cyber security
digital security
ESP development board
esp32
flipper zero
hacking
hobby
wifi security
Bad Bluetooth, BLE spammer, Bruce Firmware, BruceGotchi, captive portal, CC1101 module, cybersecurity gadgets, DIY hacking device, ESP32 hacking tool, ethical hacking, Flipper Zero alternative, IR cloner, LilyGO T-Deck, M5Stack Cardputer, M5StickC Plus 2, network audit, offensive security, open source firmware, penetration testing, pentesting hardware, replay attack, Sub-GHz RF analysis, wardriving, WiFi deauther
9M2PJU
0 Comments
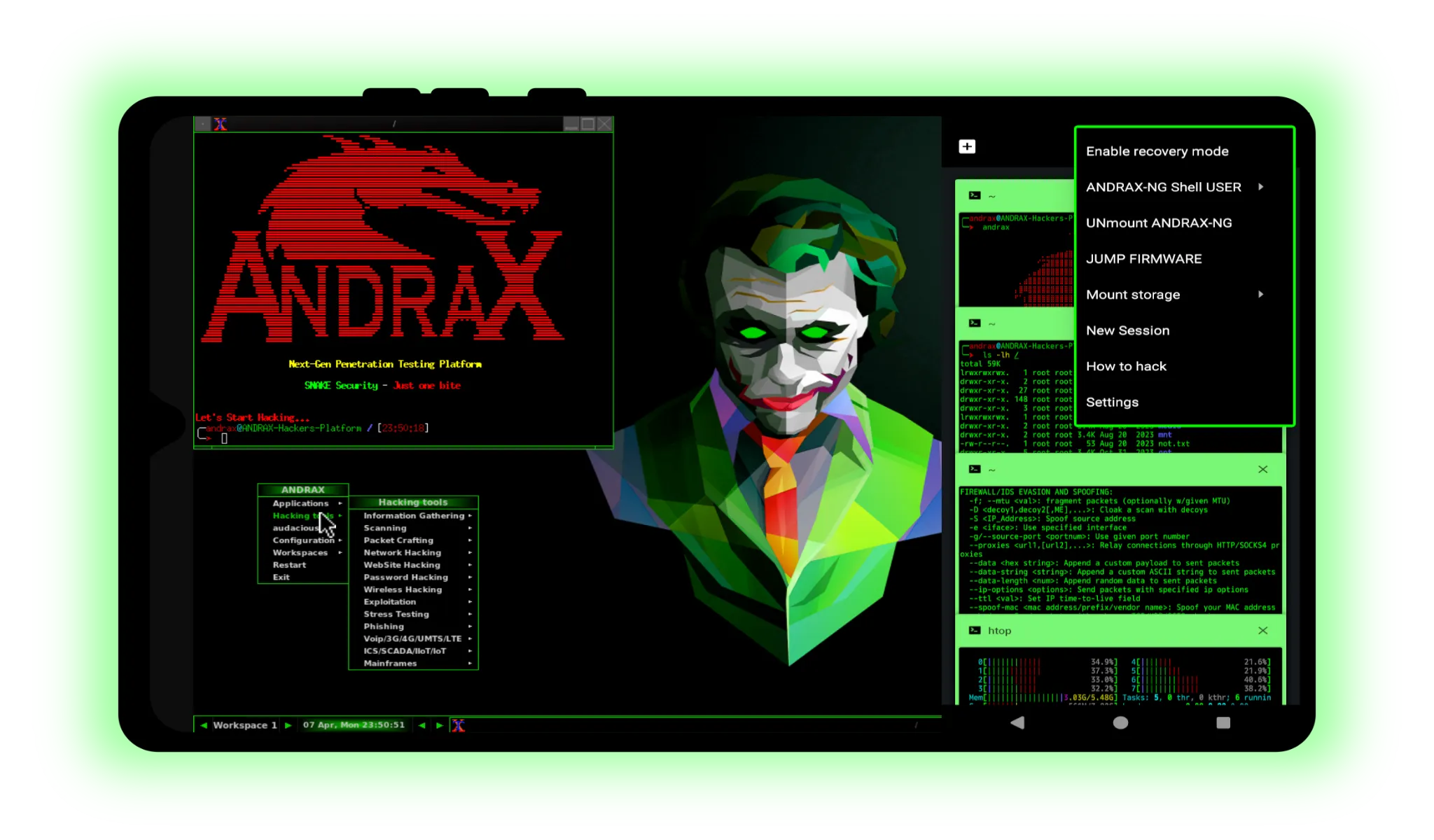
Unleash the Shark: Why Bruce is the Ultimate Budget “Flipper Zero” Killer
In the world of portable offensive security, the Flipper Zero has been the undisputed king. It’s sleek, it’s capable, and it’s… expensive. But what if I told you that the dusty ESP32 development board sitting in your drawer—or that $30 M5Stack Cardputer—could match, and in some cases exceed, the capabilities of the famous dolphin?
