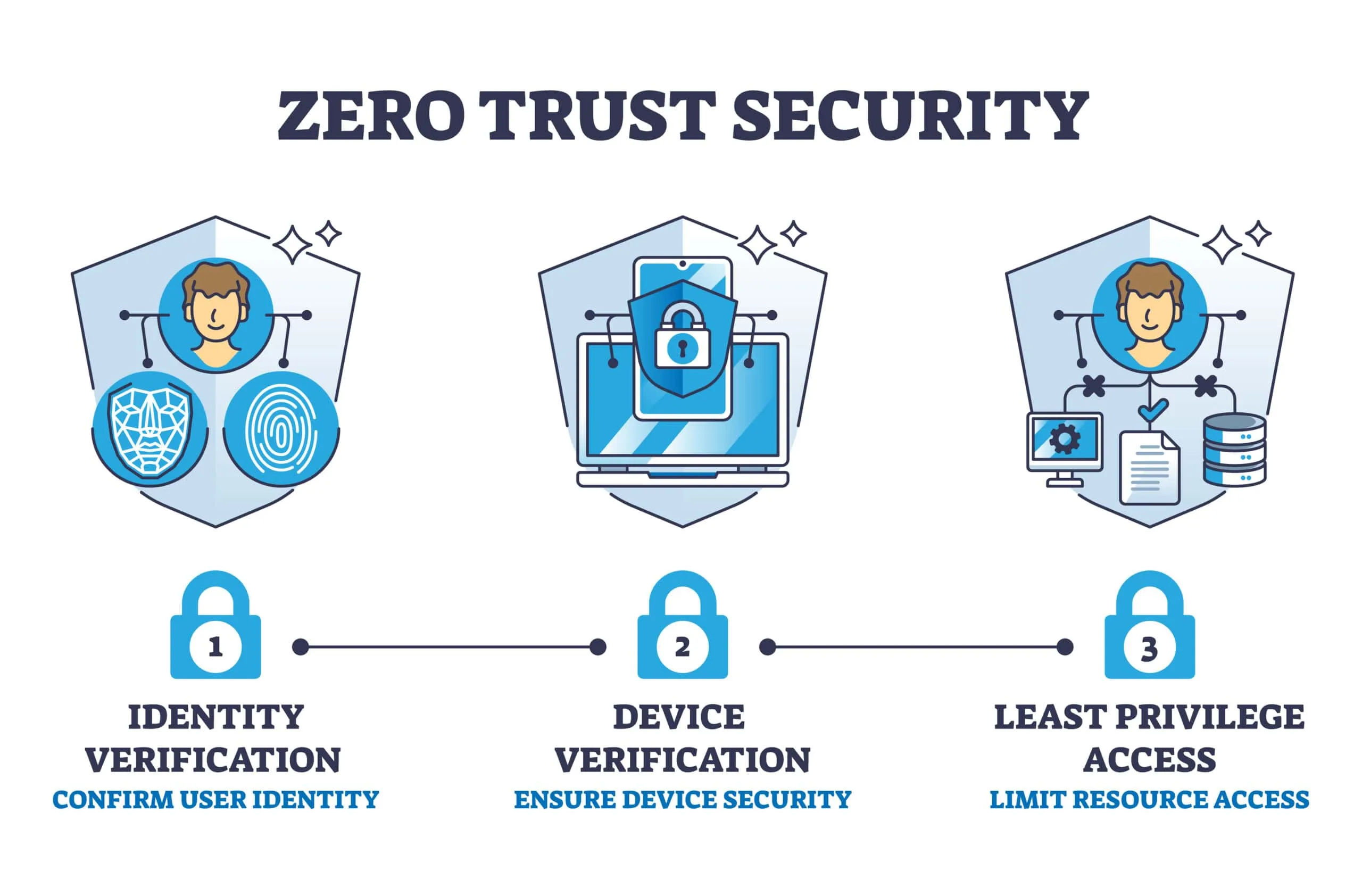
Enhance Your Website Security with Wordfence: A Comprehensive WordPress Security Plugin
In today’s digital landscape, securing your website is paramount. As cyber threats become more sophisticated,…
Exploring Network Tunnels: History, Usage, Applications, and Misuse
In the realm of computer networking, tunnels play a crucial role in facilitating secure communication,…
Unleashing CyberChef: Your Ultimate Cybersecurity Swiss Army Knife
In the realm of cybersecurity, having the right tools at your disposal can mean the…
Unlocking the Ultimate Guide: The Book of Secret Knowledge on GitHub
Introduction In the ever-evolving world of technology, staying ahead of the curve requires continuous learning…
Metasploit: A Comprehensive Guide to History, Development, Usage, and Installation on Ubuntu Linux
Metasploit is a powerful and versatile tool used primarily for penetration testing and security auditing.…
Unveiling Email Tracking: What You Need to Know
In today's digital landscape, email has revolutionized communication, making it convenient and efficient. However, beneath…
DIY WiFi Pineapple Setup Guide: Building Your Own WiFi Pineapple with TP-Link Archer C7 v2 Router
In the realm of cybersecurity, tools like the WiFi Pineapple have become indispensable for professionals…
DIY WiFi Pineapple vs. Real WiFi Pineapple: A Detailed Comparison
In the realm of cybersecurity and penetration testing, tools like the WiFi Pineapple have become…
Understanding WiFi Jamming Attacks: Detailed Explanation and Implications
WiFi jamming attacks represent a significant threat in the realm of wireless communication. These attacks…
Exploring Burp Suite: A Powerful Tool for Analyzing POST Data
The History of Burp Suite Burp Suite, developed by PortSwigger, has become a cornerstone in…
Cyberattack on ARRL Disrupts Logbook of the World
Introduction The American Radio Relay League (ARRL) has recently fallen victim to a cyberattack, significantly…
Empower Your Cybersecurity Journey with Linux: Why Ubuntu is the Perfect Starting Point
In the ever-evolving landscape of cybersecurity, staying ahead of potential threats is paramount. With the…
Understanding Firewall Policies: First Rule Win vs. Last Rule Win
Firewalls are vital guardians of network security, establishing a barrier between trusted internal networks and…
Unveiling the Arduino Bad USB: A Closer Look at Its Capabilities and Implications
In the ever-evolving landscape of technology, innovation brings both marvels and challenges. One such innovation…
Unveiling the Powerhouse: Hamas Cyber Division
Today, we turn our attention to a group that has been making headlines in recent…
Exploring BlackArch: The Penetration Tester’s Arsenal
In the realm of cybersecurity, where the battleground is constantly shifting and evolving, having the…
Unleashing Potential: The Flipper Zero Firmware Revolution
In the ever-evolving landscape of cybersecurity and hacker culture, one device has captured the imagination…
DefCon: Exploring the Epicenter of Cybersecurity at the Definitive Hacker Conference
Introduction: In this blog post, we will explore DefCon, the renowned annual security conference that…
N6NHG ( Kevin Mitnick ) – From Ham Radio Operator To Security Consultant
Kevin Mitnick, also known as N6NHG in ham radio world was the most wanted computer…