cybersecurity
email
encryption
public key infrastructure
software defined radio
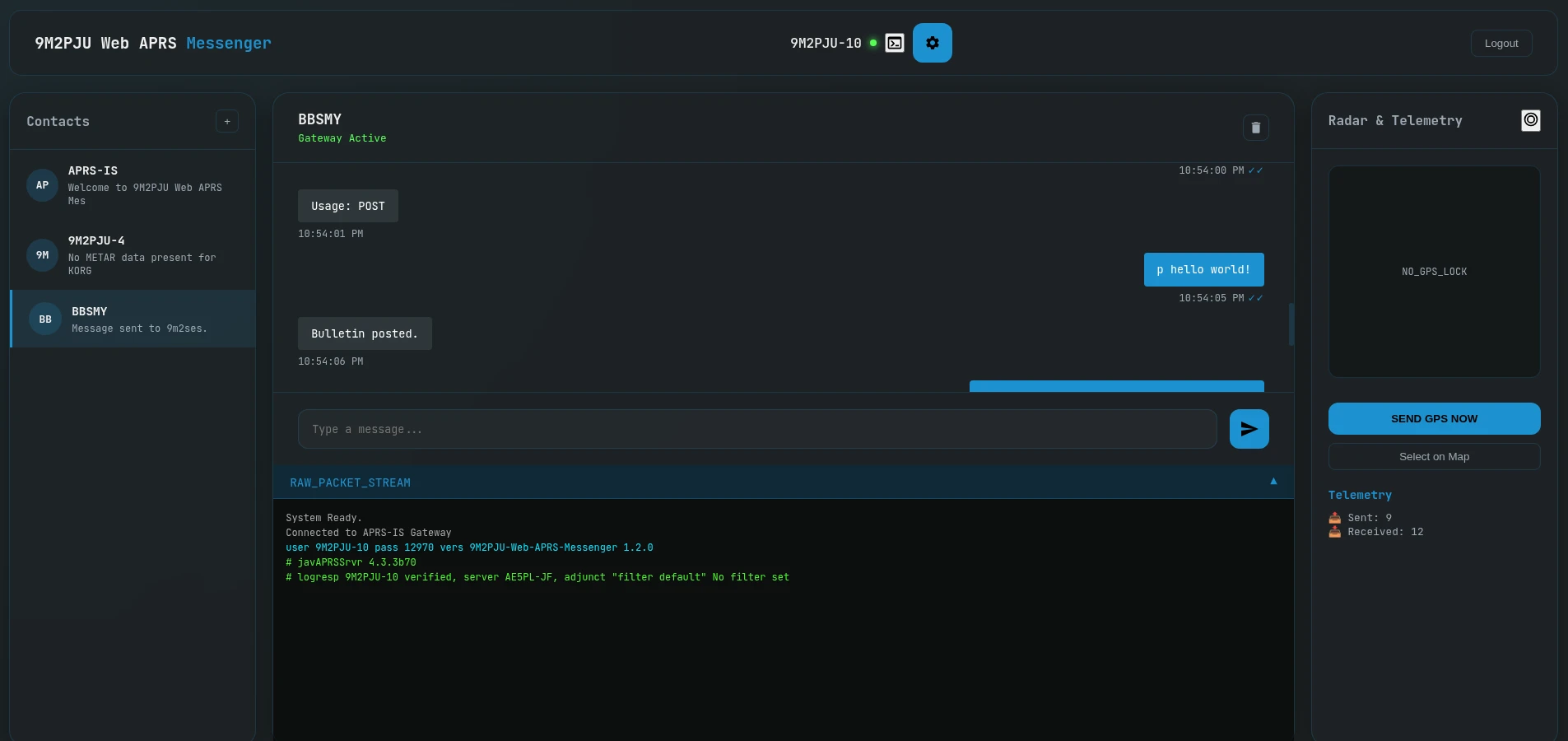
text messaging
vpn
zero trust
#DataProtection, AES, businesssecurity, comma-separated and without the "#" symbol: cybersecurity, cyberattack, databreach, datasecurity, defensesecurity, digitaltransformation, encryption, here are the hashtags from my previous response, infosec, militarytech, Okay, PGP, PKI, privacy, ransomware, SATCOM, sdr, securecommunications, SFTP, SMIME, technology, vpn, zerotrust
9M2PJU
0 Comments
Modern Types of Secured Communications: Protecting Data in the Digital Age
In today’s interconnected world, securing communication channels is more crucial than ever. With the rise of digital technologies, the risk of data breaches and unauthorized access to sensitive information has increased significantly. Modern secured communication methods are designed to protect data integrity, confidentiality, and availability, ensuring that only authorized parties can access and manipulate sensitive information. This blog post will delve into the various types of secured communication solutions available today, highlighting their features, benefits, and applications across different sectors.
