VeraCrypt: An Open-Source Encryption Solution for Secure Handling of Sensitive Data in Business, Law Enforcement and Military Operations
In the digital age, the security of sensitive data is no longer a niche concern…
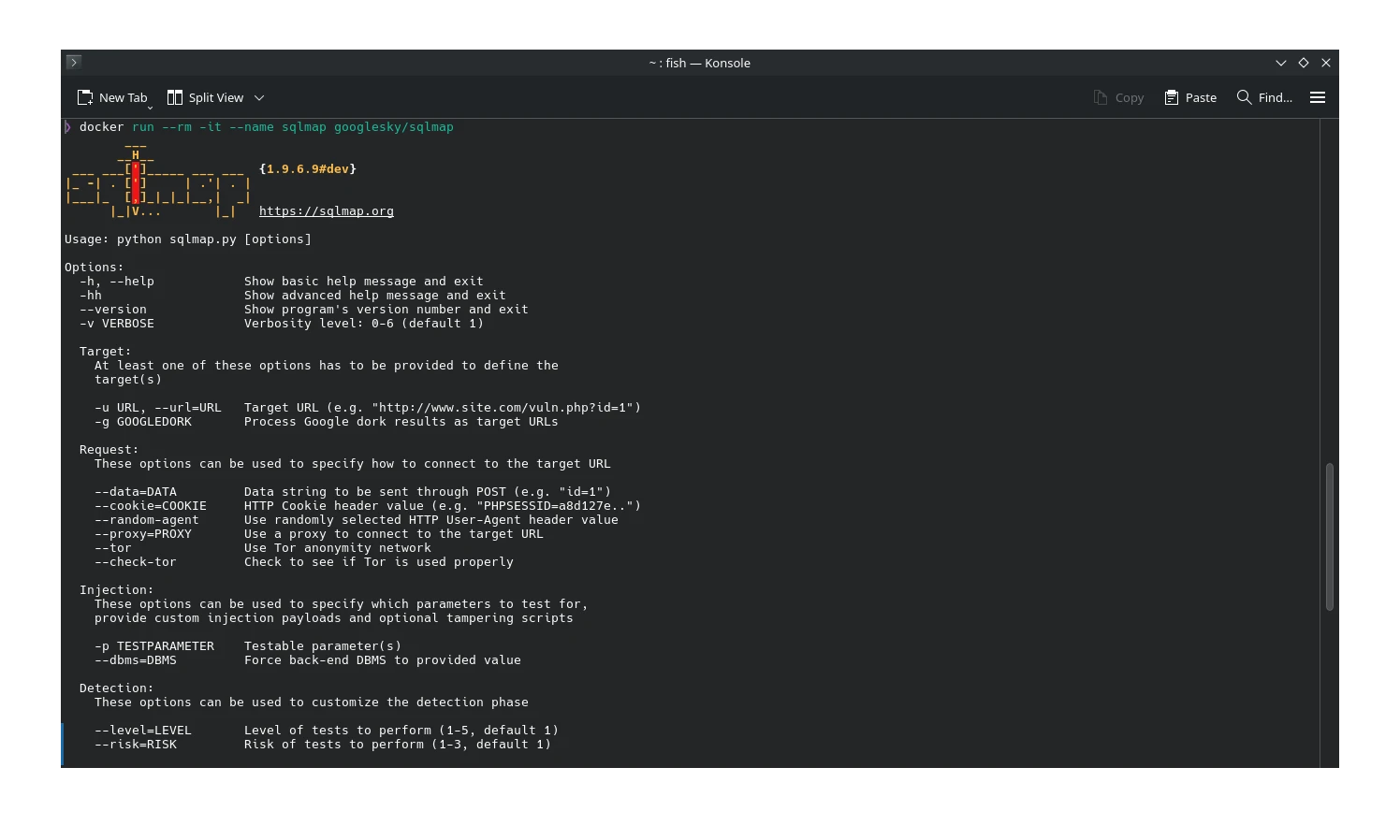
Hacking Databases with sqlmap in Docker
