What is MISP Threat Sharing? Collaborative Cyber Threat Intelligence
In today’s rapidly evolving cyber threat landscape, no organization is safe on its own. Hackers…
How Anubis Works: Fighting Bots with Proof-of-Work
The internet today is crawling with bots—some helpful, most not. Whether it’s AI scrapers harvesting…
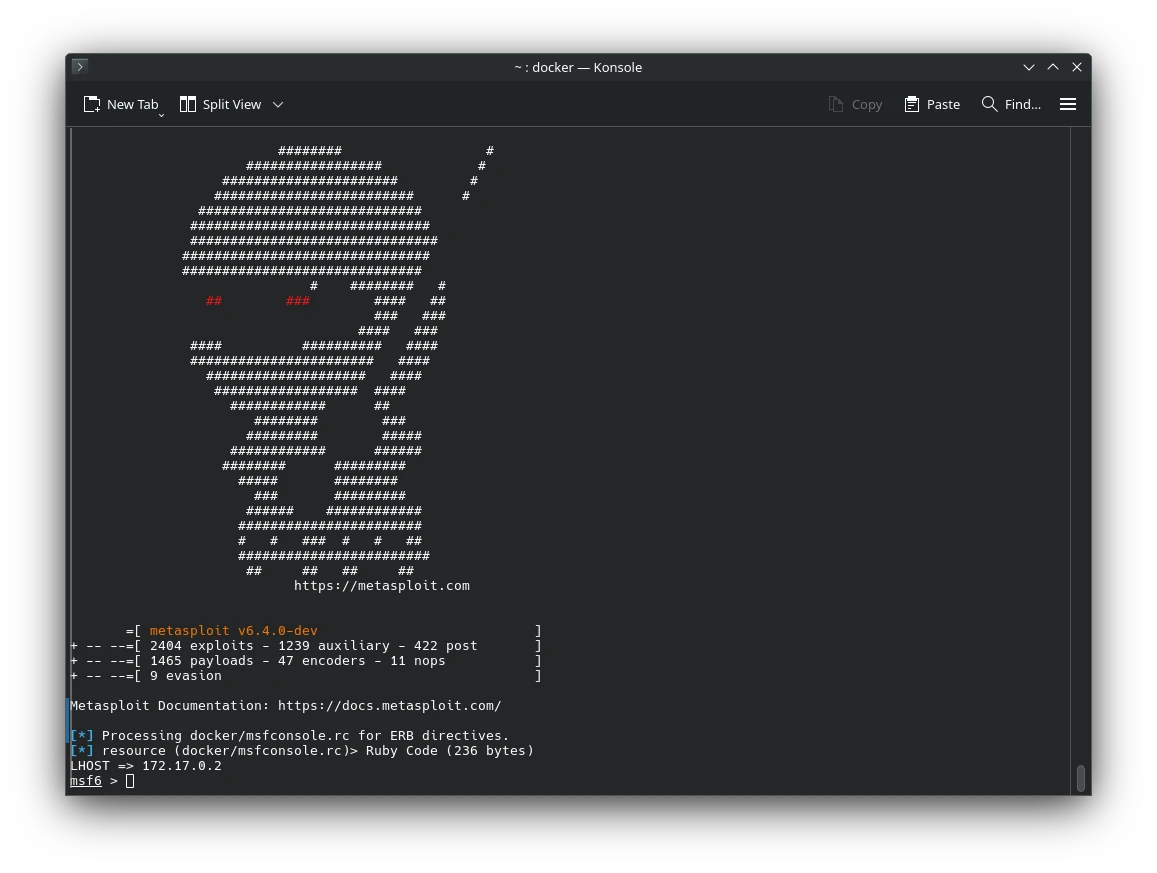
Armitage + Metasploit in Docker
If you're into penetration testing, you've probably used Metasploit — the Swiss Army knife of…
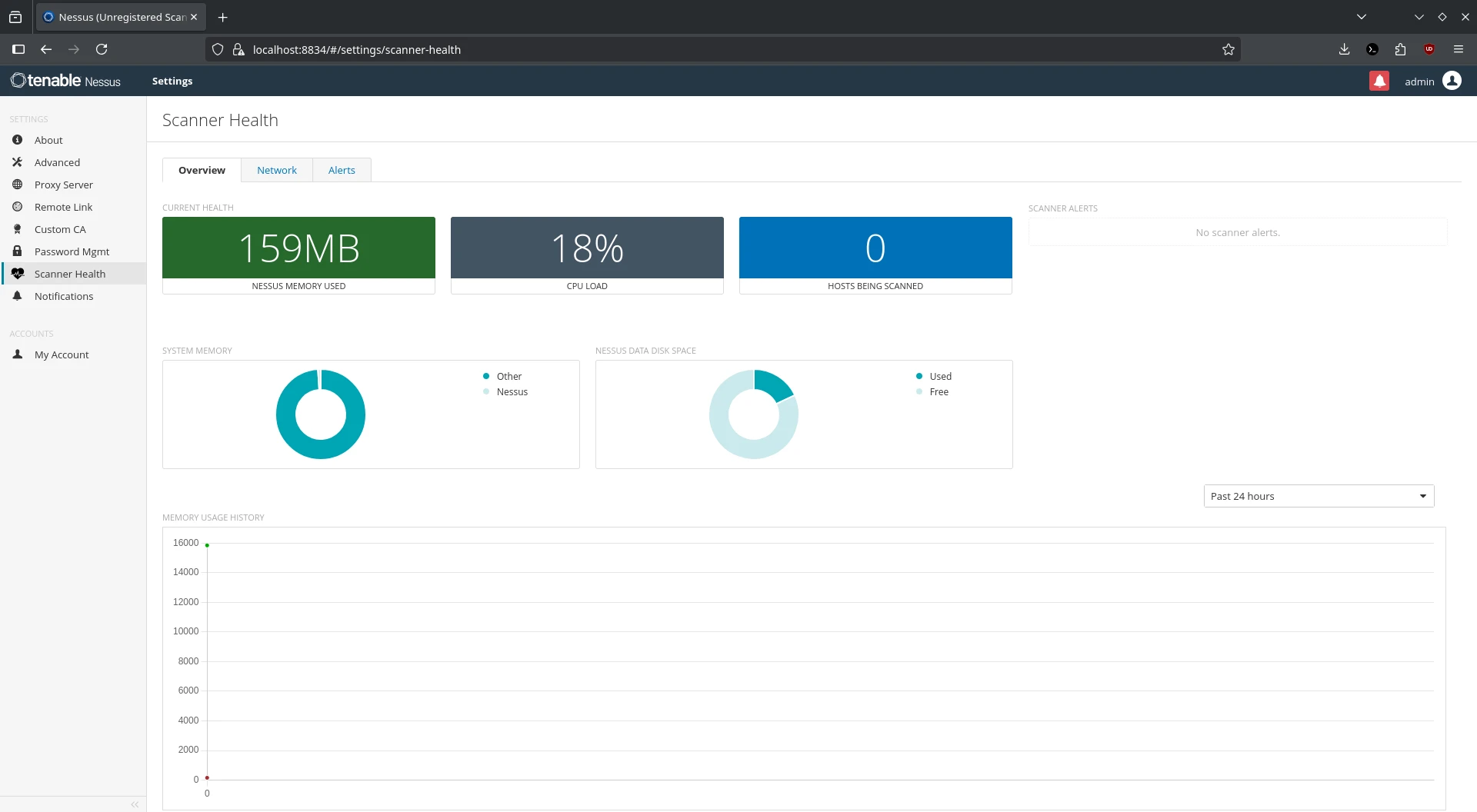
Deploying Tenable Nessus in Docker: Fast, Portable Vulnerability Scanning