Introduction to Secured Communication
Secured communication involves the use of encryption and other security measures to ensure that data transmitted between parties remains confidential and tamper-proof. This is achieved through various encryption techniques and protocols that convert readable data into unreadable ciphertext, which can only be deciphered by authorized recipients.
Types of Encryption
Encryption is the backbone of modern secured communication. There are two primary types of encryption: symmetric and asymmetric.
Symmetric Encryption
- Definition: Symmetric encryption uses a single shared key for both encryption and decryption. It is efficient and ideal for securing large volumes of data, especially when the parties involved can securely exchange the key beforehand.
- Applications: Symmetric encryption is widely used in applications where speed is crucial, such as encrypting data at rest. The Advanced Encryption Standard (AES) is a popular symmetric encryption algorithm known for its resistance to brute-force attacks.
- Challenges: The main challenge with symmetric encryption is securely distributing the shared key. If the key is compromised, the entire system is vulnerable to unauthorized access.
Asymmetric Encryption
- Definition: Asymmetric encryption employs a pair of mathematically linked keys: a public key for encryption and a private key for decryption. This method is particularly useful for securing communication channels like email and websites.
- Applications: Asymmetric encryption is ideal for scenarios where secure key exchange is difficult. It provides an additional layer of security by ensuring that only the intended recipient can decrypt the message.
- Benefits: Asymmetric encryption eliminates the need for direct key exchange, reducing the risks associated with key distribution. It also supports digital signatures, which verify the authenticity of messages.
Secure Communication Solutions
1. Secure Email
- Encryption Protocols: Secure email solutions often use encryption protocols like PGP (Pretty Good Privacy) or S/MIME (Secure/Multipurpose Internet Mail Extensions). These ensure that email messages are encrypted and can only be read by the intended recipients.
- Email Gateways: Secure email gateways filter incoming messages for spam and phishing attempts, protecting users from potential threats.
- Data Loss Prevention (DLP): DLP mechanisms prevent sensitive information from being leaked through email by filtering outgoing messages.
2. Secure File Transfer
- Protocols: Secure file transfer protocols such as SFTP (Secure File Transfer Protocol) and MFT (Managed File Transfer) ensure that large-scale data transfers are secure and encrypted.
- Features: These protocols offer additional security features like monitoring and reporting for compliance purposes.
3. Virtual Private Networks (VPNs)
- Functionality: VPNs provide secure, encrypted access to private networks over the internet. They are commonly used by remote workers to connect to company networks securely.
- Benefits: VPNs protect data privacy by encrypting all internet traffic, making it difficult for unauthorized parties to intercept or access sensitive information.
