How Anubis Works: Fighting Bots with Proof-of-Work
The internet today is crawling with bots—some helpful, most not. Whether it’s AI scrapers harvesting…
What is OpenWrt One: The First Router Built for Software Freedom
OpenWrt One is the first wireless router specifically designed from the ground up to run…
How OpenWrt Works: Inside the World’s Most Powerful Router Operating System
OpenWrt is not just firmware—it's a complete Linux-based operating system purpose-built for routers and embedded…
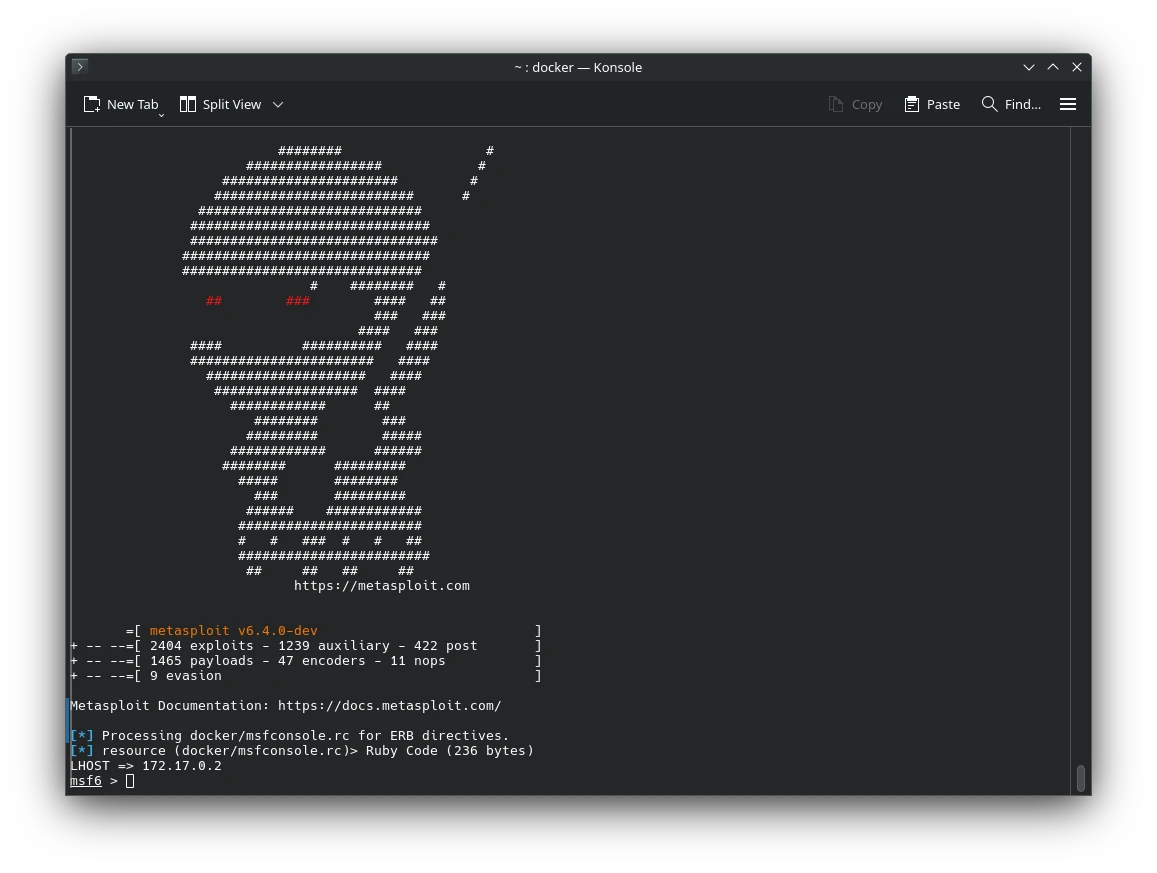
Penetration Testing with Metasploit Docker Image
🛠️ What is Metasploit Framework? The Metasploit Framework is one of the most powerful and…
How Netflix Powers the World’s Fastest Content Delivery Network with FreeBSD
When you stream your favorite Netflix show without buffering, you're witnessing the power of FreeBSD…
Software-Defined Networking (SDN): The Future of Flexible Network Infrastructure
In an age where speed, scalability, and automation are king, traditional networking methods are struggling…