Tenable Nessus has long been a trusted tool in the cybersecurity world for identifying vulnerabilities,…
Penetration Testing with Metasploit Docker Image
🛠️ What is Metasploit Framework? The Metasploit Framework is one of the most powerful and…
Choosing the Best Web Application Firewall (WAF) for Your WordPress Site
As WordPress powers over 40% of the web, it remains a prime target for hackers,…
Exploring gLinux: Google’s In-House Debian-Based Operating System
In the world of tech giants, custom tools and platforms are often developed in-house to…
Essential Linux Commands Every System Administrator Should Know
As a system administrator, mastering the command line is critical. Whether you're maintaining servers, managing…
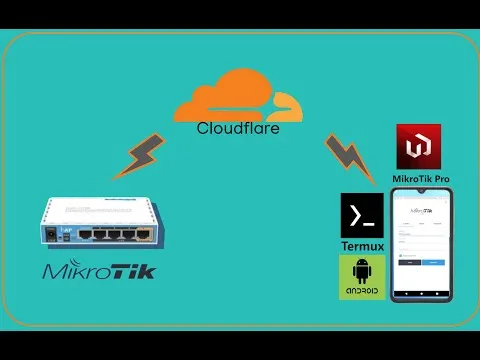
Hosting a Web Server Securely with Cloudflare Zero Trust Tunnel on MikroTik (Using Docker)
You have a web server running in your home network — maybe it’s a dashboard,…
DockFlare: Securely Expose Docker Services with Cloudflare Tunnels
🌟 Introduction: What Is DockFlare? Self-hosting applications has become increasingly popular among developers, tech enthusiasts,…
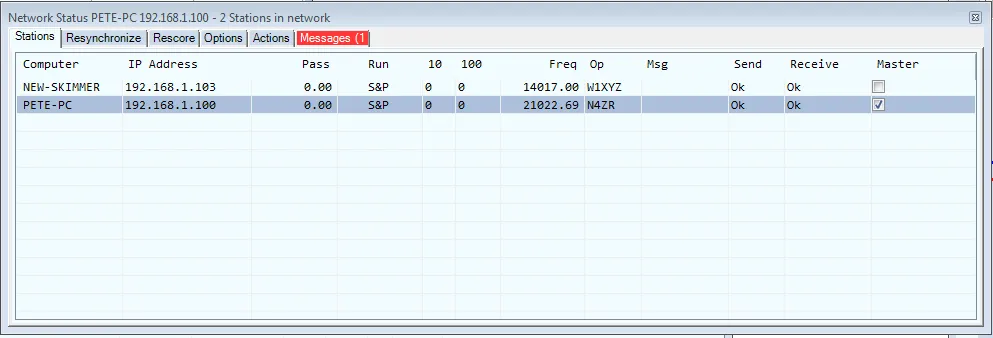
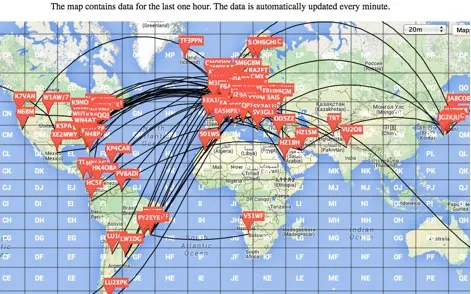
Multi-Computer and Multi-Op Contesting with N1MM Logger+
