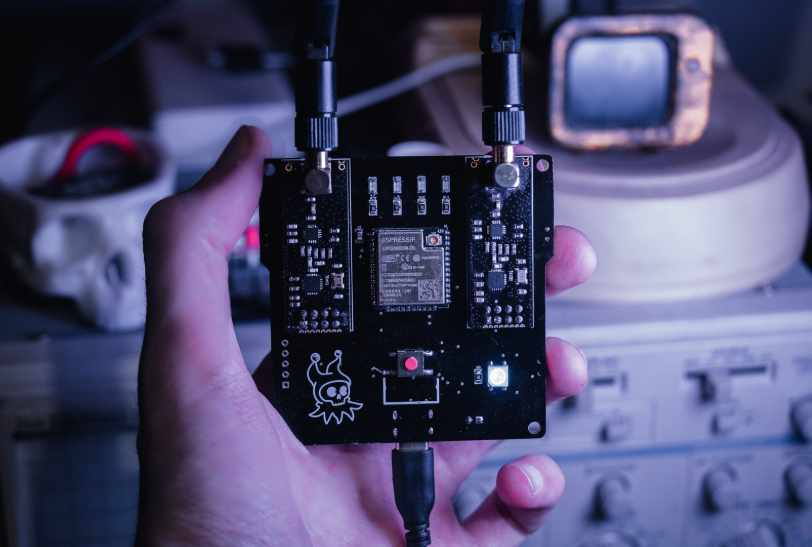
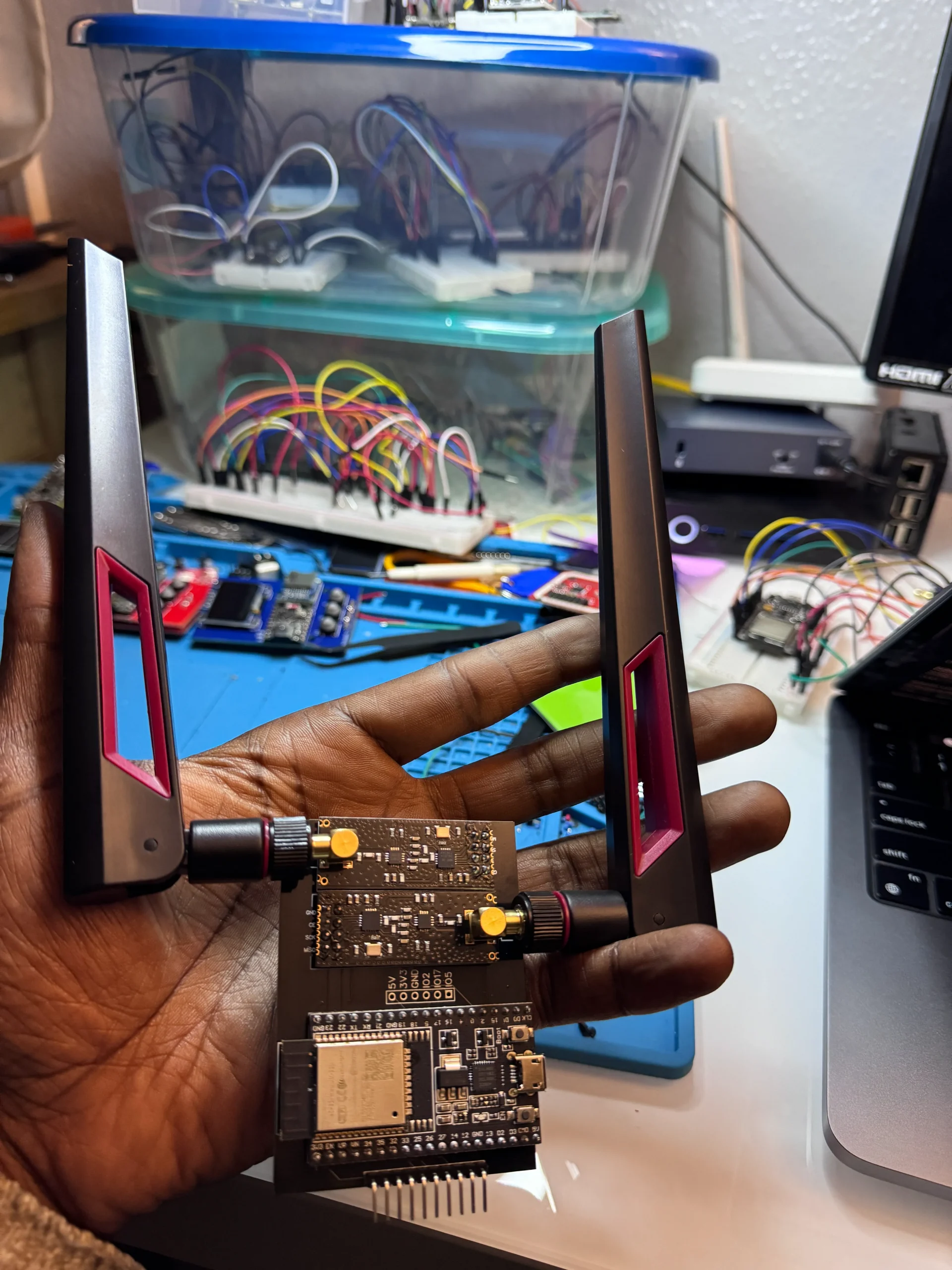
Meet the Cypher Jammer – The Open-Source Wireless Jamming Toolkit
Looking for a fun and educational pentesting project that blends hardware hacking and wireless experimentation?…
Project Starbeam: A Modular Signal Intelligence Platform for Tactical & Security Applications
Project Starbeam is here—and it’s unlike anything else in the open-source hardware world. Designed for…
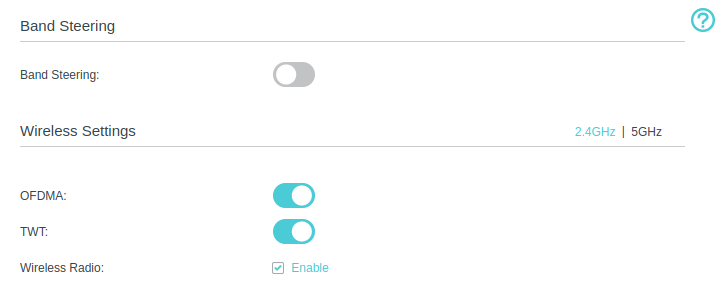
Should You Combine or Separate 2.4GHz and 5GHz Wi-Fi Bands? Let’s Break It Down
In the era of smart homes, streaming, and constant connectivity, your Wi-Fi setup can make…
How to Install TP-Link TXE70UH WiFi Adapter on Debian/Ubuntu
The TP-Link TXE70UH is a high-performance WiFi 6 adapter that offers blazing-fast speeds and improved…
Exploring Innovative Projects with Starlink: Connecting the Unconnected
Introduction Starlink, the satellite internet constellation developed by SpaceX, has revolutionized how we think about…
DIY WiFi Pineapple Setup Guide: Building Your Own WiFi Pineapple with TP-Link Archer C7 v2 Router
In the realm of cybersecurity, tools like the WiFi Pineapple have become indispensable for professionals…
Building Your Own WiFi Pineapple Tetra: A Comprehensive Guide by Samy Younsi
In the cybersecurity world, tools like the WiFi Pineapple Tetra are essential for professionals and…
DIY WiFi Pineapple vs. Real WiFi Pineapple: A Detailed Comparison
In the realm of cybersecurity and penetration testing, tools like the WiFi Pineapple have become…
Understanding WiFi Jamming Attacks: Detailed Explanation and Implications
WiFi jamming attacks represent a significant threat in the realm of wireless communication. These attacks…
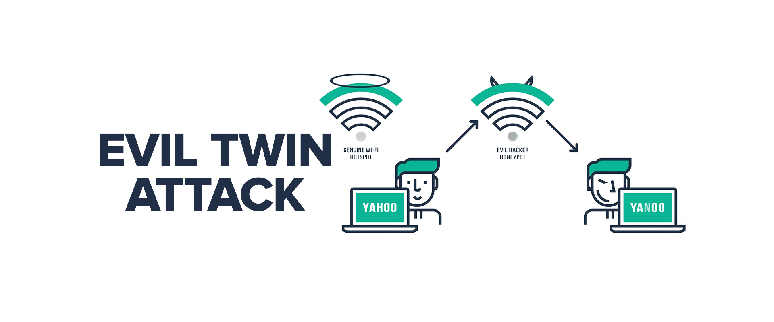
Understanding Evil Twin Attacks: History and Step-by-Step Guide to Gaining Passwords
The History of Evil Twin Attacks Evil Twin attacks are a sophisticated type of Wi-Fi…
Meneroka Wireless Broadband Leaky Coaxial Cables (WBLCX)
Dalam era digital hari ini, di mana ketersambungan adalah yang terpenting, inovasi dalam teknologi jalur…
Memahami Saluran WiFi dan Mengurangkan Kesesakan
