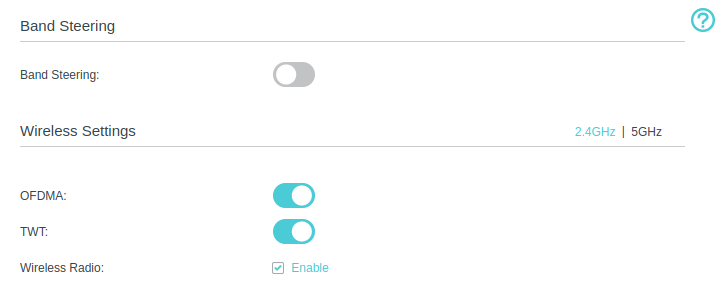
Exploring the DSTIKE HACKHELD: A Hackable ESP8266 Development Device
The DSTIKE HACKHELD is an open-source, hackable handheld device designed for DIY enthusiasts and security…
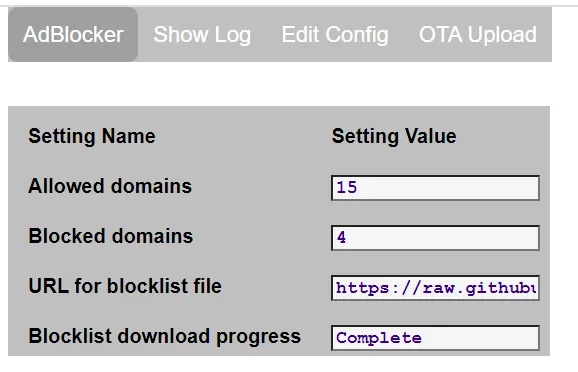
ESP32_AdBlocker: Affordable Network-Wide Ad Blocking on ESP32
Tired of intrusive ads and trackers? Meet ESP32_AdBlocker, a lightweight DNS Sinkhole that blocks unwanted…
Exploring Innovative Projects with Starlink: Connecting the Unconnected
Introduction Starlink, the satellite internet constellation developed by SpaceX, has revolutionized how we think about…
DIY WiFi Pineapple Setup Guide: Building Your Own WiFi Pineapple with TP-Link Archer C7 v2 Router
In the realm of cybersecurity, tools like the WiFi Pineapple have become indispensable for professionals…
Building Your Own WiFi Pineapple Tetra: A Comprehensive Guide by Samy Younsi
In the cybersecurity world, tools like the WiFi Pineapple Tetra are essential for professionals and…
DIY WiFi Pineapple vs. Real WiFi Pineapple: A Detailed Comparison
In the realm of cybersecurity and penetration testing, tools like the WiFi Pineapple have become…
Understanding WiFi Jamming Attacks: Detailed Explanation and Implications
WiFi jamming attacks represent a significant threat in the realm of wireless communication. These attacks…
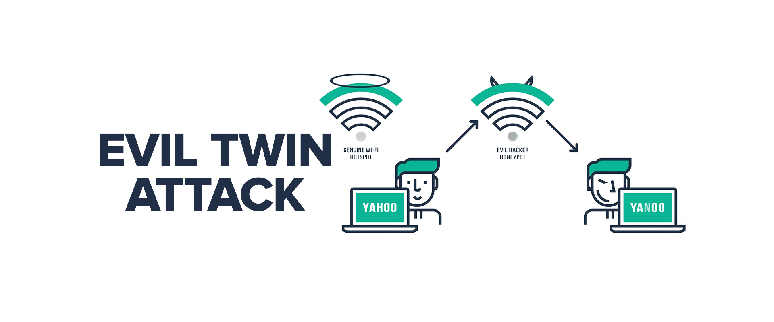
Understanding Evil Twin Attacks: History and Step-by-Step Guide to Gaining Passwords
The History of Evil Twin Attacks Evil Twin attacks are a sophisticated type of Wi-Fi…
Meneroka Wireless Broadband Leaky Coaxial Cables (WBLCX)
Dalam era digital hari ini, di mana ketersambungan adalah yang terpenting, inovasi dalam teknologi jalur…
Memahami Saluran WiFi dan Mengurangkan Kesesakan
Dalam dunia yang disambungkan secara digital, WiFi telah menjadi sebahagian daripada kehidupan seharian kita. Daripada…
Exploring the Benefits and Trade-offs: A Comparison of Throughput and CPU Usage between WPA3 and WPA2 Security on Wireless Networks
Introduction:In the realm of wireless communication, security is paramount. With the rise of vulnerabilities like…
Understanding Bufferbloat: Causes, Consequences, and Solutions
In today's digitally interconnected world, where we rely heavily on seamless internet connectivity for work,…
Flipper Blackhat: Unleash the Power of WiFi Hacking and Evil Portal Capabilities
Welcome to hamradio.my, where we explore the remarkable Flipper Blackhat, a WiFi hacking device designed…
Protecting Your Wireless Network: Understanding and Preventing PMKID Interception
In the digital age, concerns about cybersecurity are not unwarranted. With the prevalence of wireless…
Unleash the Power of Flipper Zero with Xtream Firmware
In the realm of hardware hacking and cybersecurity, enthusiasts are constantly seeking new tools to…
Unveiling Momentum Firmware: Revolutionizing Flipper Zero’s Capabilities
In the realm of cybersecurity and penetration testing, tools are the unsung heroes of the…
Hak5: Revolutionizing the World of Cybersecurity with Innovative Tools and Expertise
Introduction: In today's blog post, we explore Hak5, a renowned company that has made significant…
WiFi Hash Purple Monster: Capturing EAPOL/PMKID Packets with M5Stack/ESP32
Introduction: Welcome to my tech blog, where we explore innovative devices and techniques. Today, we…
Unleashing the Power of Pwnagotchi: A Revolutionary Tool for Tech Enthusiasts
Introduction: Welcome to hamradio.my, your trusted source for all things tech-related. In today's blog post,…
Hedy Lamarr’s Discovery: A Game-Changer that Transformed the World
Introduction: In the realm of scientific breakthroughs, there are rare instances where an individual's discovery…