amateur radio
cybersecurity
firmware
firmware analysis
free software
ham radio
malware analysis
open source
reverse engineering
amateur radio, analysis, binwalk, cybersecurity, digital forensics, embedded systems, firmware, firmware extraction, hacking, ham radio, Linux Tools, open source, radio hacking, reverse engineering, rf analysis, rtl-sdr, rustlang, sdr, security, signal processing, software defined radio
9M2PJU
0 Comments
Unlocking Firmware Secrets with Binwalk: A Powerful Tool for Amateur Radio Enthusiasts
As technology evolves, amateur radio operators are increasingly exploring software-defined radios (SDRs), digital modes, and embedded systems. Many modern transceivers, handheld radios, and digital devices rely on firmware to control their functionality. Understanding and modifying this firmware can open new possibilities, from enabling hidden features to customizing device behavior. This is where Binwalk, a powerful firmware analysis tool, comes in.
What is Binwalk?
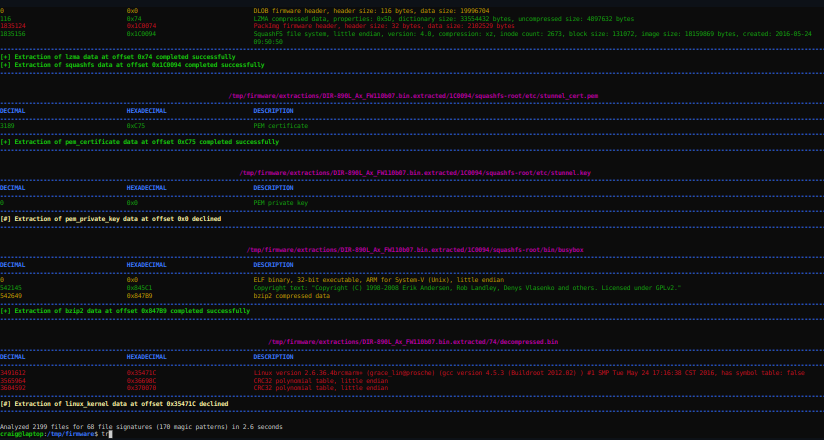
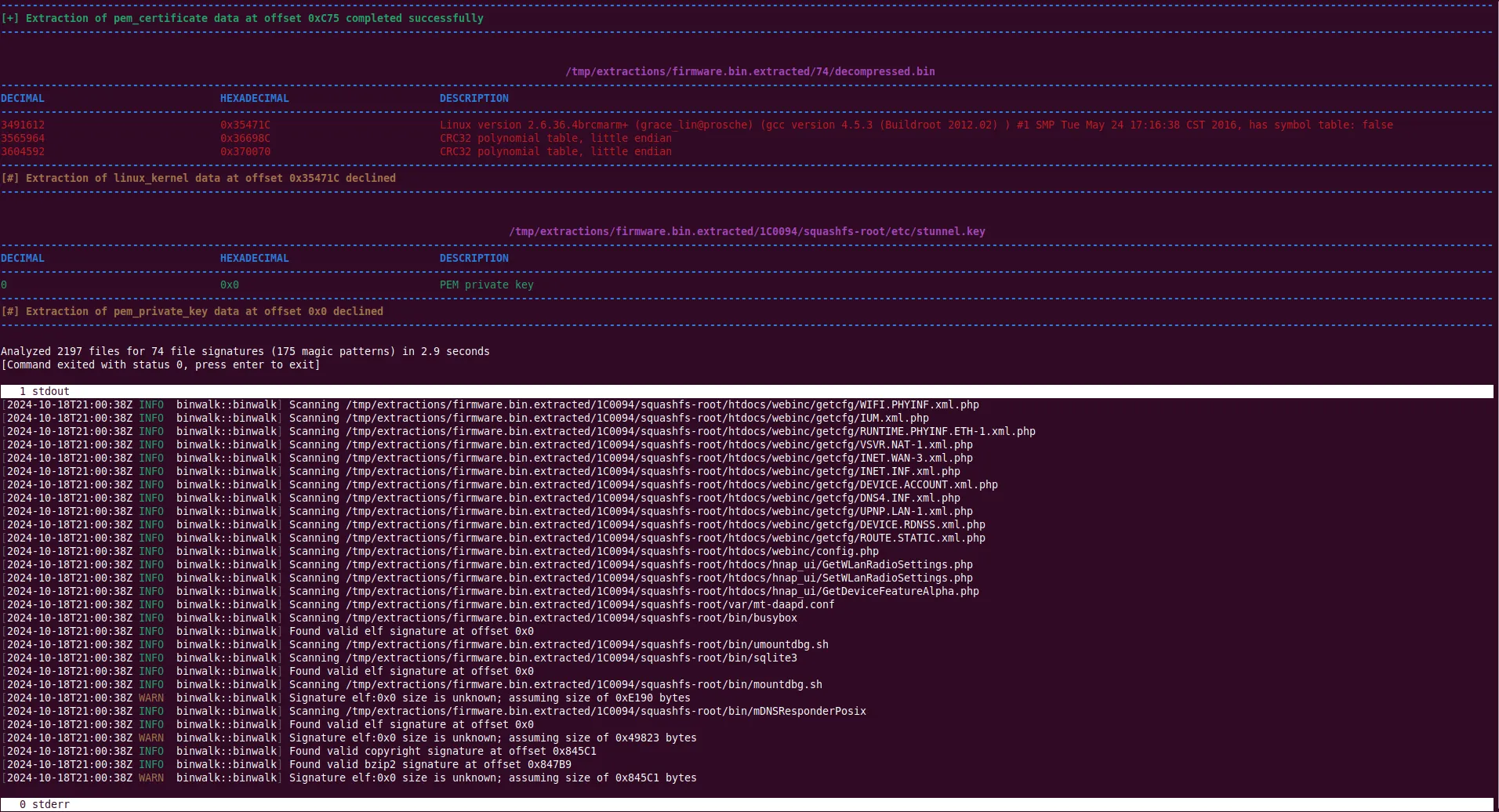
Binwalk is an open-source tool designed to analyze, identify, and extract data from binary files, particularly firmware images. Originally written in Python, the latest version, Binwalk v3, has been rewritten in Rust for improved speed and accuracy. It is widely used in cybersecurity, reverse engineering, and embedded system development, making it an invaluable tool for amateur radio enthusiasts who want to delve into the internals of their radio equipment.
Why is Binwalk Useful for Amateur Radio?
Many modern radios, such as digital handheld transceivers (D-STAR, DMR, and System Fusion), SDRs, and repeater controllers, rely on firmware that can be updated or customized. With Binwalk, radio enthusiasts can:
- Extract hidden files from firmware updates to analyze their structure.
- Identify encryption or compression methods used in firmware storage.
- Modify radio parameters (when legally permitted) to enable additional features.
- Understand proprietary communication protocols for interoperability with other devices.
Installing Binwalk
Binwalk can be installed in multiple ways:
- Using Docker:
