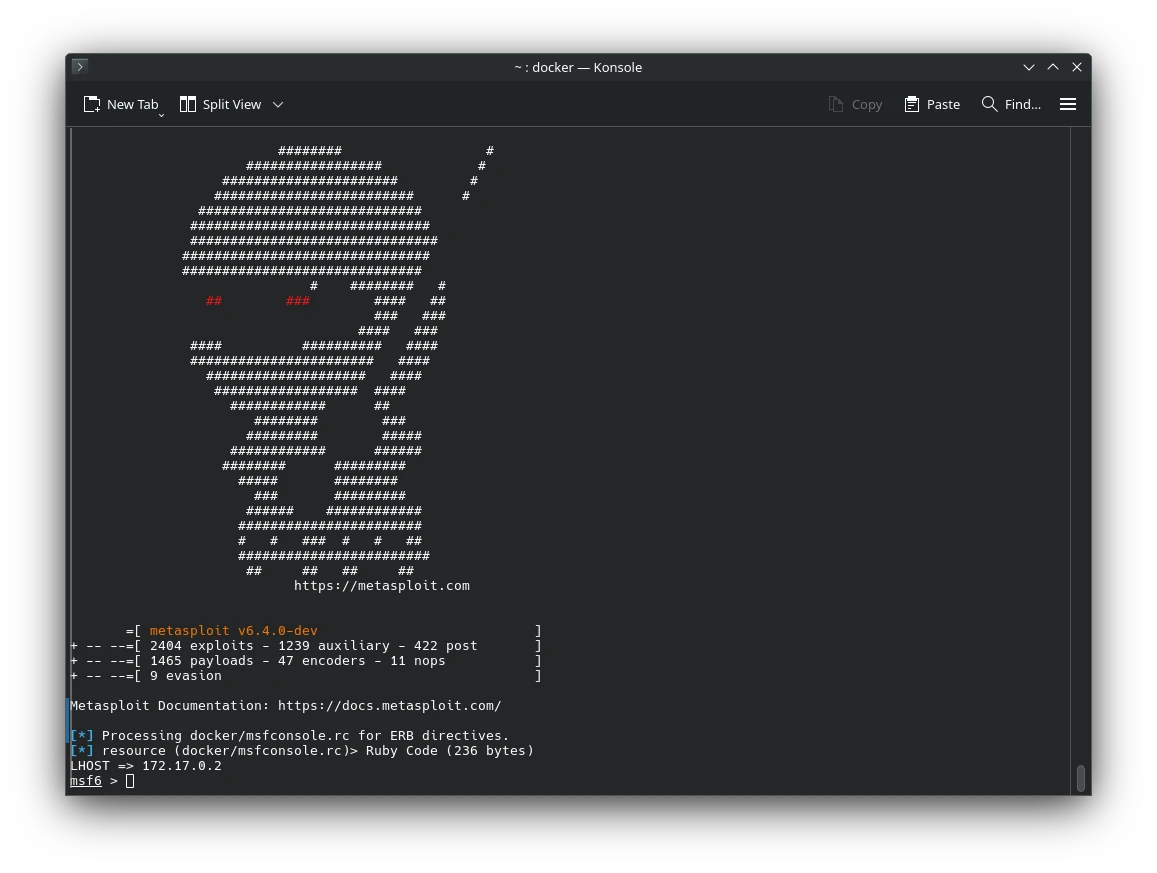
Armitage + Metasploit in Docker
If you're into penetration testing, you've probably used Metasploit — the Swiss Army knife of…
Hacking Databases with sqlmap in Docker
When it comes to finding and exploiting SQL injection vulnerabilities, few tools are as powerful—or…
Deploying Tenable Nessus in Docker: Fast, Portable Vulnerability Scanning
Tenable Nessus has long been a trusted tool in the cybersecurity world for identifying vulnerabilities,…
Penetration Testing with Metasploit Docker Image
🛠️ What is Metasploit Framework? The Metasploit Framework is one of the most powerful and…
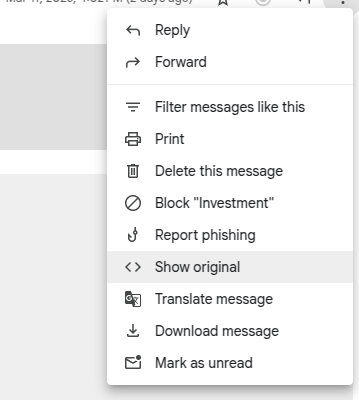
How to Recognize Spam Emails Using Gmail’s Show Original Feature
In today's digital world, spam emails have become increasingly sophisticated, making them harder to identify…