Are you looking to upgrade your ham radio contesting setup from single-operator to multi-operator? Or…
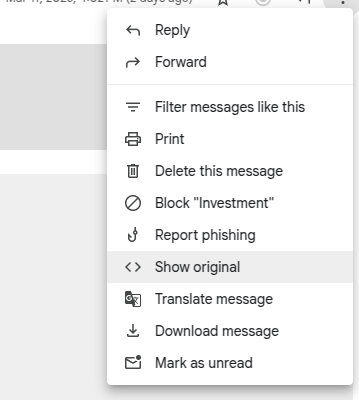
How to Recognize Spam Emails Using Gmail’s Show Original Feature
In today's digital world, spam emails have become increasingly sophisticated, making them harder to identify…
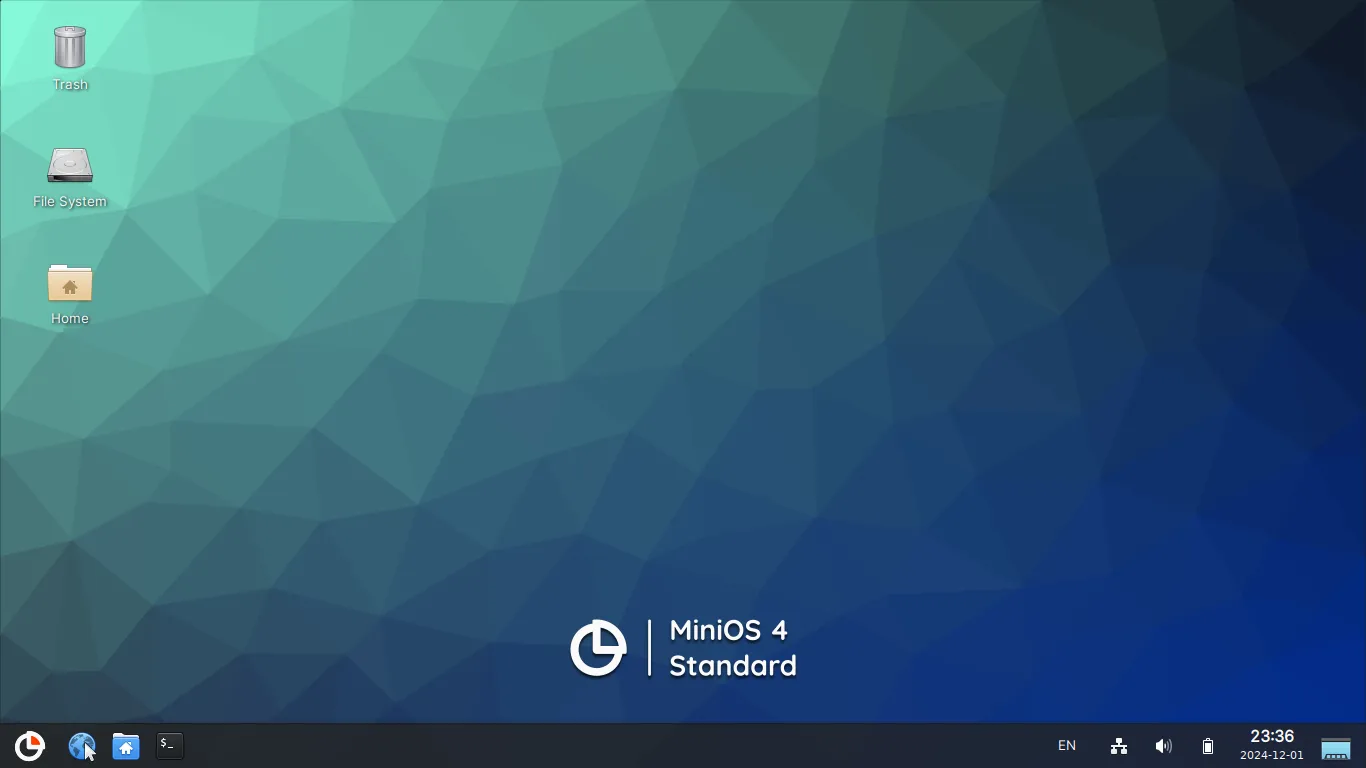
Discover MiniOS: The Ultimate Portable Linux Experience
Linux users seeking a portable, efficient, and reliable operating system now have a powerful solution…
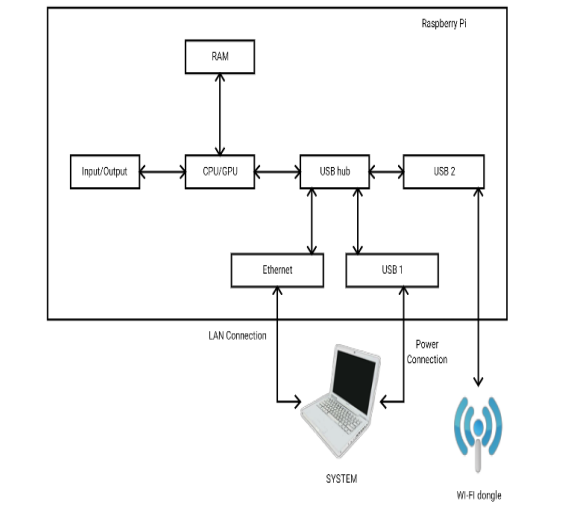
Wi-Fi Jamming Using Raspberry Pi: Security Tools for Network Protection
