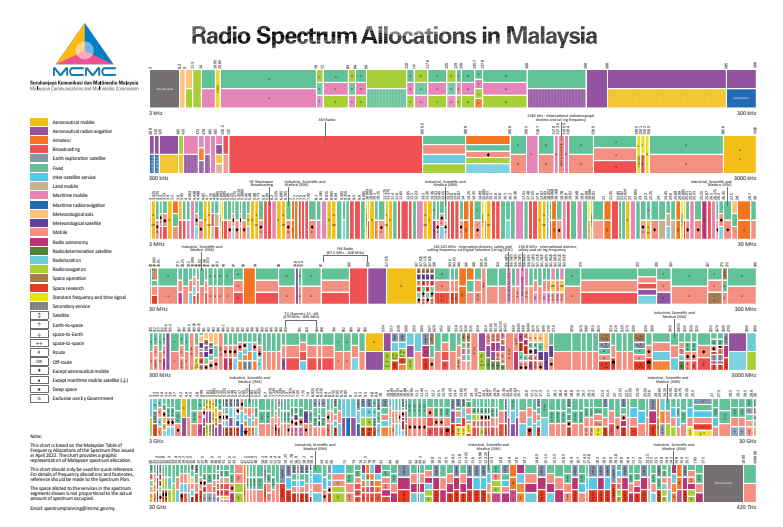
How Radio Spectrum Works in Malaysia
If you've ever used Wi-Fi, tuned into a radio station, made a phone call, or…
How to Download Android ADB, Add It to Windows PATH and Why You Should
If you're an Android enthusiast, tinker with IoT gear, or dive into custom ROMs, you've…
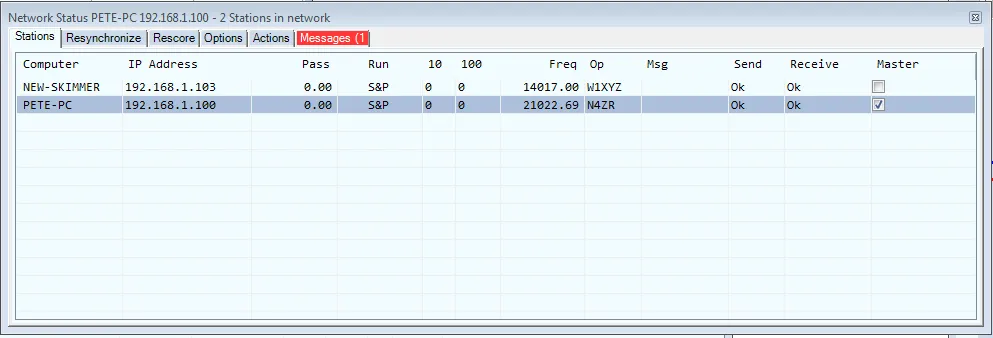
Multi-Computer and Multi-Op Contesting with N1MM Logger+
Are you looking to upgrade your ham radio contesting setup from single-operator to multi-operator? Or…
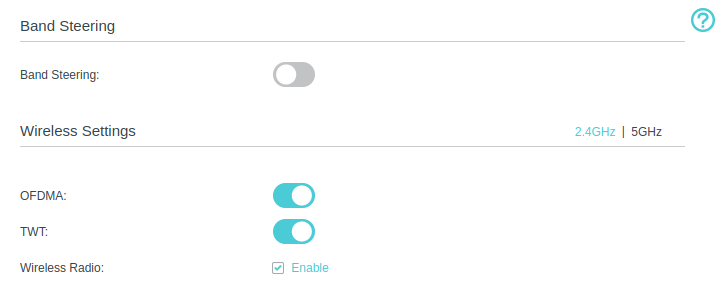
Should You Combine or Separate 2.4GHz and 5GHz Wi-Fi Bands? Let’s Break It Down
In the era of smart homes, streaming, and constant connectivity, your Wi-Fi setup can make…
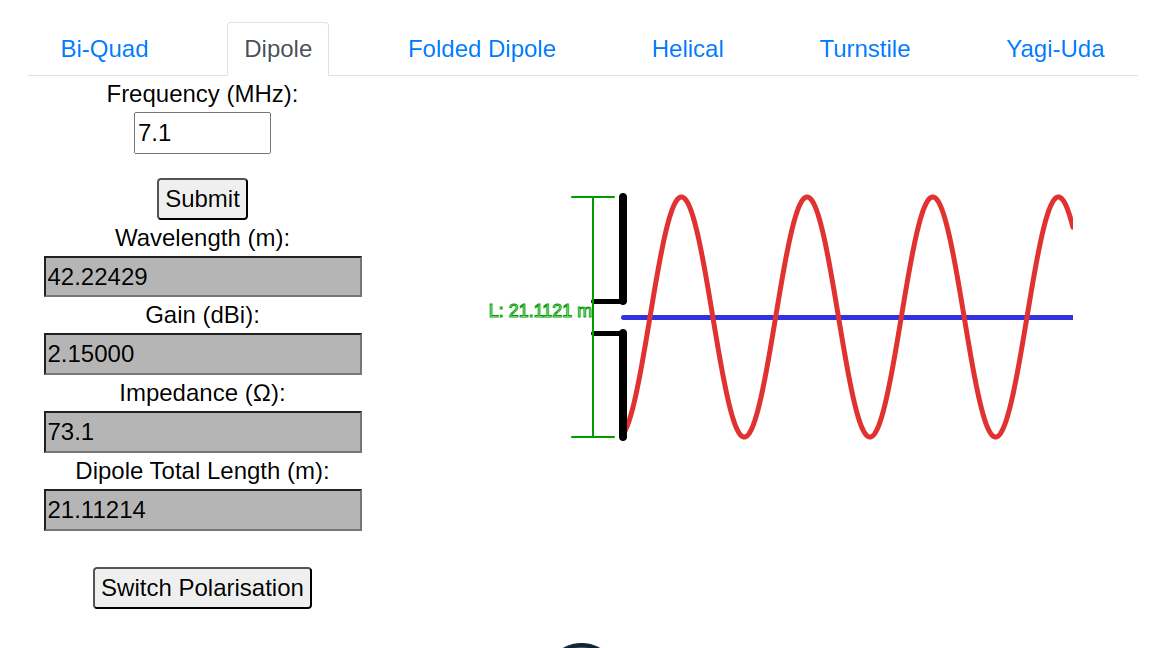
Antenna Dimensions Calculator: A Handy Tool for Amateur Radio Enthusiasts
If you're an amateur radio operator, you know that building antennas can be both a…
Exploring Innovative Projects with Starlink: Connecting the Unconnected
Introduction Starlink, the satellite internet constellation developed by SpaceX, has revolutionized how we think about…
DIY WiFi Pineapple Setup Guide: Building Your Own WiFi Pineapple with TP-Link Archer C7 v2 Router
In the realm of cybersecurity, tools like the WiFi Pineapple have become indispensable for professionals…
Building Your Own WiFi Pineapple Tetra: A Comprehensive Guide by Samy Younsi
In the cybersecurity world, tools like the WiFi Pineapple Tetra are essential for professionals and…
DIY WiFi Pineapple vs. Real WiFi Pineapple: A Detailed Comparison
In the realm of cybersecurity and penetration testing, tools like the WiFi Pineapple have become…
Understanding WiFi Jamming Attacks: Detailed Explanation and Implications
WiFi jamming attacks represent a significant threat in the realm of wireless communication. These attacks…
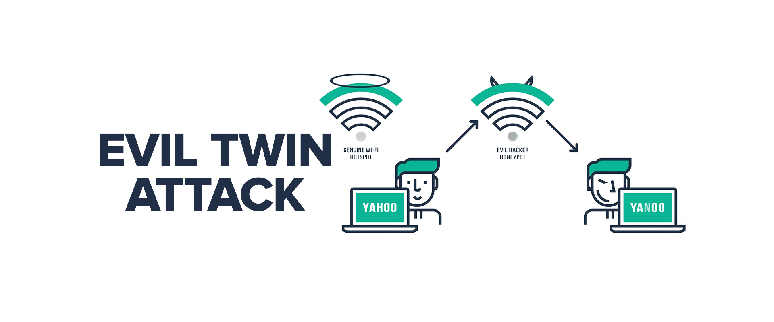
Understanding Evil Twin Attacks: History and Step-by-Step Guide to Gaining Passwords
The History of Evil Twin Attacks Evil Twin attacks are a sophisticated type of Wi-Fi…
Memahami Saluran WiFi dan Mengurangkan Kesesakan
Dalam dunia yang disambungkan secara digital, WiFi telah menjadi sebahagian daripada kehidupan seharian kita. Daripada…