When it comes to finding and exploiting SQL injection vulnerabilities, few tools are as powerful—or…
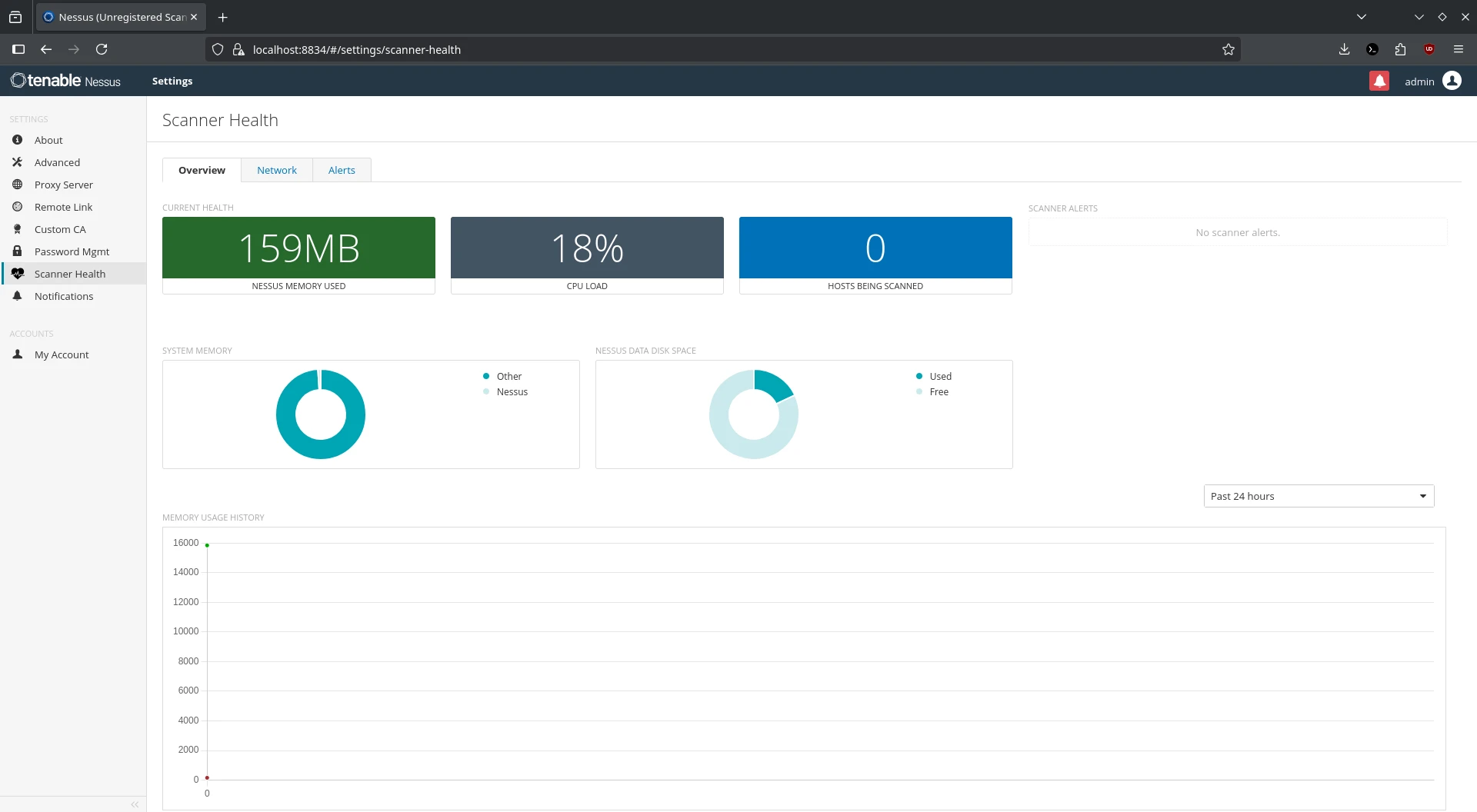
Deploying Tenable Nessus in Docker: Fast, Portable Vulnerability Scanning
Tenable Nessus has long been a trusted tool in the cybersecurity world for identifying vulnerabilities,…
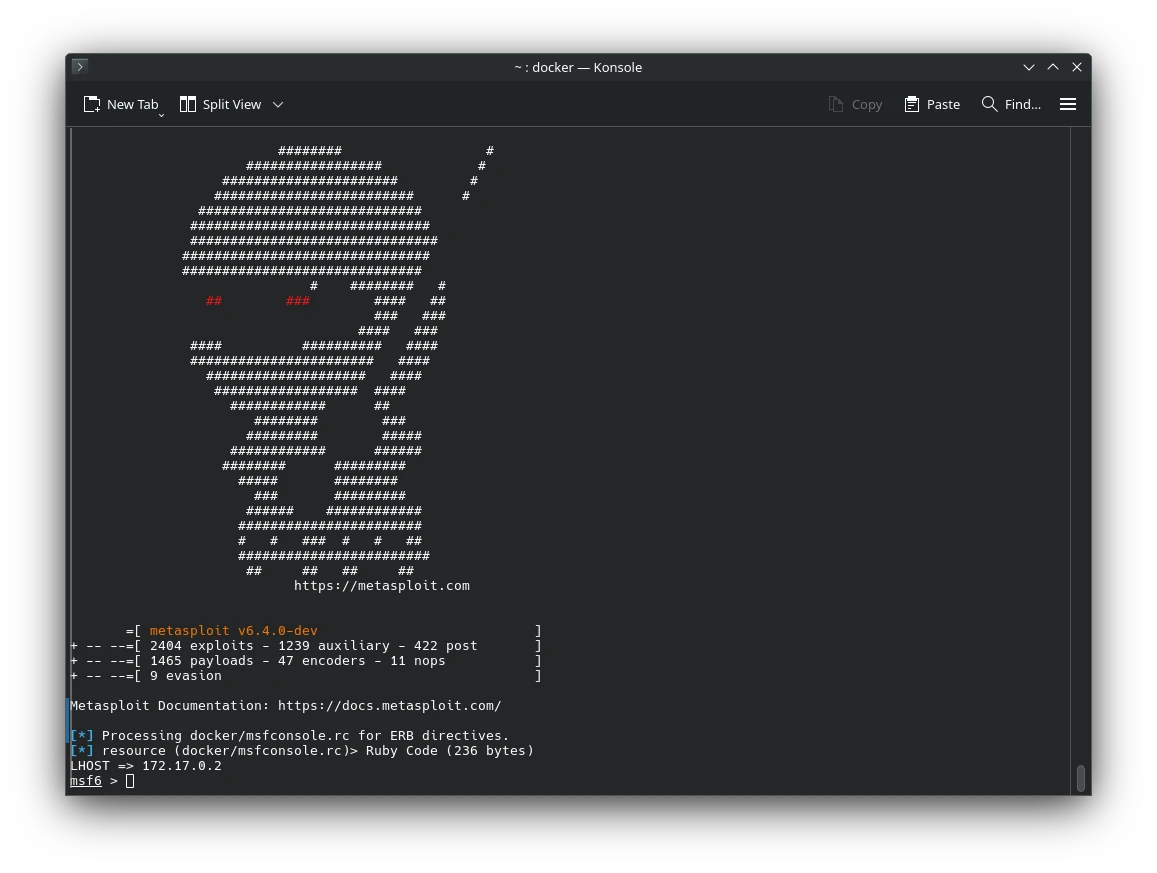
Penetration Testing with Metasploit Docker Image
🛠️ What is Metasploit Framework? The Metasploit Framework is one of the most powerful and…
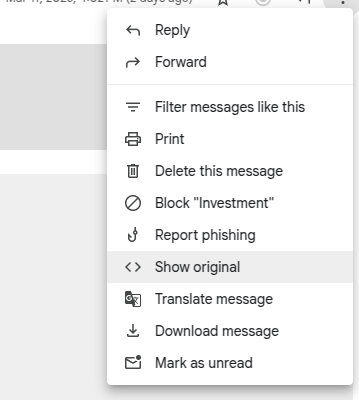
How to Recognize Spam Emails Using Gmail’s Show Original Feature
In today's digital world, spam emails have become increasingly sophisticated, making them harder to identify…