Advanced Secure Communication Technologies
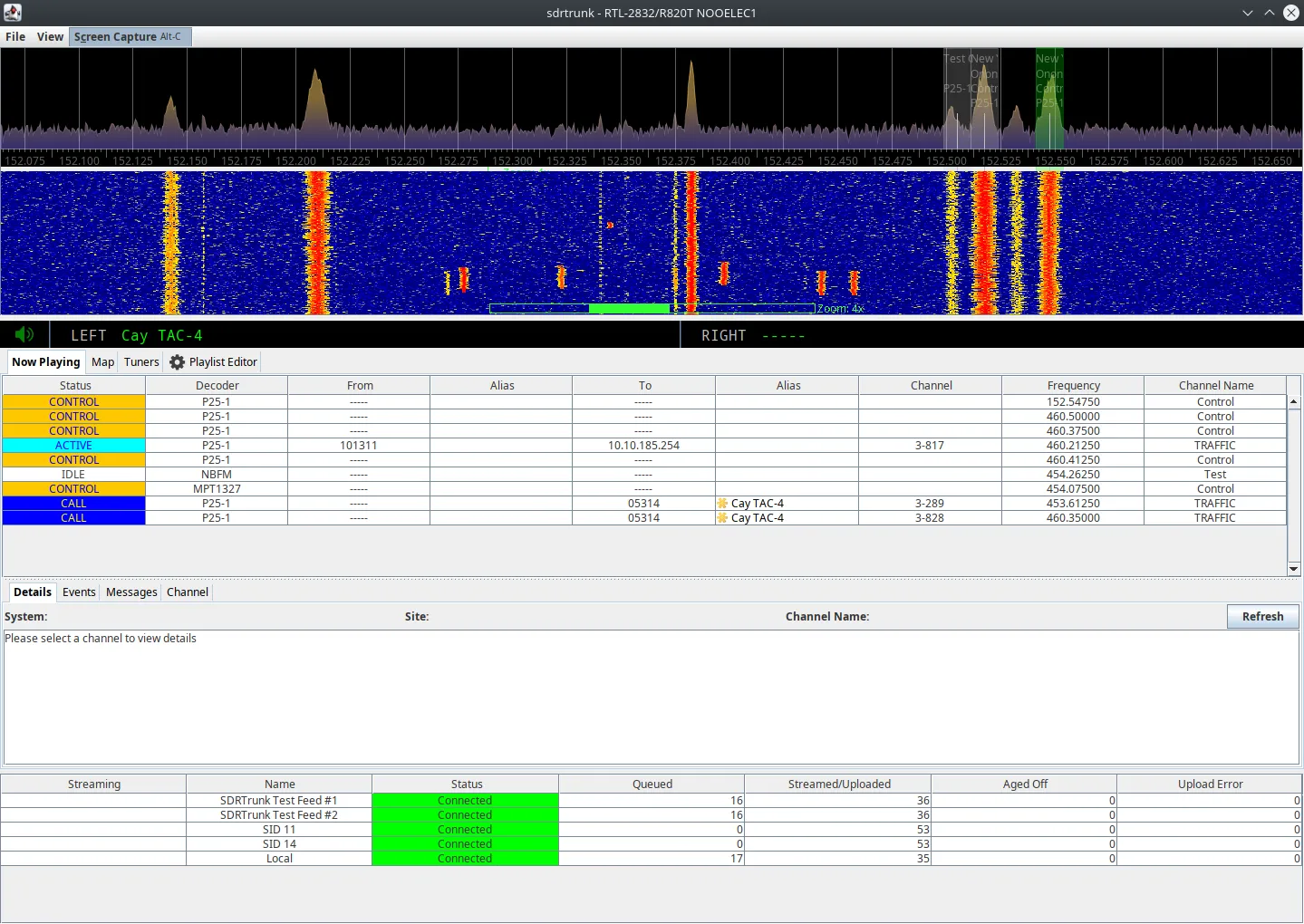
1. Software-Defined Radio (SDR)
- Application: SDR technology is used in military communication systems to ensure adaptability and security. It allows radios to adjust to new frequencies and encryption standards instantly.
- Benefits: SDR systems can change encryption algorithms and switch frequencies to maintain uninterrupted communication, even in hostile environments.
2. Public Key Infrastructure (PKI)
- Functionality: PKI uses cryptographic keys and digital certificates to authenticate users and devices, ensuring that only authorized parties can access sensitive data.
- Benefits: PKI protects data integrity by preventing message forgery and manipulation.
3. Zero Trust Architecture
- Concept: Zero trust security models assume that no user or device is inherently trustworthy. Each communication request is authenticated and encrypted, reducing the risk of unauthorized access.
- Benefits: This approach significantly decreases the risk of data breaches by continuously verifying the identity of users and devices.
Secure Communication in Defense and Military
In the defense sector, secure communication is critical for maintaining operational security and protecting sensitive information. Technologies like Secure Satellite Communications (SATCOM) and Software-Defined Radio (SDR) play key roles in ensuring that military communications remain secure and uninterrupted.
- Secure Satellite Communications (SATCOM): SATCOM systems use encrypted data transmission to prevent interception, enabling real-time communication over large distances.
- Secure Messaging Platforms: These platforms facilitate encrypted, real-time communication between military personnel, ensuring confidentiality and integrity of sensitive information.
Conclusion
Modern secured communication solutions are essential for protecting sensitive information in today’s digital landscape. By leveraging encryption techniques, secure protocols, and advanced technologies, organizations can ensure the confidentiality, integrity, and availability of their data. Whether it’s secure email, file transfer, or VPNs, these solutions are critical for compliance and trust-building in both business and defense sectors. As technology continues to evolve, the importance of secure communication will only grow, making it a cornerstone of digital security strategies worldwide.
Citations:
- https://pecb.com/article/encryption-during-communication
- https://guardiandigital.com/resources/blog/why-secure-communication-is-essential-for-business-success
- https://www.logic-fruit.com/blog/wireless-communication/communication-solutions-in-defense/
- https://blog.vandalog.com/2014/03/04/practical-tip-secure-communications/
- https://commsec.ie/secure-communications-the-cornerstone-of-compliance-in-the-digital-era/
- https://problogger.com/make-blog-cybersecurity-fortress/
- https://www.kiteworks.com/secure-file-sharing/ten-essential-capabilities-of-secure-communication-solutions/
- https://ashleyhughes.com/types-of-blog-posts/




Post Comment