Dalam dunia yang disambungkan secara digital, WiFi telah menjadi sebahagian daripada kehidupan seharian kita. Daripada…
Unveiling the Evil Crow RF: Your Gateway to Radiofrequency Hacking
In the realm of cybersecurity, the pursuit of innovative tools and techniques to bolster defenses…
Exploring the Benefits and Trade-offs: A Comparison of Throughput and CPU Usage between WPA3 and WPA2 Security on Wireless Networks
Introduction:In the realm of wireless communication, security is paramount. With the rise of vulnerabilities like…
Unraveling the Power of OpenWRT: A Comprehensive Guide
Introduction:In the world of networking, where flexibility, security, and customization are paramount, OpenWRT emerges as…
Flipper Blackhat: Unleash the Power of WiFi Hacking and Evil Portal Capabilities
Welcome to hamradio.my, where we explore the remarkable Flipper Blackhat, a WiFi hacking device designed…
Unlocking Wireless Secrets with the Universal Radio Hacker (URH)
In a world where wireless communication reigns supreme, understanding the intricate dance of signals that…
Exploring Wireless Security: WPA2 vs. WPA3
In the world of wireless communication, security is paramount. As the backbone of our interconnected…
Protecting Your Wireless Network: Understanding and Preventing PMKID Interception
In the digital age, concerns about cybersecurity are not unwarranted. With the prevalence of wireless…
Exploring the World of Wardriving: Unveiling the Secrets of Wireless Networks
In the digital age, where connectivity is paramount, the exploration of wireless networks has become…
The Birth of MonstaTek M1
"Hello World. It was only a matter of time that the imagination of tech geeks,…
WiFi Hash Purple Monster: Capturing EAPOL/PMKID Packets with M5Stack/ESP32
Introduction: Welcome to my tech blog, where we explore innovative devices and techniques. Today, we…
Kod Morse Dan Telegrafi
Kod Morse merupakan satu cara menyampaikan informasi berteks dalam satu siri bunyi atau cahaya yang…
Sharing Wireless Internet To Ethernet
Sometimes we need to share our wireless internet to an ethernet connected clients or anything…
