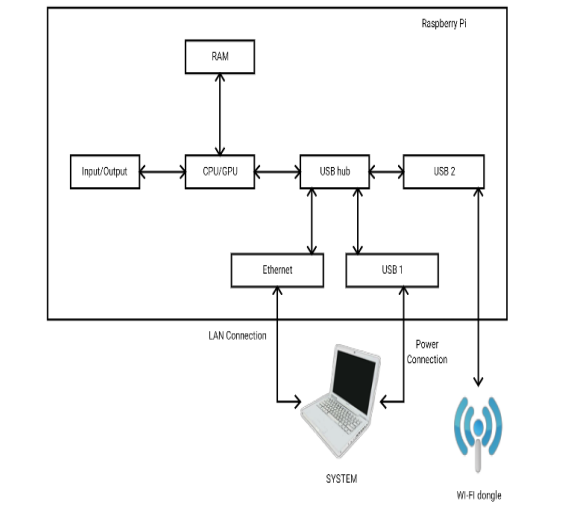
Wi-Fi Jamming Using Raspberry Pi: Security Tools for Network Protection
In today's interconnected world, wireless networks have become a critical part of our infrastructure. However,…
Reticulum: The Future of Secure and Resilient Networking
In a world where digital communication is often subject to surveillance, censorship, and centralized control,…
How to Install TP-Link TXE70UH WiFi Adapter on Debian/Ubuntu
The TP-Link TXE70UH is a high-performance WiFi 6 adapter that offers blazing-fast speeds and improved…
Exploring Innovative Projects with Starlink: Connecting the Unconnected
Introduction Starlink, the satellite internet constellation developed by SpaceX, has revolutionized how we think about…
DIY WiFi Pineapple Setup Guide: Building Your Own WiFi Pineapple with TP-Link Archer C7 v2 Router
In the realm of cybersecurity, tools like the WiFi Pineapple have become indispensable for professionals…
Building Your Own WiFi Pineapple Tetra: A Comprehensive Guide by Samy Younsi
In the cybersecurity world, tools like the WiFi Pineapple Tetra are essential for professionals and…
DIY WiFi Pineapple vs. Real WiFi Pineapple: A Detailed Comparison
In the realm of cybersecurity and penetration testing, tools like the WiFi Pineapple have become…
Understanding WiFi Jamming Attacks: Detailed Explanation and Implications
WiFi jamming attacks represent a significant threat in the realm of wireless communication. These attacks…
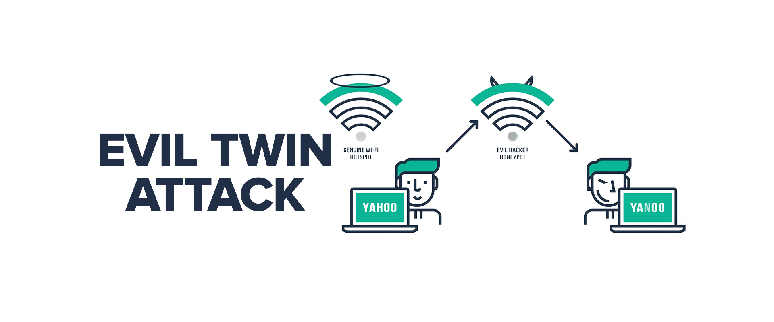
