aircrack-ng
cybersecurity
jammer
jamming
network
radio frequency
raspberry pi
security
wifi
access point security, aircrack-ng, captive portal, channel hopping, cybersecurity, deauth packets, deauthentication attack, ethical hacking, iot security, monitor mode, network analysis, network management, network protection, network security, network vulnerabilities, nodogsplash, packet sniffing, penetration testing, python scripting, raspberry pi, security research, security tools, soc, software defined radio, wifi jamming, wifi security, wireless deauth, wireless hacking, wireless monitoring, wireless networks
9M2PJU
0 Comments
Wi-Fi Jamming Using Raspberry Pi: Security Tools for Network Protection
In today’s interconnected world, wireless networks have become a critical part of our infrastructure. However, this ubiquity also creates security vulnerabilities that can be exploited. Understanding these vulnerabilities is essential for developing robust security measures. Let’s explore how a Raspberry Pi can be transformed into a wireless network security tool.
What is Wi-Fi Jamming?
Wi-Fi jamming is a technique that disrupts wireless networks by sending deauthentication packets to clients and access points. While this might sound malicious, it has legitimate applications in security testing, network management, and law enforcement.
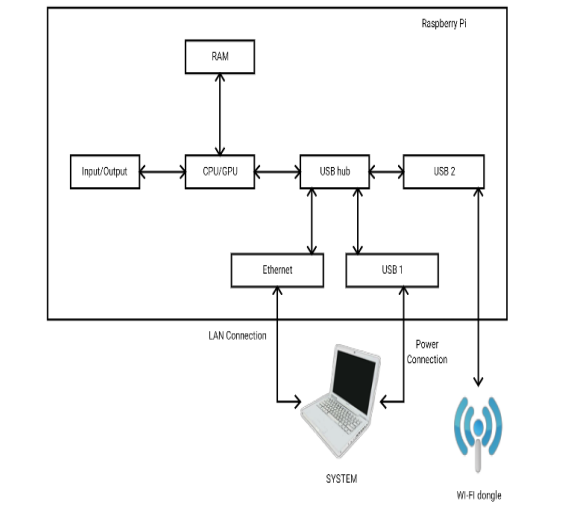
The Raspberry Pi Advantage
The Raspberry Pi is an ideal platform for network security tools due to its:
- Low cost and high portability
- Open hardware architecture
- Flexibility through its System on a Chip (SoC) design
- Compatibility with various wireless adapters
How the Jamming Process Works
The process involves several technical steps:
- Interface Selection: The system identifies the most powerful wireless interface and enables monitor mode.
- Channel Hopping: It sequentially scans channels 1-11, spending about 1 second on each to identify access points and connected clients.
- Deauthentication: After identifying targets, the system sends deauthentication packets that force clients to disconnect from their access points.
- Targeted Jamming: The tool can be configured to target specific devices or all devices connected to a particular access point.
Applications in Security
This type of tool has several legitimate uses:
- Law Enforcement: Originally developed for law enforcement to interrupt criminal communications
- Security Testing: Organizations can test their network resilience against deauthentication attacks
- Network Management: Institutions can control which devices connect to their networks
- Emergency Situations: Can be used to prevent remote triggering of explosive devices
Creating a Captive Portal
Beyond jamming, a Raspberry Pi can also be configured to create a captive portal – a landing page that appears when users connect to a network. This has applications in:
- User authentication
- Displaying network terms of service
- Controlled internet access
- Marketing and advertisements
Ethical Considerations
It’s crucial to note that unauthorized network disruption is illegal in most jurisdictions. These tools should only be used:
- On networks you own or have permission to test
- For legitimate security testing purposes
- In accordance with local laws and regulations
- With proper authorization from relevant authorities
Technical Implementation
The implementation involves several components:
- Aircrack-ng: A suite of tools for wireless network assessment
- Nodogsplash: Software for creating and managing captive portals
- Python: For scripting the core functionality
The system can be further enhanced with features like bandwidth control, domain restrictions, and packet filtering to create a comprehensive network management solution.
Conclusion
Wi-Fi jamming using Raspberry Pi represents a powerful tool for understanding and securing wireless networks. While its capabilities could be misused, its primary value lies in helping network administrators identify vulnerabilities and improve security posture. As IoT devices continue to proliferate, with estimates suggesting 30 billion connected objects by 2020, understanding these network security principles becomes increasingly important.
Remember, the goal of security research is always to build more robust systems, not to compromise legitimate networks.





Post Comment