What Is Proxmox?
If you’ve ever needed to run multiple operating systems or servers on a single machine…
What is MISP Threat Sharing? Collaborative Cyber Threat Intelligence
In today’s rapidly evolving cyber threat landscape, no organization is safe on its own. Hackers…
How Anubis Works: Fighting Bots with Proof-of-Work
The internet today is crawling with bots—some helpful, most not. Whether it’s AI scrapers harvesting…
Armitage + Metasploit in Docker
If you're into penetration testing, you've probably used Metasploit — the Swiss Army knife of…
Hacking Databases with sqlmap in Docker
When it comes to finding and exploiting SQL injection vulnerabilities, few tools are as powerful—or…
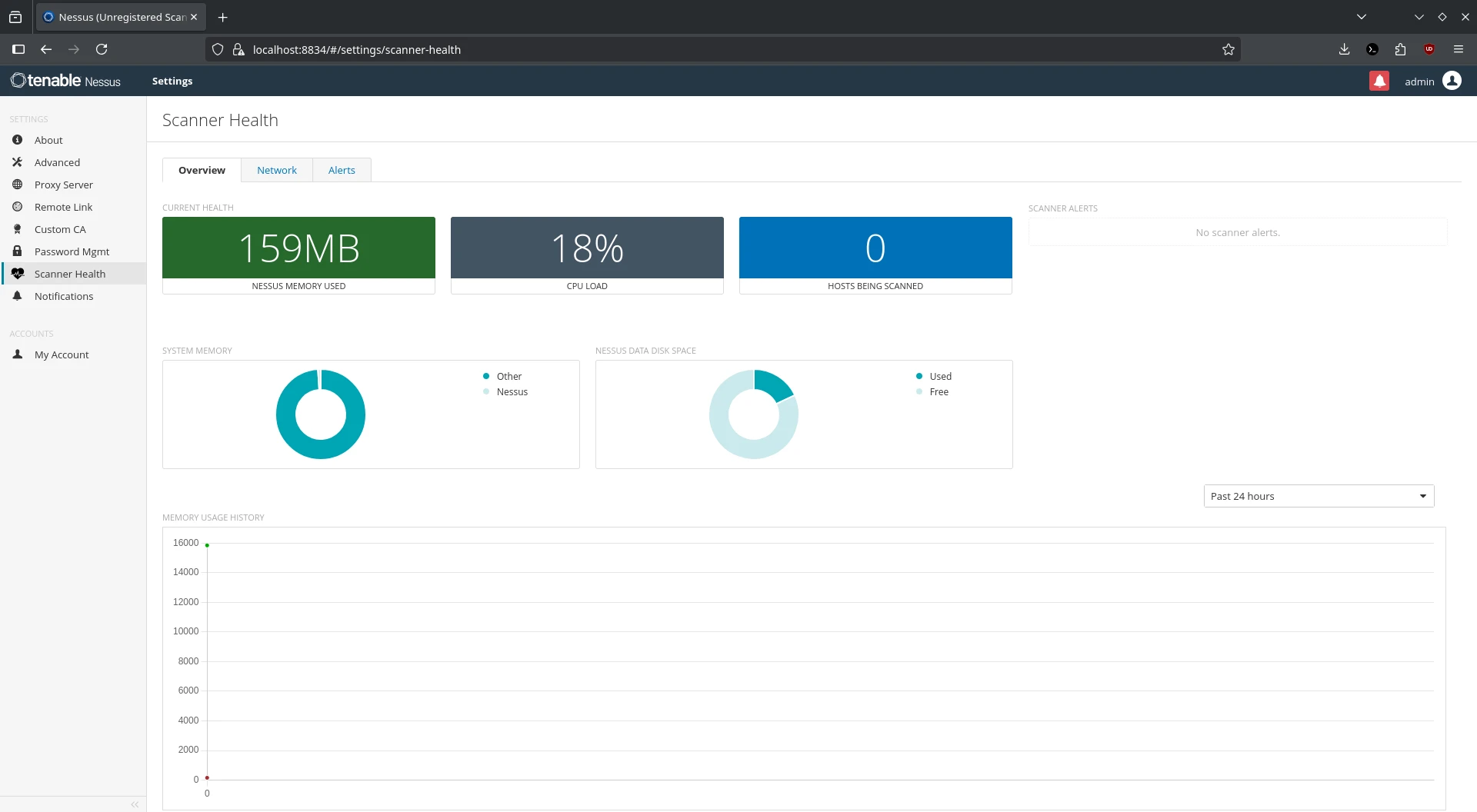
Deploying Tenable Nessus in Docker: Fast, Portable Vulnerability Scanning
Tenable Nessus has long been a trusted tool in the cybersecurity world for identifying vulnerabilities,…
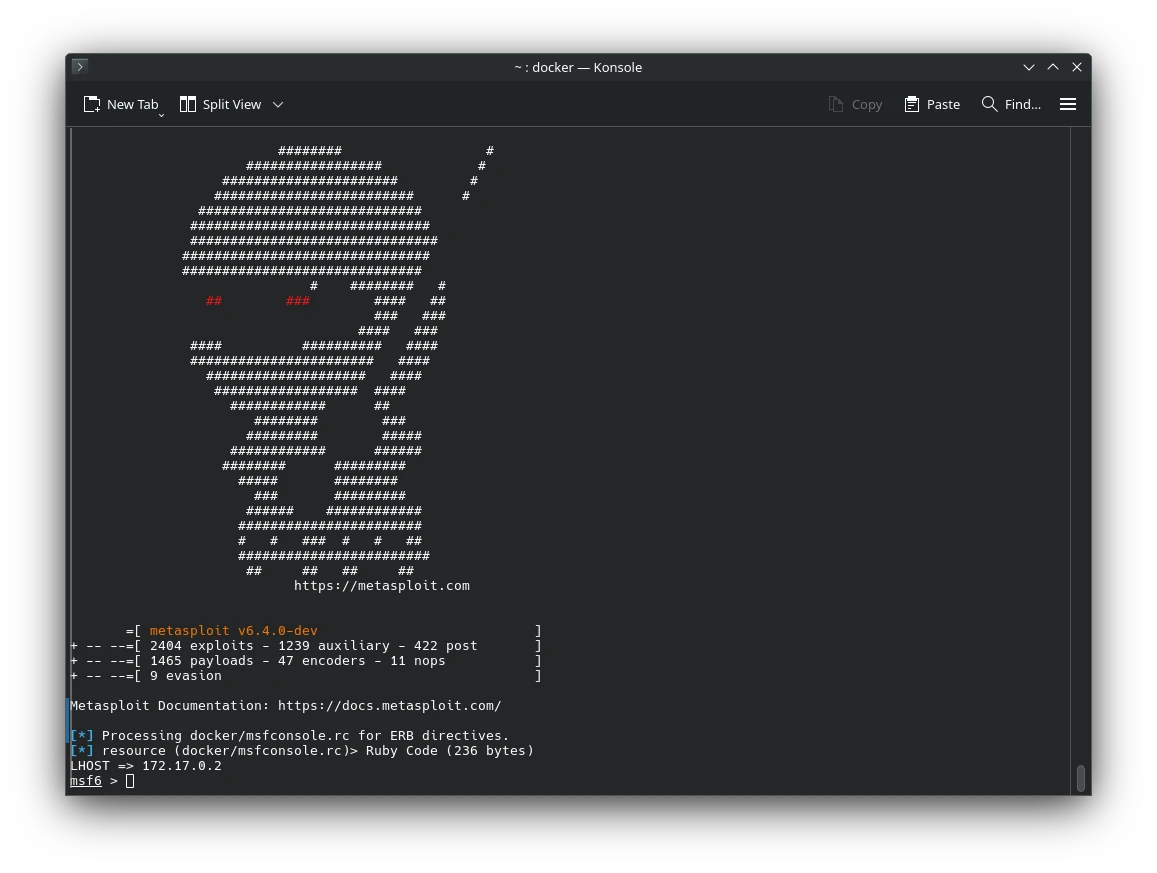
Penetration Testing with Metasploit Docker Image
🛠️ What is Metasploit Framework? The Metasploit Framework is one of the most powerful and…
PortNote – A Beautiful and Simple Way to Document Your Network Ports