Enter Bruce.
Bruce is not just another firmware. It is an open-source, multi-functional “predatory” suite designed for the ESP32 ecosystem. It transforms modest hardware into a Swiss Army Knife for the digital age, capable of analyzing radio waves, auditing Wi-Fi, and testing Bluetooth resilience.
If you are a pen-tester, a hardware hacker, or just curious about the invisible signals around you, here is why Bruce should be your next flash.
📡 The Core Pillars of Bruce
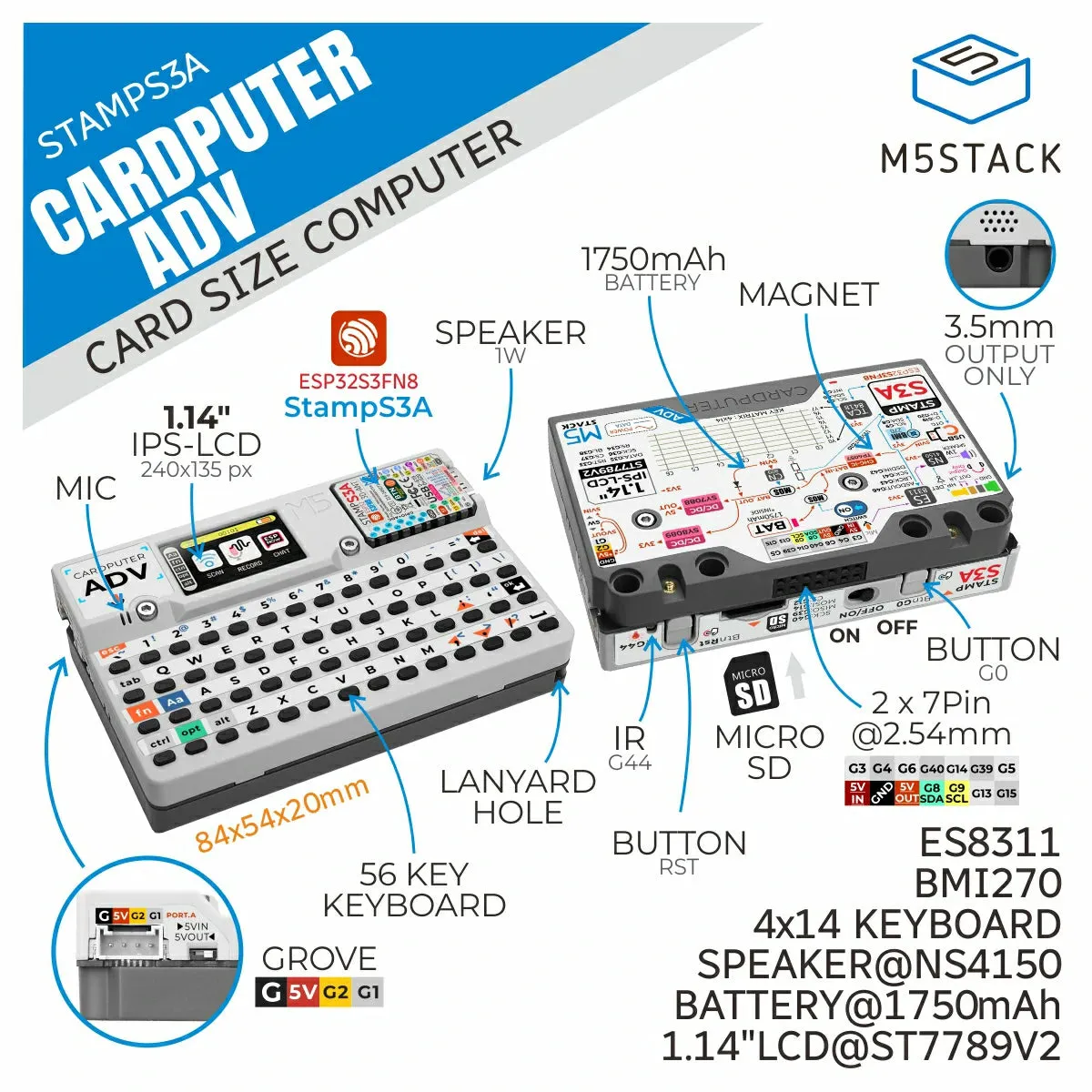
Bruce is built around modularity. Depending on your hardware (M5Stack Cardputer, M5StickC Plus 2, or LilyGO T-Deck), it unlocks different superpowers.