In today's interconnected world, wireless networks have become a critical part of our infrastructure. However,…
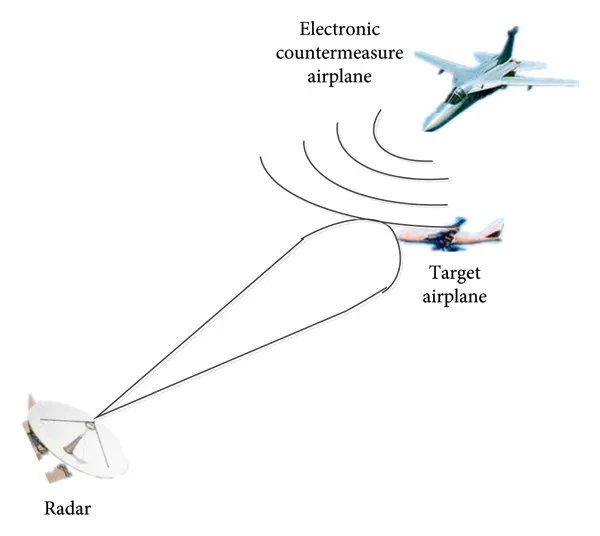
Disrupting the Digital Battlefield: Mastering the Art of Communications Jamming and Deception
In the modern theater of war, where information flows at the speed of light, control…
Whispers in the Ether: Unraveling the Secrets of Communications Intelligence (COMINT)
In the intricate dance of modern warfare and geopolitical strategy, information reigns supreme. The ability…
Electronic Warfare Terminology: Understanding the Language of Electromagnetic Combat
