BYOD
cyber
cybersecurity
security
zero trust
byod, cloudsecurity, cyberdefense, cyberresilience, cybersecurity, cyberthreats, datasecurity, digitaltransformation, endpointsecurity, iam, incidentresponse, informationsecurity, infosec, leastprivilege, mfa, microsegmentation, multifactorauthentication, networksecurity, remotework, sase, securityarchitecture, securityawareness, securityoperations, securitypolicy, securitystrategy, threatdetection, zerotrust
9M2PJU
0 Comments
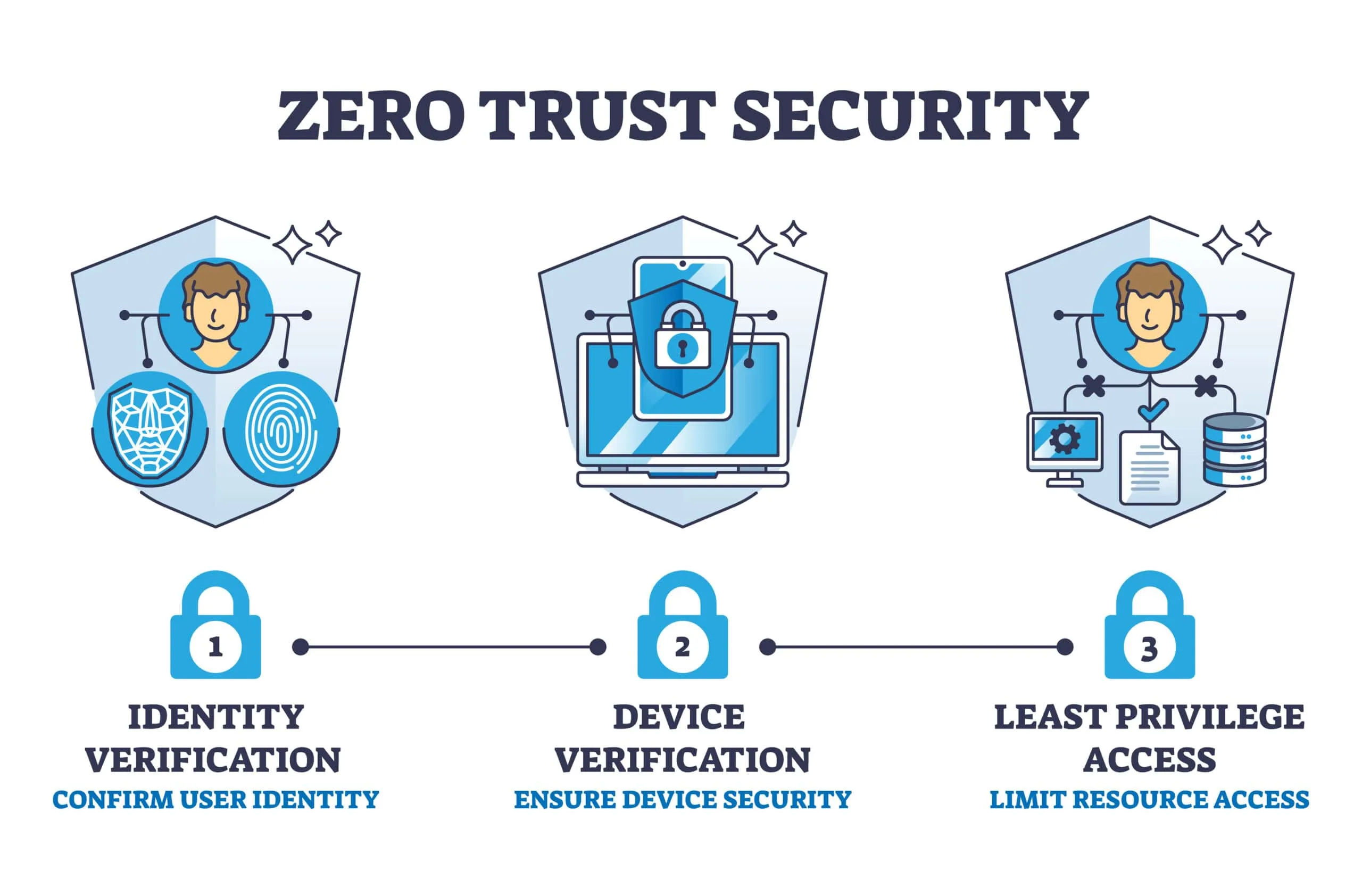
Introduction to Zero Trust Architecture
In today’s digital landscape, security is a paramount concern for organizations worldwide. Traditional security models often rely on a “castle-and-moat” approach, where everything inside the network is considered trusted. However, with the rise of cloud computing, remote work, and bring-your-own-device (BYOD) policies, this model has become increasingly outdated. This is where Zero Trust Architecture (ZTA) comes into play, offering a modern security framework that assumes no user or device is trustworthy until verified.
History and Origin
The concept of Zero Trust was first coined by Stephen Paul Marsh in his 1994 doctoral thesis at the University of Stirling. Marsh explored trust as a finite, mathematically describable concept that transcends human factors like morality and ethics. However, it wasn’t until 2010 that the term gained widespread recognition, thanks to analyst John Kindervag of Forrester Research. Kindervag popularized the Zero Trust model as a stricter cybersecurity approach, emphasizing the need for continuous verification and segmentation within corporate networks.
The Jericho Forum, an international security consortium, played a significant role in the evolution of Zero Trust by highlighting the challenges of defining organizational IT boundaries and promoting the concept of “de-perimeterization” in the early 2000s. Google’s BeyondCorp initiative, launched after the Operation Aurora attack in 2009, was one of the first large-scale implementations of Zero Trust, further solidifying its place in modern security strategies.
Applications of Zero Trust Architecture
Zero Trust Architecture is applied in various ways to enhance security across different domains:
- Zero Trust Network Access (ZTNA): This approach replaces traditional VPNs by verifying user and device identities before granting network access. It minimizes the attack surface by limiting lateral movement within the network.
- Zero Trust Application Access (ZTAA): Beyond securing networks, ZTAA extends Zero Trust principles to protect applications. It ensures that access to applications is granted only after thorough verification, safeguarding against threats even if the network is compromised.
- Zero Trust Access: This is the overarching model that integrates both ZTNA and ZTAA, providing end-to-end security across networks and applications. It emphasizes identity-based security, ensuring that all entities—users, devices, and data—are continuously validated.
Benefits of Zero Trust Architecture
Implementing Zero Trust Architecture offers several key benefits:
- Minimized Risk: By continuously verifying identities and permissions, Zero Trust reduces the risk of security breaches. It eliminates over-provisioned access and ensures that only necessary permissions are granted.
- Enhanced Security Monitoring: Zero Trust involves comprehensive monitoring for malicious activity, which helps in early detection and response to potential threats.
- Improved Compliance: With its focus on granular access control and continuous verification, Zero Trust can help organizations meet stringent regulatory requirements more effectively.
- Adaptability to Modern Work Environments: Zero Trust is particularly beneficial in today’s cloud-centric and remote work environments, where traditional perimeter security models are insufficient.
- Reduced Lateral Movement: By limiting access to only what is necessary for a task, Zero Trust prevents attackers from moving laterally within the network, thereby protecting sensitive data.
Conclusion
Zero Trust Architecture represents a significant shift in how organizations approach cybersecurity. By assuming that no user or device is inherently trustworthy, Zero Trust provides a robust framework for protecting digital assets in an increasingly complex and interconnected world. As technology continues to evolve, the adoption of Zero Trust principles will remain crucial for maintaining robust security postures across industries.





Post Comment