1. The Sub-GHz RF Suite (Radio Frequency)
This is where Bruce truly shines, especially if you attach a CC1101 module. While most basic firmwares only listen, Bruce allows you to interact with the Sub-GHz world (300MHz–928MHz).
- Spectrum Analysis: Visualize the invisible. Bruce renders a live waveform of radio traffic nearby. It’s incredibly useful for spotting “noisy” devices or identifying the frequency of a mystery remote.
- Universal Remote (Replay Attacks): Bruce can listen for a signal (like a gate opener or a doorbell), save it, and replay it.
- Pro Tip: It supports RAW Recording. Even if Bruce doesn’t “understand” the protocol, it can clone the exact timing of the signal pulses to replay it later.
- The Jammer: Need to test how a security system handles interference? Bruce can broadcast “noise” to block specific frequencies (like 433MHz), effectively deafening receivers in the area. Note: Use this strictly for testing shielded equipment you own.
2. Wi-Fi Warfare
Bruce leverages the ESP32’s native Wi-Fi radio for advanced network auditing. It goes far beyond a simple “scanner.”
- Beacon Spam: Create hundreds of fake Wi-Fi networks (SSIDs) with funny or confused names. This is harmless but demonstrates how easily devices can be cluttered.
- Deauthentication (Deauth): The classic “kick” attack. Bruce can send dissociation frames to disconnect devices from a router. This is vital for testing if your home network is vulnerable to forced disconnects.
- Evil Portal: Bruce can host a “Captive Portal”—a fake login page. When a target connects to Bruce’s open Wi-Fi, they are presented with a login screen (e.g., “Firmware Update Required”). Any credentials entered are captured to the SD card.
3. Bluetooth Low Energy (BLE) Assault
Modern devices are chatty. Bruce exploits this.
- BLE Spam (The “Sour Apple”): By broadcasting specifically crafted BLE packets, Bruce can confuse nearby iOS, Android, and Windows devices, causing them to pop up “Connect New Device” notifications endlessly. It’s a powerful demo of how annoying Bluetooth vulnerabilities can be.
- Bad BLE (Wireless Ducky): Connect Bruce to a PC via Bluetooth, and it acts as a keyboard. You can then run Ducky Scripts remotely—automating keystrokes to open terminals, type commands, or launch websites in seconds.
🛠️ The Ecosystem: “BruceGotchi” and More
Bruce isn’t just a list of attacks; it’s a platform.
The BruceGotchi
Security work can be dry, so Bruce includes a “Pwnagotchi-style” companion. This digital pet lives on your screen and reacts to the environment.
- Hungry? It feeds on EAPOL packets (Wi-Fi handshakes).
- Bored? It gets sad if there are no signals around.
- Personality: It gives you a visual status report of your wardriving without needing to read lines of text.
The Web Interface
Unlike many tools where you have to constantly pop out the SD card to check logs, Bruce hosts its own web server. You can connect to Bruce from your phone’s browser to:
- Download captured signals/handshakes.
- Upload new scripts or update firmware.
- Manage your file system wirelessly.
🧐 Real Talk: Limitations & Ethics
It is important to be realistic. Bruce is powerful, but it has limits:
- Rolling Codes: Like the Flipper Zero, Bruce cannot magically bypass “Rolling Code” encryption found on modern cars. If you clone your car key, the clone likely won’t work (or will only work once).
- Hardware Required: For the best experience (especially RF), you need an external CC1101 module. The built-in antennas on M5Stack devices are often too weak for long-range work.
⚠️ The Golden Rule:
Bruce is a tool for Red Teaming and Education.
- Do not jam public frequencies.
- Do not deauth your neighbors.
- Do not capture credentials from people who haven’t given you permission.
- Unauthorized use of these features is illegal.
🚀 Conclusion: Why You Should Flash Bruce Today
If you love the idea of the Flipper Zero but hate the price tag, or if you simply enjoy the freedom of open-source hardware, Bruce is a no-brainer. It breathes new life into cheap microcontrollers and puts a professional-grade pentesting suite in your pocket.
Whether you are debugging your garage door opener or learning how Wi-Fi handshakes work, Bruce is the best teacher you can ask for.




Post Comment