docker pull binwalk/binwalk - Using Rust Package Manager (Cargo):
cargo install binwalk - Building from source:
git clone https://github.com/ReFirmLabs/binwalk.git cd binwalk cargo build --release
Using Binwalk for Firmware Analysis
Binwalk is simple to use and provides detailed insights into firmware structures. Here are some essential commands:
- Scanning a firmware file:
binwalk firmware.binThis scans the file and lists detected signatures, file types, and embedded data. - Extracting embedded files:
binwalk -e firmware.binThis automatically extracts any detected files, such as compressed archives or filesystem images. - Recursively extracting files:
binwalk -Me firmware.binThis scans and extracts files recursively, useful for analyzing deeply nested firmware structures. - Excluding specific signatures:
binwalk --exclude=jpeg,png,gif firmware.binThis avoids extracting unwanted files, like common image formats, to focus on relevant data. - Carving out file data:
binwalk --carve firmware.binThis extracts sections of a file, even if they do not match known file signatures, useful for uncovering hidden data.
Practical Applications in Amateur Radio
- Analyzing Radio Firmware: Operators can extract firmware from radio devices to study their structure and identify possible modifications.
- Understanding Digital Modes: By examining protocol implementations in firmware, hams can better understand how digital voice and data modes work.
- Customizing SDR Hardware: SDR users can analyze firmware updates for potential improvements or debugging purposes.
- Recovering Corrupt Firmware: If a radio firmware update fails, Binwalk can help extract essential components for recovery.
Conclusion
Binwalk v3 brings significant improvements in firmware analysis, making it faster and more accurate than ever before. For amateur radio enthusiasts interested in exploring the firmware of their devices, Binwalk offers a powerful and accessible way to analyze and extract valuable information. Whether you’re reverse engineering digital modes, studying SDR firmware, or recovering lost data, Binwalk is an indispensable tool for the modern ham radio operator.
Learn more at https://github.com/ReFirmLabs/binwalk




Post Comment