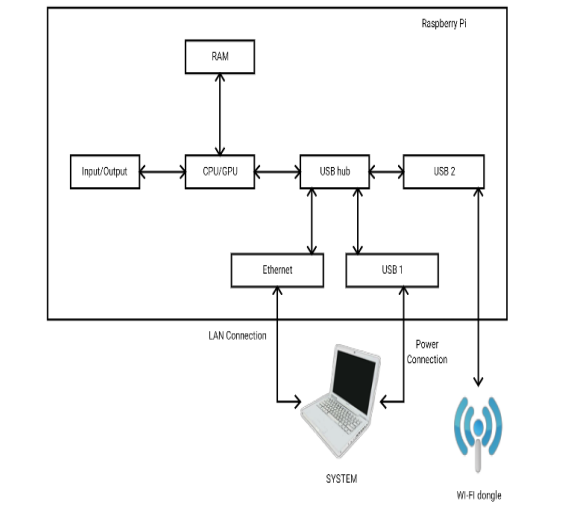
Wi-Fi Jamming Using Raspberry Pi: Security Tools for Network Protection
In today's interconnected world, wireless networks have become a critical part of our infrastructure. However,…
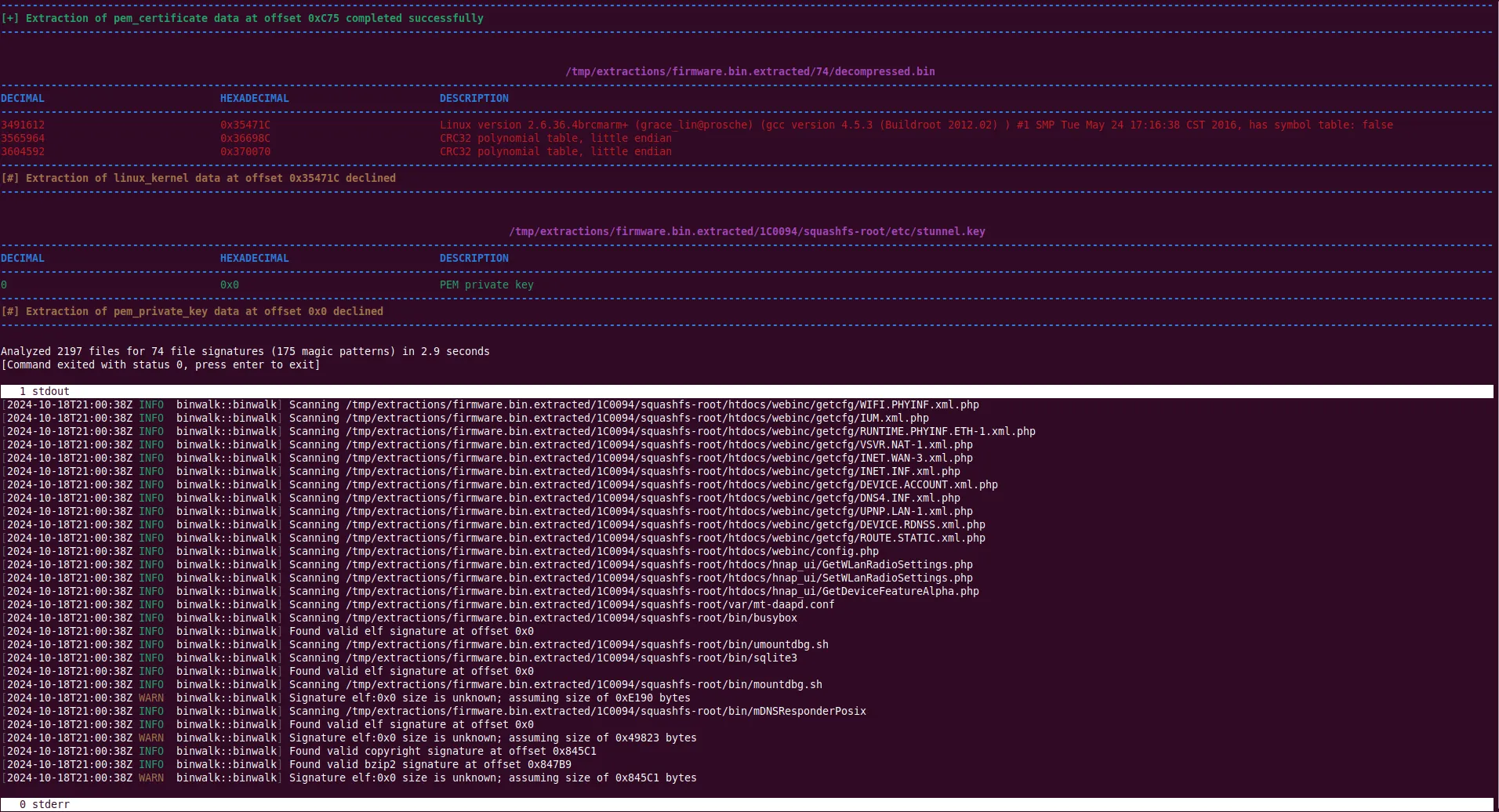
Unlocking Firmware Secrets with Binwalk: A Powerful Tool for Amateur Radio Enthusiasts
As technology evolves, amateur radio operators are increasingly exploring software-defined radios (SDRs), digital modes, and…
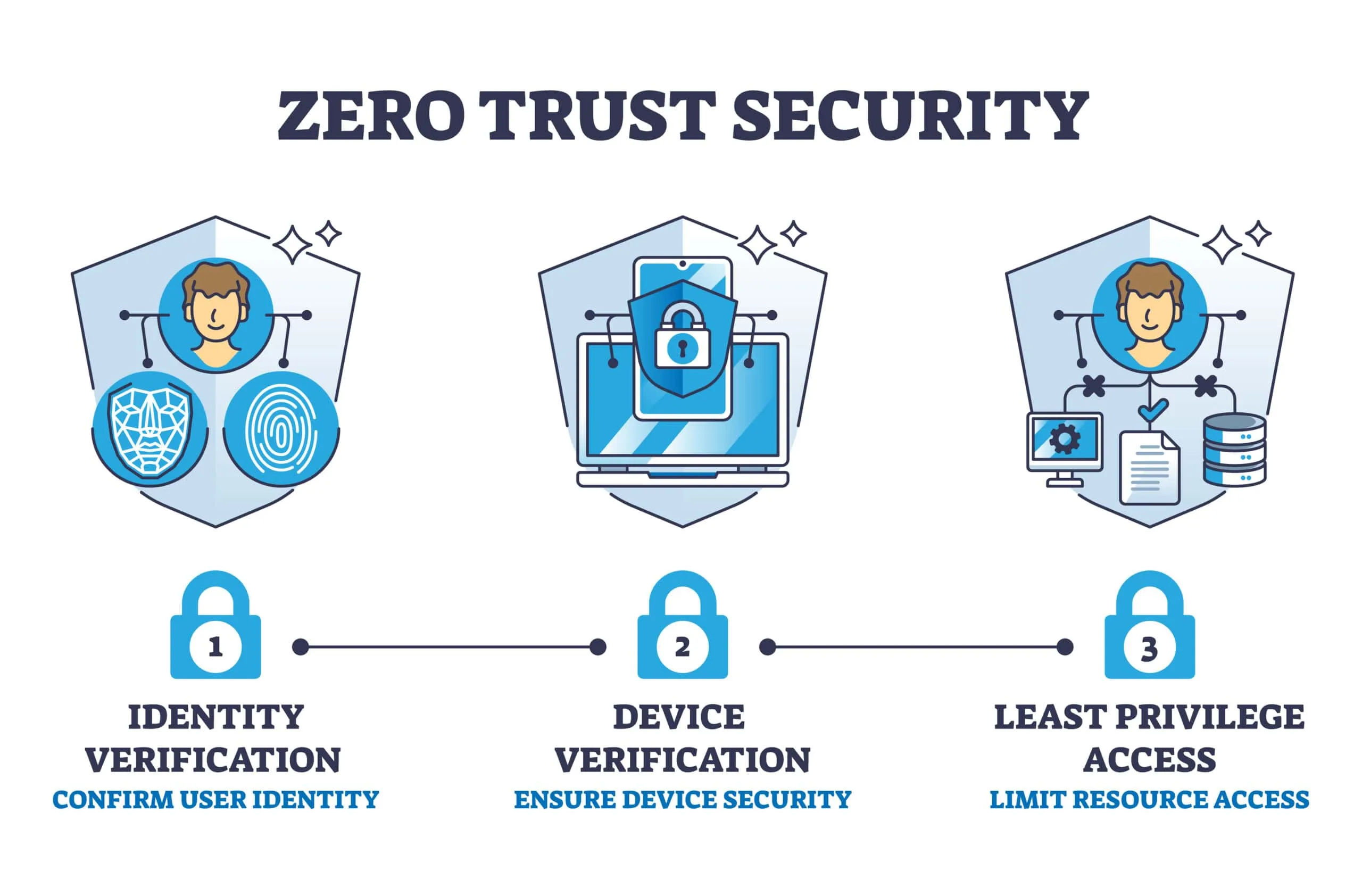
Introduction to Zero Trust Architecture
In today's digital landscape, security is a paramount concern for organizations worldwide. Traditional security models…
Modern Types of Secured Communications: Protecting Data in the Digital Age
In today's interconnected world, securing communication channels is more crucial than ever. With the rise…
The Rise of PCMCIA Cards as Cryptographic Security Modules in the 1990s
In the early 1990s, the emergence of personal computers (PCs) and laptops began to revolutionize…
The Evolution of CyberSecurity Malaysia: A Journey from MyCERT to National Guardian
Our journey in safeguarding Malaysia's cyberspace began on January 13, 1997, with the establishment of…
The Tor Project: Ensuring Anonymity Online
In an age where privacy and online security are paramount, the Tor Project stands as…
Enhance Your Website Security with Wordfence: A Comprehensive WordPress Security Plugin
In today’s digital landscape, securing your website is paramount. As cyber threats become more sophisticated,…
Unleashing CyberChef: Your Ultimate Cybersecurity Swiss Army Knife
In the realm of cybersecurity, having the right tools at your disposal can mean the…