In the complex world of modern warfare, electronic warfare (EW) has become an essential component…
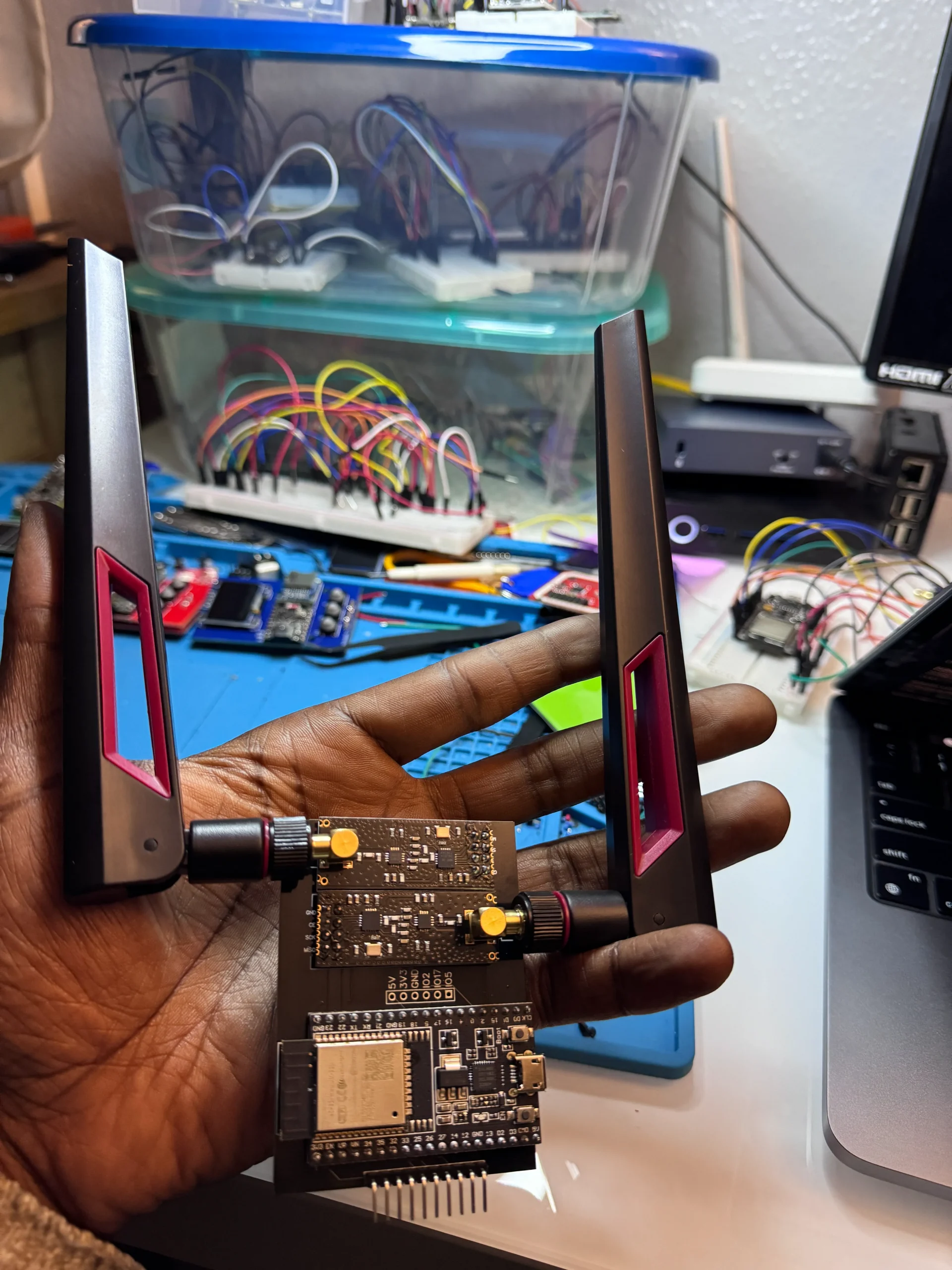
Exploring the DSTIKE HACKHELD: A Hackable ESP8266 Development Device
The DSTIKE HACKHELD is an open-source, hackable handheld device designed for DIY enthusiasts and security…
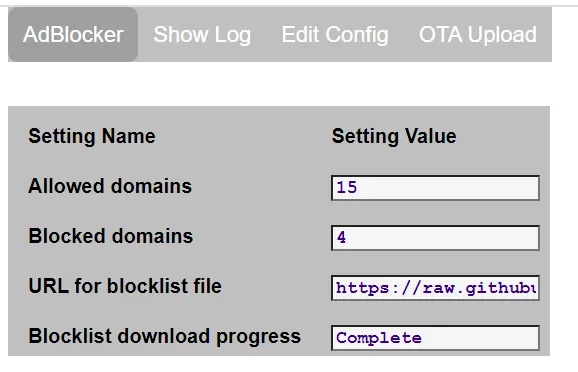
ESP32_AdBlocker: Affordable Network-Wide Ad Blocking on ESP32
Tired of intrusive ads and trackers? Meet ESP32_AdBlocker, a lightweight DNS Sinkhole that blocks unwanted…
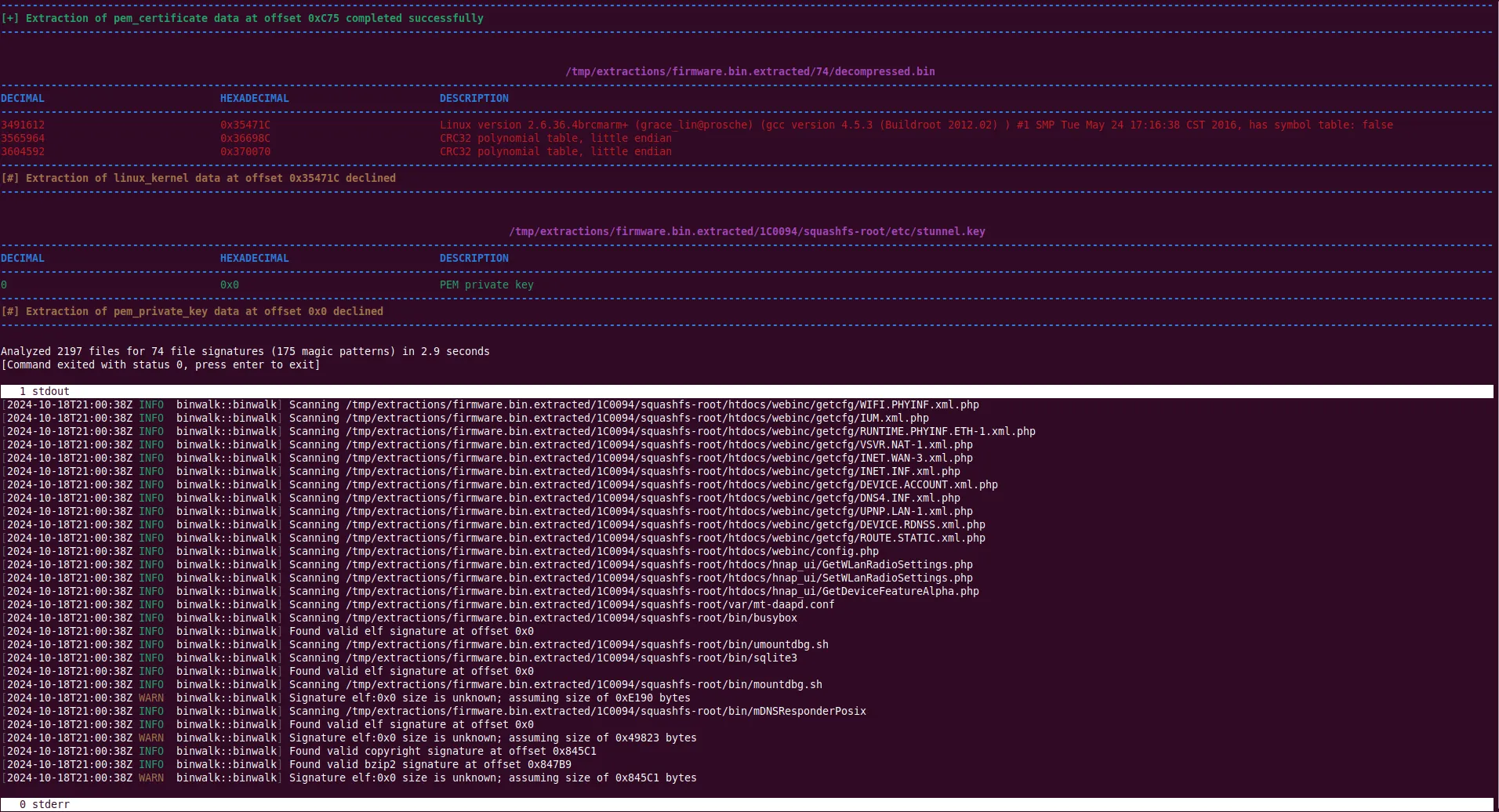
Unlocking Firmware Secrets with Binwalk: A Powerful Tool for Amateur Radio Enthusiasts
