Unlocking the Ultimate Guide: The Book of Secret Knowledge on GitHub
Introduction In the ever-evolving world of technology, staying ahead of the curve requires continuous learning…
Metasploit: A Comprehensive Guide to History, Development, Usage, and Installation on Ubuntu Linux
Metasploit is a powerful and versatile tool used primarily for penetration testing and security auditing.…
Unveiling Email Tracking: What You Need to Know
In today's digital landscape, email has revolutionized communication, making it convenient and efficient. However, beneath…
Understanding WiFi Jamming Attacks: Detailed Explanation and Implications
WiFi jamming attacks represent a significant threat in the realm of wireless communication. These attacks…
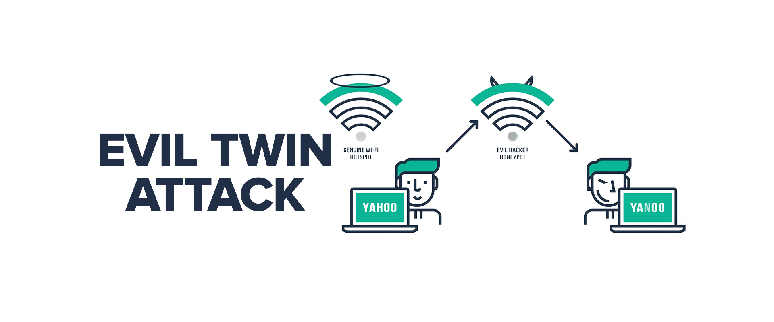
Understanding Evil Twin Attacks: History and Step-by-Step Guide to Gaining Passwords
The History of Evil Twin Attacks Evil Twin attacks are a sophisticated type of Wi-Fi…
Unveiling the Arduino Bad USB: A Closer Look at Its Capabilities and Implications
In the ever-evolving landscape of technology, innovation brings both marvels and challenges. One such innovation…
Unveiling the Powerhouse: Hamas Cyber Division
Today, we turn our attention to a group that has been making headlines in recent…
Exploring BlackArch: The Penetration Tester’s Arsenal
In the realm of cybersecurity, where the battleground is constantly shifting and evolving, having the…
Unlocking Wireless Secrets with the Universal Radio Hacker (URH)
In a world where wireless communication reigns supreme, understanding the intricate dance of signals that…
Protecting Your Wireless Network: Understanding and Preventing PMKID Interception
In the digital age, concerns about cybersecurity are not unwarranted. With the prevalence of wireless…
The Birth of MonstaTek M1
"Hello World. It was only a matter of time that the imagination of tech geeks,…
Unleashing Potential: The Flipper Zero Firmware Revolution
In the ever-evolving landscape of cybersecurity and hacker culture, one device has captured the imagination…
Unleash the Power of Flipper Zero with Xtream Firmware
In the realm of hardware hacking and cybersecurity, enthusiasts are constantly seeking new tools to…
Unveiling Momentum Firmware: Revolutionizing Flipper Zero’s Capabilities
In the realm of cybersecurity and penetration testing, tools are the unsung heroes of the…
Hak5: Revolutionizing the World of Cybersecurity with Innovative Tools and Expertise
Introduction: In today's blog post, we explore Hak5, a renowned company that has made significant…