Access: Users and devices are granted the minimum level of access required to perform their functions. This minimizes the potential damage from compromised accounts or devices. For instance, an employee in the finance department would only have access to financial systems and not to the HR or IT systems, thus reducing the potential impact of any security breach.
- Continuous Verification: Authentication and authorization are not one-time events but continuous processes. Every access request is verified in real-time based on the user’s identity, location, device health, and other contextual factors. For example, if a user’s behavior deviates from their usual patterns, additional authentication steps might be triggered.
- Micro-Segmentation: The network is divided into small, isolated segments to limit lateral movement of threats. Each segment enforces its own access controls and security policies. This means that even if an attacker breaches one segment, they cannot easily move to another part of the network.
- End-to-End Encryption: Data is encrypted at all stages of its journey, ensuring that it remains secure from eavesdropping or tampering. This encryption covers data in transit between devices and applications, as well as data at rest within storage systems.
How ZTNA Works
ZTNA operates by creating secure, encrypted tunnels between users and the resources they need to access. Here’s a detailed overview of the process:
- User Authentication: When a user attempts to access a resource, they must first authenticate their identity through multi-factor authentication (MFA). This could include something they know (password), something they have (security token), and something they are (biometric verification).
- Device Posture Check: The system evaluates the security posture of the user’s device, checking for compliance with security policies (e.g., up-to-date antivirus software, device encryption). Devices failing to meet these criteria are either denied access or placed in a restricted mode where they can only access resources necessary to remediate their posture.
- Policy Enforcement: Based on the user’s identity and device posture, the ZTNA solution enforces access policies. These policies determine whether the user can access the requested resource and what level of access they have. Policies can be very granular, specifying access based on the user’s role, location, the sensitivity of the data, and other factors.
- Access Granted via Secure Tunnel: If the user meets all the criteria, access is granted through a secure, encrypted tunnel. This tunnel ensures that data remains protected during transmission, preventing unauthorized interception and tampering.
Benefits of ZTNA
- Enhanced Security: By continuously verifying users and devices, ZTNA significantly reduces the risk of unauthorized access and data breaches. Continuous verification means that even if an attacker obtains valid credentials, additional security measures will be triggered if the system detects suspicious activity.
- Improved User Experience: ZTNA solutions often integrate seamlessly with existing IT infrastructure, providing users with secure, frictionless access to resources. Instead of dealing with cumbersome VPN connections, users can access resources through a single sign-on (SSO) interface.
- Scalability: As organizations grow and adopt new technologies, ZTNA can easily scale to accommodate additional users, devices, and resources without compromising security. This scalability is particularly beneficial for businesses with fluctuating workforces or extensive remote work policies.
- Reduced Attack Surface: Micro-segmentation and least privilege access limit the potential damage from compromised accounts or devices, reducing the overall attack surface. By isolating resources and strictly controlling access, ZTNA makes it more difficult for attackers to move laterally within the network.
Comparison with Virtual Private Networks (VPNs)
While ZTNA and VPNs both aim to provide secure remote access to network resources, they differ fundamentally in their approach and capabilities.
- Security Model:
- VPNs: Traditional VPNs create a secure tunnel between the user’s device and the corporate network. Once connected, users often have broad access to the network, relying on perimeter defenses to keep threats out.
- ZTNA: In contrast, ZTNA assumes no user or device is trusted by default. It continuously verifies every access request, regardless of the user’s location, and provides access on a need-to-know basis.
- Access Control:
- VPNs: VPNs typically grant broad access to the network once a user is authenticated. This can be risky if an account is compromised, as attackers can potentially access a wide range of resources.
- ZTNA: ZTNA enforces strict access controls, granting users access only to specific resources required for their role. This minimizes the potential damage from compromised accounts.
- User Experience:
- VPNs: VPNs can be cumbersome for users, requiring manual connection and often slowing down network performance due to the overhead of tunneling.
- ZTNA: ZTNA offers a more seamless experience, often integrating with single sign-on (SSO) solutions and providing fast, direct access to resources without the need for a full network connection.
- Scalability:
- VPNs: Scaling VPNs can be challenging, as each new user increases the load on the VPN gateway, potentially impacting performance and requiring additional infrastructure.
- ZTNA: ZTNA solutions are designed to scale easily, accommodating growing numbers of users, devices, and resources without significant performance degradation.
ZTNA in Action: Real-World Use Cases
- Remote Workforce Security: With the rise of remote work, ZTNA ensures that employees can securely access corporate resources from any location without relying on traditional VPNs. For example, a sales representative can securely access customer relationship management (CRM) tools and company email from a home office, with access policies ensuring that sensitive financial data remains protected.
- Third-Party Access: Organizations can securely grant access to external partners, contractors, and vendors without exposing their entire network. Each third-party user is granted access only to the resources they need, based on strict verification policies. For instance, a freelance developer might access specific development environments without gaining access to HR or finance systems.
- Cloud Migration: As businesses migrate to the cloud, ZTNA provides secure access to cloud-based applications and services, ensuring that data remains protected in transit and at rest. This is particularly useful for companies using hybrid cloud environments, where seamless and secure access to both on-premises and cloud resources is essential.
Challenges and Considerations
While ZTNA offers numerous advantages, it’s not without challenges. Implementing a zero-trust model requires a shift in mindset and potentially significant changes to existing infrastructure. Organizations must carefully plan their transition to ensure that security policies are properly enforced without disrupting business operations.
- Complex Implementation: Moving to a zero-trust model can be complex, requiring a thorough understanding of the organization’s current infrastructure, applications, and access patterns.
- Performance Management: ZTNA solutions can generate a high volume of authentication and access requests, which may require robust performance management to prevent bottlenecks and ensure a smooth user experience.
- Cost Considerations: While ZTNA can reduce long-term security risks and costs, the initial investment in new technologies and training can be significant. Organizations must weigh these costs against the potential benefits.
- Cultural Change: Adopting a zero-trust approach often requires a cultural shift within the organization, as employees and management must understand and embrace new security practices.
Conclusion
Zero Trust Network Access represents a paradigm shift in network security, offering a more dynamic and resilient approach to protecting digital assets. As cyber threats continue to evolve, adopting a zero-trust model will be essential for organizations looking to safeguard their data and maintain a secure, agile IT environment. By embracing ZTNA, businesses can stay ahead of threats and ensure that their networks are secure, no matter where their users or resources are located.







Post Comment