As technology evolves, amateur radio operators are increasingly exploring software-defined radios (SDRs), digital modes, and…
Securing Your DX Cluster: Essential Measures to Minimize Attacks
Understanding DX Spider in Amateur Radio 📻 Amateur radio, often called "ham radio," is a…
Understanding Public NTP Servers: A Vital Tool for Time Synchronization
In the world of networking and communications, precise time synchronization is crucial. Whether it’s ensuring…
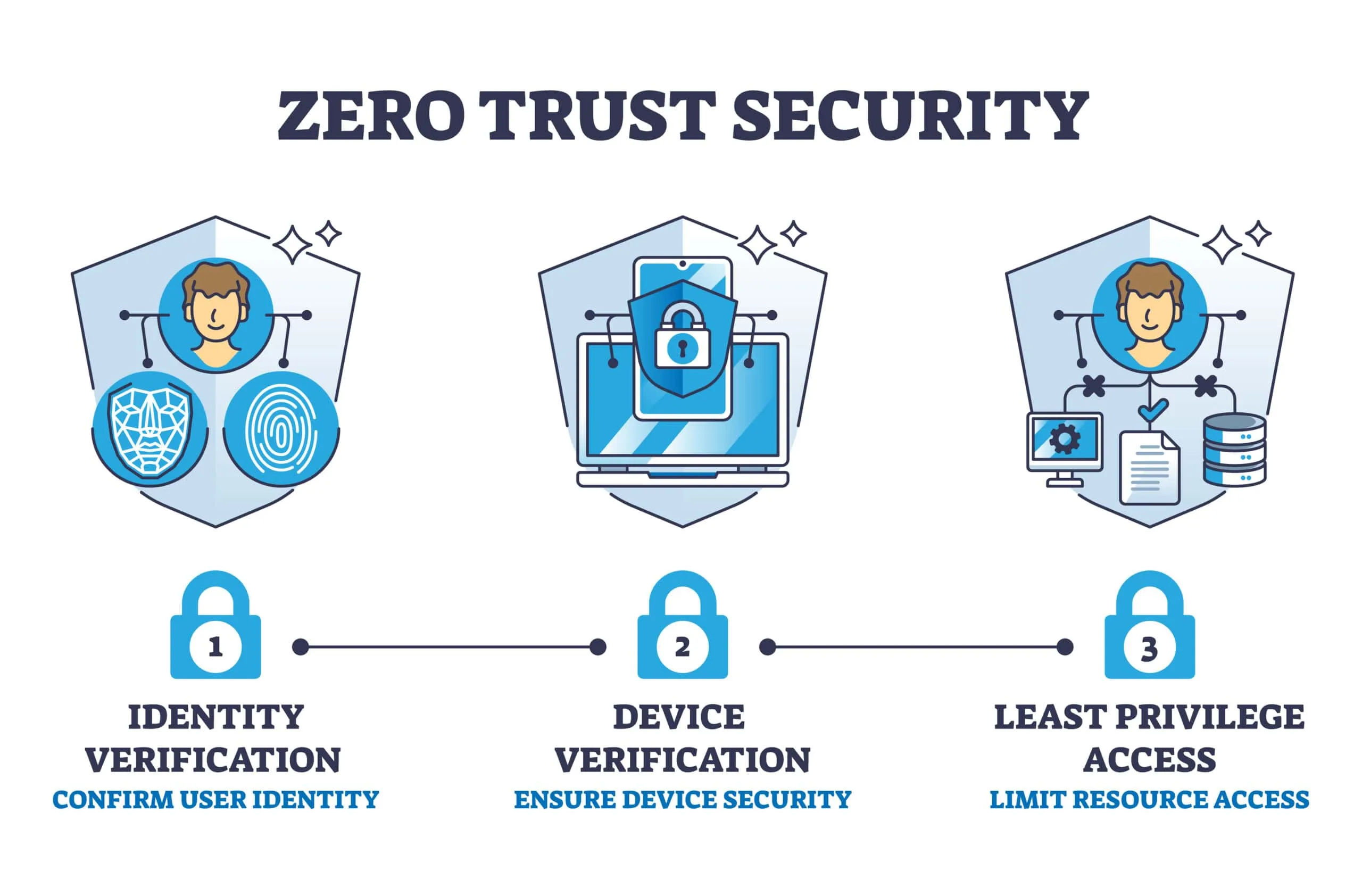
Introduction to Zero Trust Architecture
