The Tor Project: Ensuring Anonymity Online
In an age where privacy and online security are paramount, the Tor Project stands as…
Unlocking the Ultimate Guide: The Book of Secret Knowledge on GitHub
Introduction In the ever-evolving world of technology, staying ahead of the curve requires continuous learning…
Metasploit: A Comprehensive Guide to History, Development, Usage, and Installation on Ubuntu Linux
Metasploit is a powerful and versatile tool used primarily for penetration testing and security auditing.…
DIY WiFi Pineapple Setup Guide: Building Your Own WiFi Pineapple with TP-Link Archer C7 v2 Router
In the realm of cybersecurity, tools like the WiFi Pineapple have become indispensable for professionals…
Building Your Own WiFi Pineapple Tetra: A Comprehensive Guide by Samy Younsi
In the cybersecurity world, tools like the WiFi Pineapple Tetra are essential for professionals and…
DIY WiFi Pineapple vs. Real WiFi Pineapple: A Detailed Comparison
In the realm of cybersecurity and penetration testing, tools like the WiFi Pineapple have become…
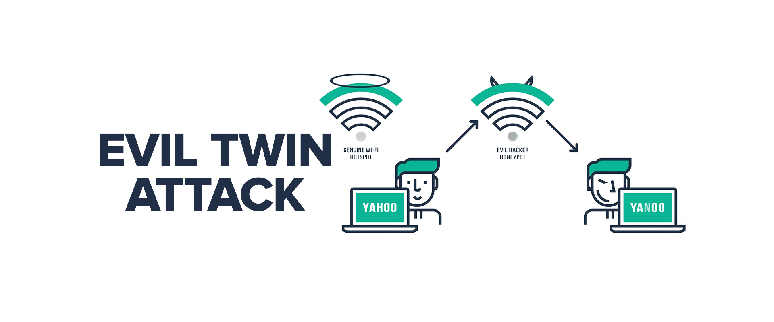
Understanding Evil Twin Attacks: History and Step-by-Step Guide to Gaining Passwords
The History of Evil Twin Attacks Evil Twin attacks are a sophisticated type of Wi-Fi…
Exploring Burp Suite: A Powerful Tool for Analyzing POST Data
The History of Burp Suite Burp Suite, developed by PortSwigger, has become a cornerstone in…
Unveiling the Evil Crow RF: Your Gateway to Radiofrequency Hacking
In the realm of cybersecurity, the pursuit of innovative tools and techniques to bolster defenses…
Flipper Blackhat: Unleash the Power of WiFi Hacking and Evil Portal Capabilities
Welcome to hamradio.my, where we explore the remarkable Flipper Blackhat, a WiFi hacking device designed…
The Birth of MonstaTek M1
"Hello World. It was only a matter of time that the imagination of tech geeks,…
Unleashing Potential: The Flipper Zero Firmware Revolution
In the ever-evolving landscape of cybersecurity and hacker culture, one device has captured the imagination…
Unveiling Momentum Firmware: Revolutionizing Flipper Zero’s Capabilities
In the realm of cybersecurity and penetration testing, tools are the unsung heroes of the…
Hak5: Revolutionizing the World of Cybersecurity with Innovative Tools and Expertise
Introduction: In today's blog post, we explore Hak5, a renowned company that has made significant…
WiFi Hash Purple Monster: Capturing EAPOL/PMKID Packets with M5Stack/ESP32
Introduction: Welcome to my tech blog, where we explore innovative devices and techniques. Today, we…
Unleashing the Power of Pwnagotchi: A Revolutionary Tool for Tech Enthusiasts
Introduction: Welcome to hamradio.my, your trusted source for all things tech-related. In today's blog post,…
UITM’s I-Hack 2010 Flag6.pcap
After i read my friend's post about flag6.pcap at UITM's I-hack 2010, i wonder how…
UITM’s I-Hack 2010
Congratulations to all winners
ICOM IC-706 MK II G Wideband Transmit Mod
This modification of the Icom 706 MK IIG ( At Your Own Risk! ) will…
N6NHG ( Kevin Mitnick ) – From Ham Radio Operator To Security Consultant
Kevin Mitnick, also known as N6NHG in ham radio world was the most wanted computer…
Ham Radio Village at HackInTheBox Security Conference 2009
Hack In The Box also known as HITB, a very popular once a year security…