How to Set Up a Caching Proxy Server to Speed Up Your Local Network
Does your home or office internet feel sluggish, especially when multiple people are browsing? You…
DockFlare: Securely Expose Docker Services with Cloudflare Tunnels
🌟 Introduction: What Is DockFlare? Self-hosting applications has become increasingly popular among developers, tech enthusiasts,…
Exploring the DSTIKE HACKHELD: A Hackable ESP8266 Development Device
The DSTIKE HACKHELD is an open-source, hackable handheld device designed for DIY enthusiasts and security…
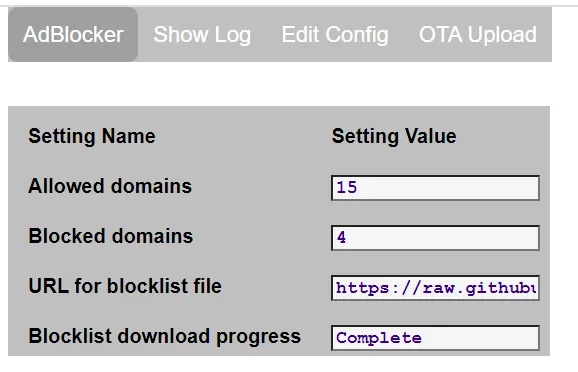
ESP32_AdBlocker: Affordable Network-Wide Ad Blocking on ESP32
Tired of intrusive ads and trackers? Meet ESP32_AdBlocker, a lightweight DNS Sinkhole that blocks unwanted…
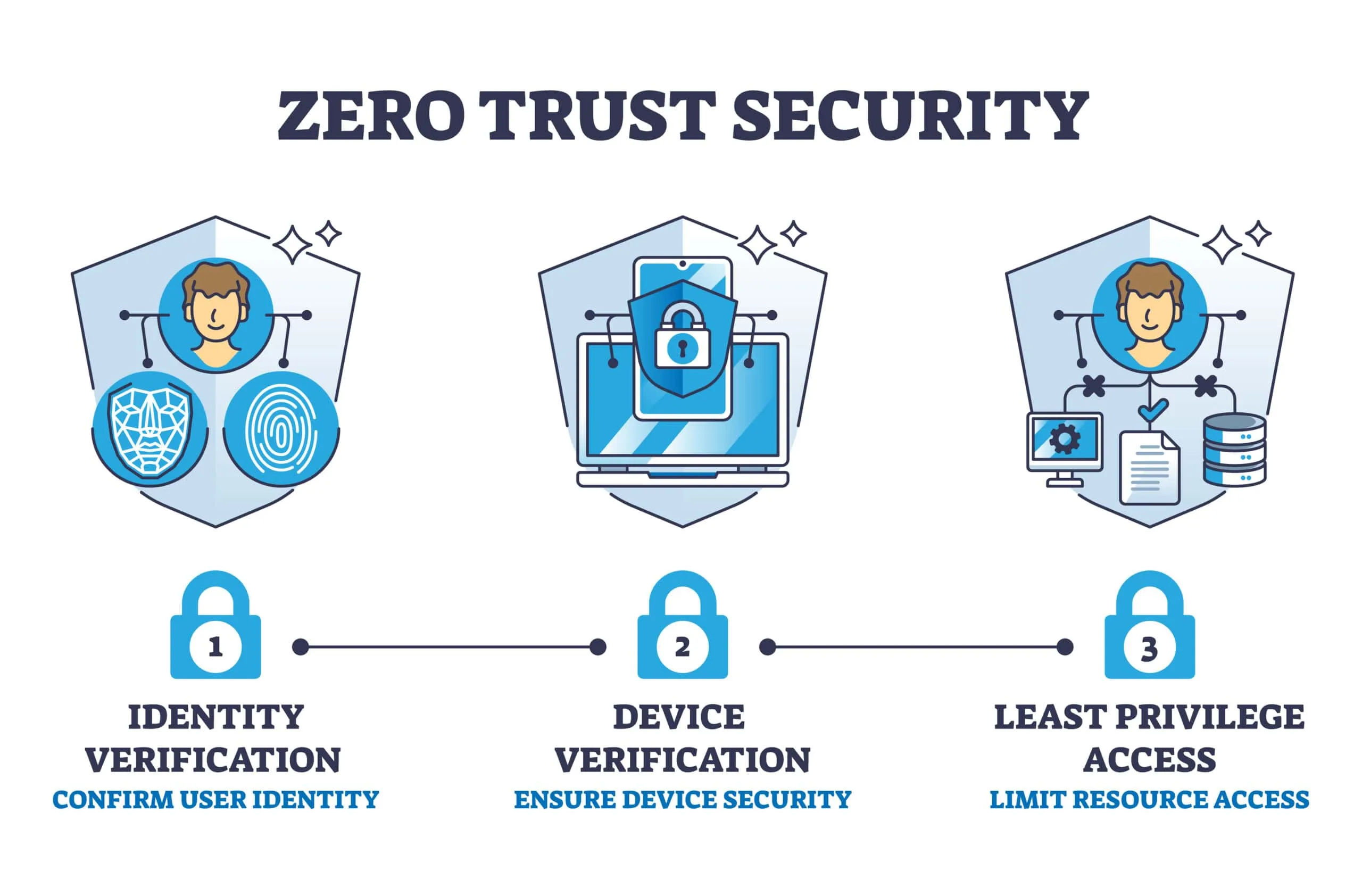
Introduction to Zero Trust Architecture
In today's digital landscape, security is a paramount concern for organizations worldwide. Traditional security models…