How To Install BCM4312, BCM4306, BCM4301 Wireless Card Driver On Kali Linux
Add a "contrib" component to /etc/apt/sources.list, for example: # Debian Squeeze/6.0 deb http://ftp.us.debian.org/debian squeeze main…
How to select the operating mode of TP-LINK wireless multiple modes devices?
Suitable for: TL-MR3020, TL-MR3040, TL-WA5110G, TL-WA5210G, TL-WA7510N, TL-WR543G, TL-WR700N, TL-WR702N, TL-WR743ND Some TP-LINK devices have multiple…
Physically Small Spiral Antenna
http://www.google.com/patents/US7586462?printsec=abstract&dq=physically+small+spiral+antenna&ei=J1_QT4n2M9DOrQehlLiJDA#v=onepage&q=physically%20small%20spiral%20antenna&f=false
The simplicity of Morse code telegraphy
Morse code is an on-off code. It is not a binary code since the gaps…
Surviving With the Help of Morse Code
Everyone has heard of Morse code. It has been almost 144 years since its inception…
Surfin’: Radioing the Titanic
04/13/2012 By Stan Horzepa, WA1LOUContributing Editor This week, Surfin’ hops on the wayback machine and…
Inspiration and Perspiration — RMS Titanic Distress Signals Heard Again
06/01/2012 The 100th anniversary of the Titanic disaster involved many commemorative events around the world, from Belfast,…
Dot-dash-diss: The gentleman hacker’s 1903 lulz
A century ago, one of the world’s first hackers used Morse code insults to disrupt…
Antenna diversity
Antenna diversity, also known as space diversity, is any one of several wireless diversity schemes…
IEEE 802.22 Akan Menggunakan frekuensi TV VHF dan UHF
The IEEE has recently released the new 802.22 standard for Wireless Regional Area Network (WRAN)…
Browse The Internet With D-STAR Radio
http://en.wikipedia.org/wiki/D-STAR http://www.dstarusers.org/ http://www.dstarinfo.com/ p/s: thanks to N7ICE for the demonstration.
WIfite – Mass WEP/WPA Cracker For BackTrack4
introductiondesigned for Backtrack4 RC1 distribution of Ubuntu. Linux only; no windows or osx support. purposeto…
Beini – Tiny Core Linux Based Wireless Penetration Distro
Beini is tiny core linux based distro made for wireless penetration and auditing.It's special application…
Z Code
Z Code (like Q Code and X Code) is a set of codes used in…