In today's digital landscape, security is a paramount concern for organizations worldwide. Traditional security models…
Unlocking the Secrets of Android Apps: A Deep Dive into Awesome Android Reverse Engineering
In the ever-evolving world of mobile technology, Android remains one of the most popular operating…
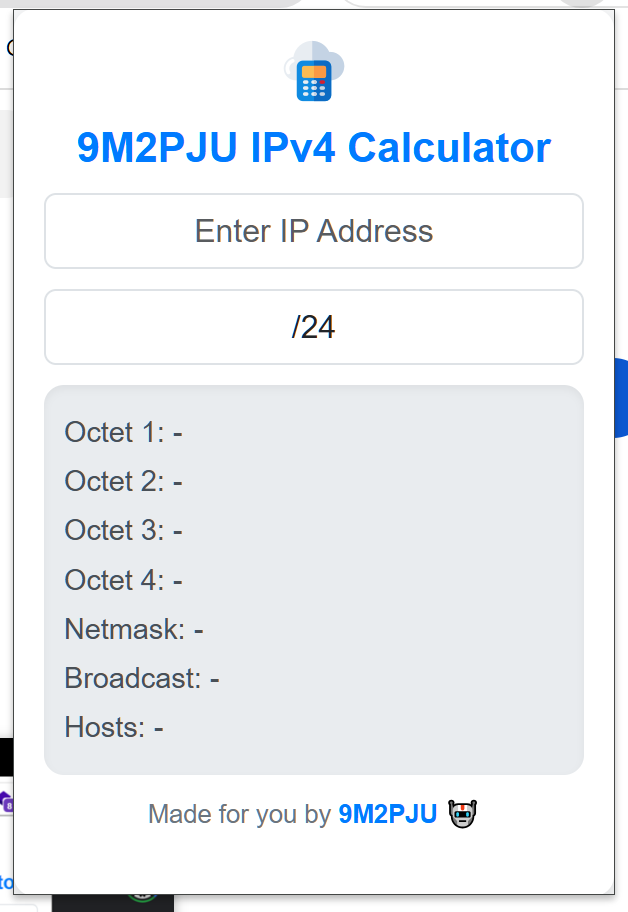
9M2PJU IPv4 Calculator Chrome Extension
Are you tired of manually calculating IPv4 address details? Look no further! We are thrilled…
Enhance Your Website Security with Wordfence: A Comprehensive WordPress Security Plugin
In today’s digital landscape, securing your website is paramount. As cyber threats become more sophisticated,…