computer
cyber security
information technologies
password
bcrypt vs md5, brute force attack, cryptographic security, cyber attack methods, cybersecurity malaysia, hash chain, hash functions, hashcat, how rainbow tables work, key stretching, legacy systems security, md5 cracking, ntlm hash, ophcrack, password cracking, password hashing, password protection best practices, password salting, password security, rainbow table attack prevention, rainbow tables, rainbowcrack, reduction function, salted hashes, sha1 cracking, time memory tradeoff
9M2PJU
0 Comments
Understanding Rainbow Tables: How Hackers Crack Password Hashes (and How to Defend Yourself)
In cybersecurity, passwords are often the first and most important line of defense. Yet, attackers continue to find ways to break weak or poorly-protected credentials. One of the most powerful techniques used in password cracking—especially in older systems—is the rainbow table attack.
If you have ever wondered how rainbow tables work, why they were so popular, and how modern security protects against them, this article breaks it down in a practical, easy-to-understand way.
What Exactly Is a Rainbow Table?
A rainbow table is a precomputed lookup table used to reverse cryptographic hash functions. Instead of guessing every password and hashing it in real-time (brute force), attackers generate massive tables of password–hash pairs in advance.
Once they have these tables, they can take a leaked password hash and instantly look up which password produced it.
This method became famous because it dramatically speeds up password cracking while requiring less storage than a fully precomputed dictionary.
How Password Hashing Works
Websites and operating systems usually store passwords as hashes, not plain text. A hash is a one-way mathematical function such as:
- MD5
- SHA-1
- NTLM
- SHA-256
When you log in, the system hashes the password you enter and compares it to the stored hash.
Hashing is one-way. You should not be able to “reverse” a hash. But rainbow tables exploit a weakness: hashes of the same password always look the same.
The Problem Rainbow Tables Exploit
If a system stores unsalted hashes (older Windows systems are notorious for this), two users with the same password will have identical hash values.
This allows attackers to precompute huge collections of:
password → hash
Then, when a database is breached, they only need to search for the hash inside their rainbow table.
No guessing. No brute force. Just a massive lookup.
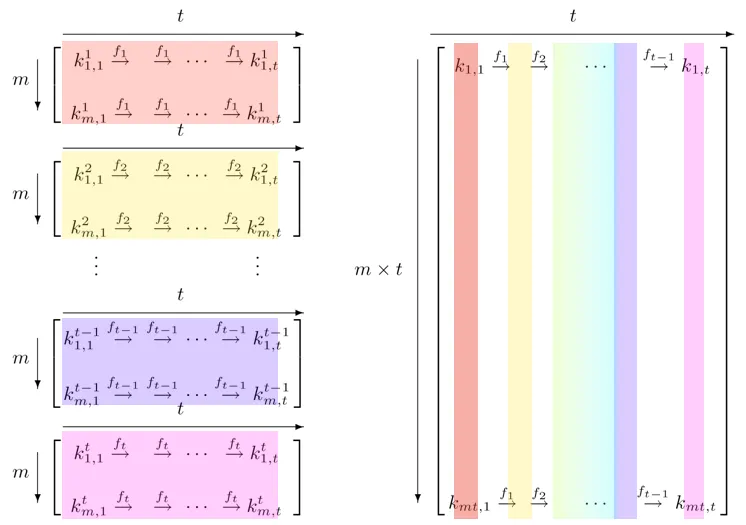
How Rainbow Tables Actually Work
A full dictionary of every password and its hash would require enormous storage. To reduce space, rainbow tables use hash chains and reduction functions.
Here is the simplified idea:
- Start with a password (e.g., “aaaaaa”).
- Hash it →
281DAF40 - “Reduce” the hash back into another password-like value →
sgfnyd - Hash again
- Reduce again
- Continue for k steps
Only the first and last password in the chain are stored. Thousands or millions of these chains form a rainbow table.
When cracking, attackers run the same hash-reduce sequence and check if the final value matches one of the endpoints in the table.
If it does, they regenerate the chain and recover the password.
This technique is extremely efficient and helped tools like Ophcrack and RainbowCrack become famous.
Why They’re Called “Rainbow” Tables
Instead of using one reduction function, modern rainbow tables use many different reduction functions, one for each step in the chain.
If each reduction function is visualised using a different colour, the rows look like a rainbow—hence the name.
This innovation massively reduces chain collisions and increases cracking success.
Are Rainbow Tables Still Dangerous Today?
Yes and no.
Rainbow tables are still useful against:
- Old Windows LM/NTLM hashes
- Systems with unsalted MD5 or SHA-1
- Poorly-configured applications
- IoT devices or routers using outdated hashing
However, modern security practices make rainbow tables nearly useless.
Why Rainbow Tables Are Becoming Obsolete
1. Salting
A salt is a random value added to every password before hashing.
hash(password + salt)
Even if two users have the same password, their salted hashes become completely different.
To attack salted passwords, hackers would need:
one rainbow table per salt
For large salts (e.g., 128 bits), this is impossible.
2. Key Stretching
Modern algorithms slow down hashing by design:
- bcrypt
- PBKDF2
- scrypt
- Argon2
These force attackers to spend more computation time per guess, making rainbow tables impractical.
3. GPU Acceleration Favors Brute Force Over Rainbow Tables
With modern GPUs, raw brute-force or dictionary attacks (Hashcat, John the Ripper) are often faster than building rainbow tables from scratch.
When Rainbow Tables Still Matter
Despite modern defenses, rainbow tables remain relevant for:
- Legacy systems
- Old Windows domains using LM/NTLM hashes
- Forensic work on outdated hardware
- Educational demonstrations
- Recovering weak passwords from old databases
If a system still uses unsalted MD5, SHA-1, or NTLM, rainbow tables can break:
- 7-character LM passwords in seconds
- 8–9 character NTLM hashes fairly quickly
- Simple alphanumeric passwords near-instantly
How to Defend Your Systems
To fully eliminate rainbow table risks, ensure your environment uses:
1. Strong password hashing
Use these:
- bcrypt
- PBKDF2
- scrypt
- Argon2
Avoid:
- plain MD5
- plain SHA-1
- NTLM
- LM hash (always disable it)
2. Unique per-user salts
Most modern frameworks implement these automatically.
3. Long passwords or passphrases
Rainbow tables rarely go beyond 14 characters due to storage cost.
4. Two-factor authentication
Even a cracked password becomes less useful.
5. Regular security audits
Legacy systems often hide weak hashing methods.
Final Thoughts
Rainbow tables are a clever and historically important technique in password cracking. They represent a massive time-memory tradeoff that allowed attackers to invert hashes far faster than brute-force methods.
However, with modern salting and slow hash functions, rainbow tables have become less effective, though not entirely obsolete—especially for old systems still running weak hashing algorithms.
If you manage servers, applications, or authentication systems in Malaysia or anywhere else, ensure that your environments use salted, stretched, modern password hashing to stay ahead of attackers.




Post Comment