Unveiling the Evil Crow RF: Your Gateway to Radiofrequency Hacking
In the realm of cybersecurity, the pursuit of innovative tools and techniques to bolster defenses…
Exploring the Benefits and Trade-offs: A Comparison of Throughput and CPU Usage between WPA3 and WPA2 Security on Wireless Networks
Introduction:In the realm of wireless communication, security is paramount. With the rise of vulnerabilities like…
Unraveling the Power of OpenWRT: A Comprehensive Guide
Introduction:In the world of networking, where flexibility, security, and customization are paramount, OpenWRT emerges as…
Flipper Blackhat: Unleash the Power of WiFi Hacking and Evil Portal Capabilities
Welcome to hamradio.my, where we explore the remarkable Flipper Blackhat, a WiFi hacking device designed…
Unlocking Wireless Secrets with the Universal Radio Hacker (URH)
In a world where wireless communication reigns supreme, understanding the intricate dance of signals that…
Exploring Wireless Security: WPA2 vs. WPA3
In the world of wireless communication, security is paramount. As the backbone of our interconnected…
Protecting Your Wireless Network: Understanding and Preventing PMKID Interception
In the digital age, concerns about cybersecurity are not unwarranted. With the prevalence of wireless…
Exploring the World of Wardriving: Unveiling the Secrets of Wireless Networks
In the digital age, where connectivity is paramount, the exploration of wireless networks has become…
The Birth of MonstaTek M1
"Hello World. It was only a matter of time that the imagination of tech geeks,…
Hak5: Revolutionizing the World of Cybersecurity with Innovative Tools and Expertise
Introduction: In today's blog post, we explore Hak5, a renowned company that has made significant…
WiFi Hash Purple Monster: Capturing EAPOL/PMKID Packets with M5Stack/ESP32
Introduction: Welcome to my tech blog, where we explore innovative devices and techniques. Today, we…
Unleashing the Power of Pwnagotchi: A Revolutionary Tool for Tech Enthusiasts
Introduction: Welcome to hamradio.my, your trusted source for all things tech-related. In today's blog post,…