When you run a self-hosted home lab or manage multiple services on a single machine,…
Essential Linux Commands Every System Administrator Should Know
As a system administrator, mastering the command line is critical. Whether you're maintaining servers, managing…
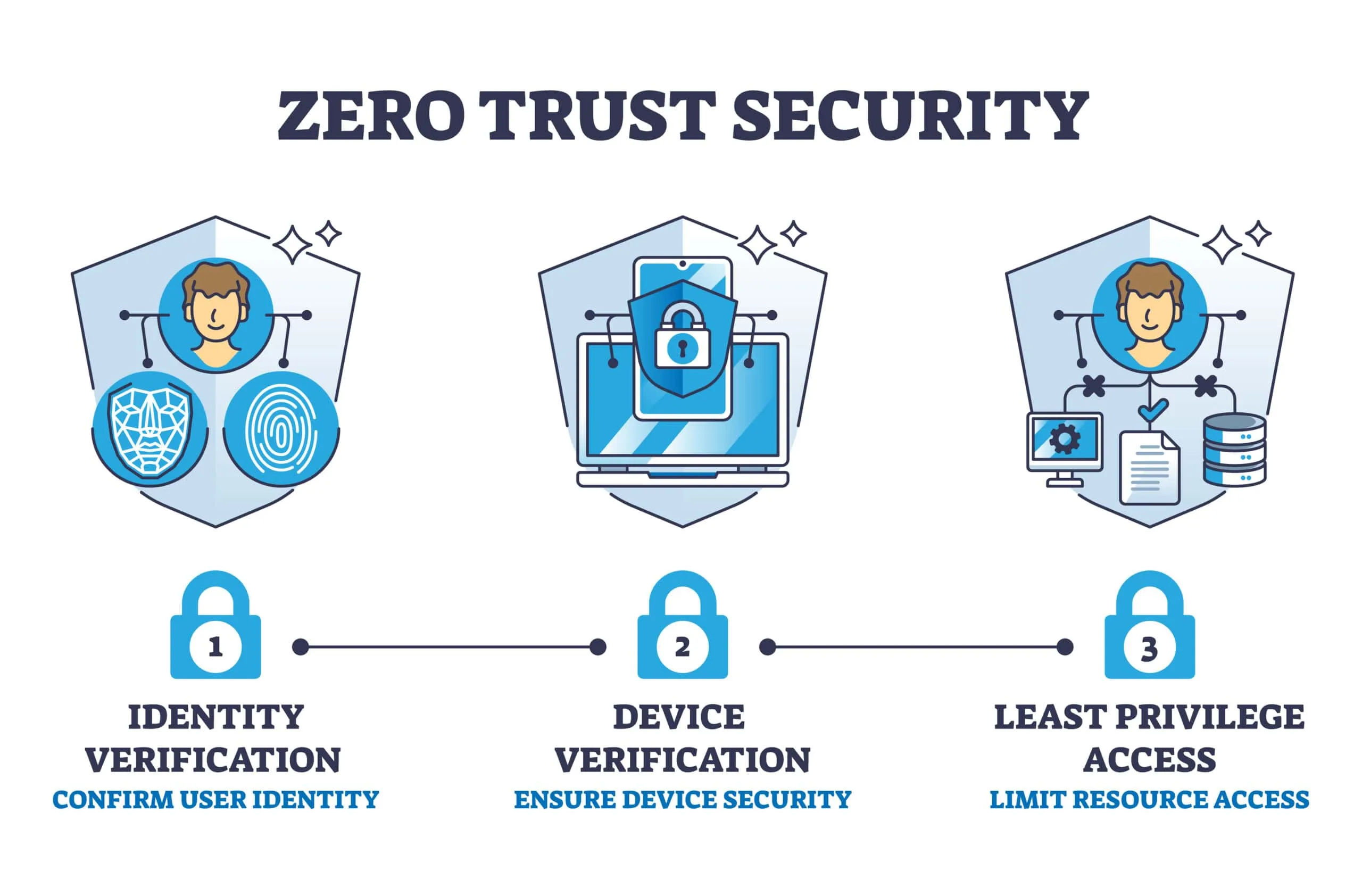
Introduction to Zero Trust Architecture
In today's digital landscape, security is a paramount concern for organizations worldwide. Traditional security models…
Modern Types of Secured Communications: Protecting Data in the Digital Age
In today's interconnected world, securing communication channels is more crucial than ever. With the rise…