Understanding Evil Twin Attacks: History and Step-by-Step Guide to Gaining Passwords
The History of Evil Twin Attacks Evil Twin attacks are a sophisticated type of Wi-Fi…
Exploring the Benefits and Trade-offs: A Comparison of Throughput and CPU Usage between WPA3 and WPA2 Security on Wireless Networks
Introduction:In the realm of wireless communication, security is paramount. With the rise of vulnerabilities like…
Flipper Blackhat: Unleash the Power of WiFi Hacking and Evil Portal Capabilities
Welcome to hamradio.my, where we explore the remarkable Flipper Blackhat, a WiFi hacking device designed…
Exploring Wireless Security: WPA2 vs. WPA3
In the world of wireless communication, security is paramount. As the backbone of our interconnected…
Protecting Your Wireless Network: Understanding and Preventing PMKID Interception
In the digital age, concerns about cybersecurity are not unwarranted. With the prevalence of wireless…
Unleashing the Power of Pwnagotchi: A Revolutionary Tool for Tech Enthusiasts
Introduction: Welcome to hamradio.my, your trusted source for all things tech-related. In today's blog post,…
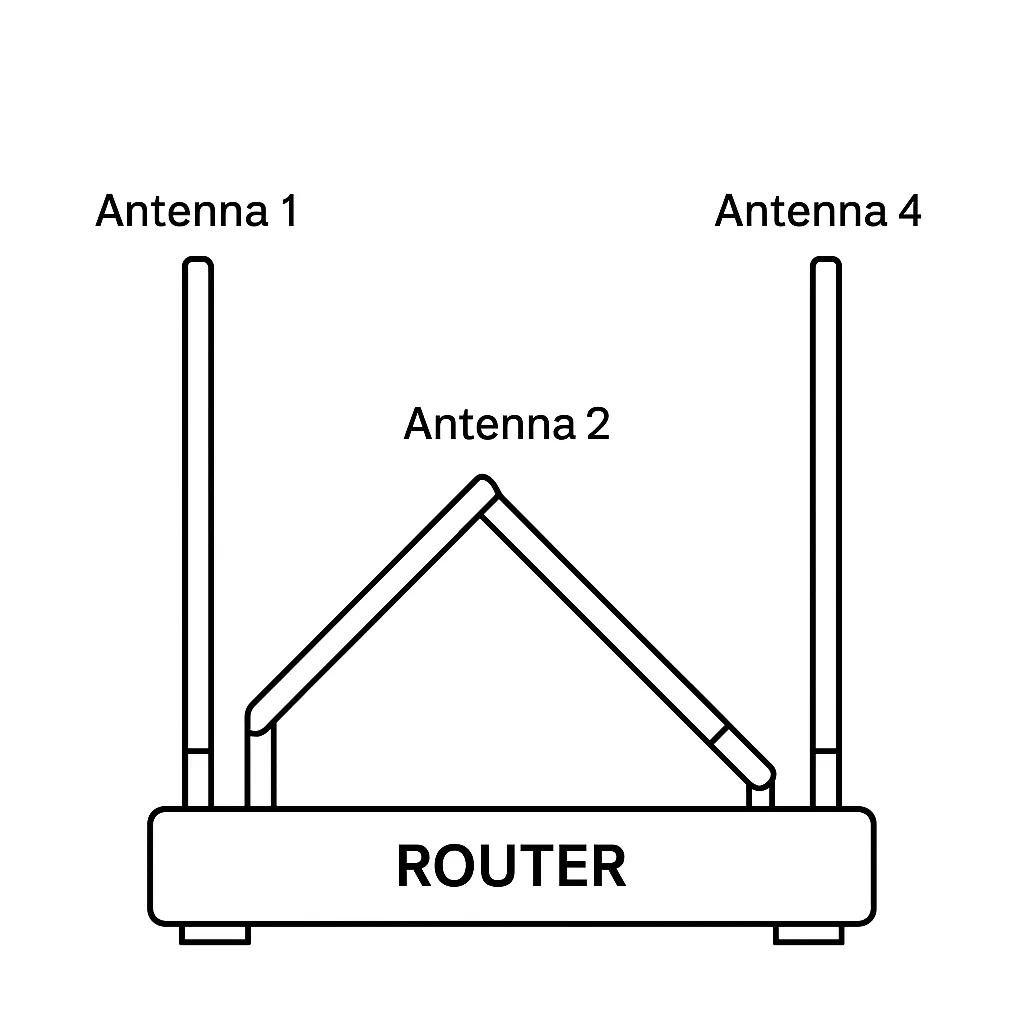
Antenna diversity
Antenna diversity, also known as space diversity, is any one of several wireless diversity schemes…
WIfite – Mass WEP/WPA Cracker For BackTrack4
introductiondesigned for Backtrack4 RC1 distribution of Ubuntu. Linux only; no windows or osx support. purposeto…
Echolink Application For Iphone, Ipod Touch
This app is for licensed Amateur Radio operators only. See www.echolink.org for more information. EchoLink…