How Netflix Powers the World’s Fastest Content Delivery Network with FreeBSD
When you stream your favorite Netflix show without buffering, you're witnessing the power of FreeBSD…
Essential Linux Commands Every System Administrator Should Know
As a system administrator, mastering the command line is critical. Whether you're maintaining servers, managing…
Software-Defined Networking (SDN): The Future of Flexible Network Infrastructure
In an age where speed, scalability, and automation are king, traditional networking methods are struggling…
How to Set Up a Caching Proxy Server to Speed Up Your Local Network
Does your home or office internet feel sluggish, especially when multiple people are browsing? You…
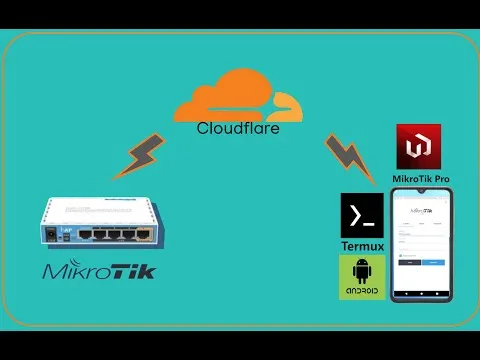
Hosting a Web Server Securely with Cloudflare Zero Trust Tunnel on MikroTik (Using Docker)
You have a web server running in your home network — maybe it’s a dashboard,…
How to Set Up Chrony as a Local NTP Server Using Docker
In a local network where you want to keep your devices synchronized with accurate time,…
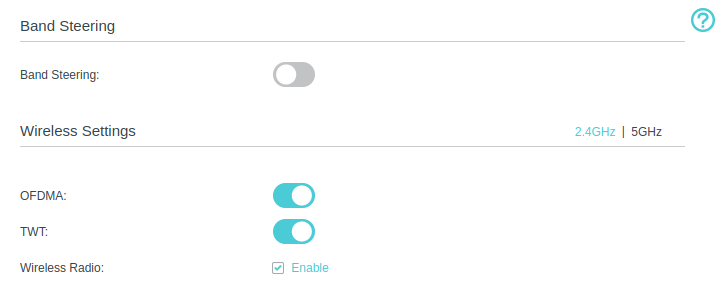
Should You Combine or Separate 2.4GHz and 5GHz Wi-Fi Bands? Let’s Break It Down
In the era of smart homes, streaming, and constant connectivity, your Wi-Fi setup can make…
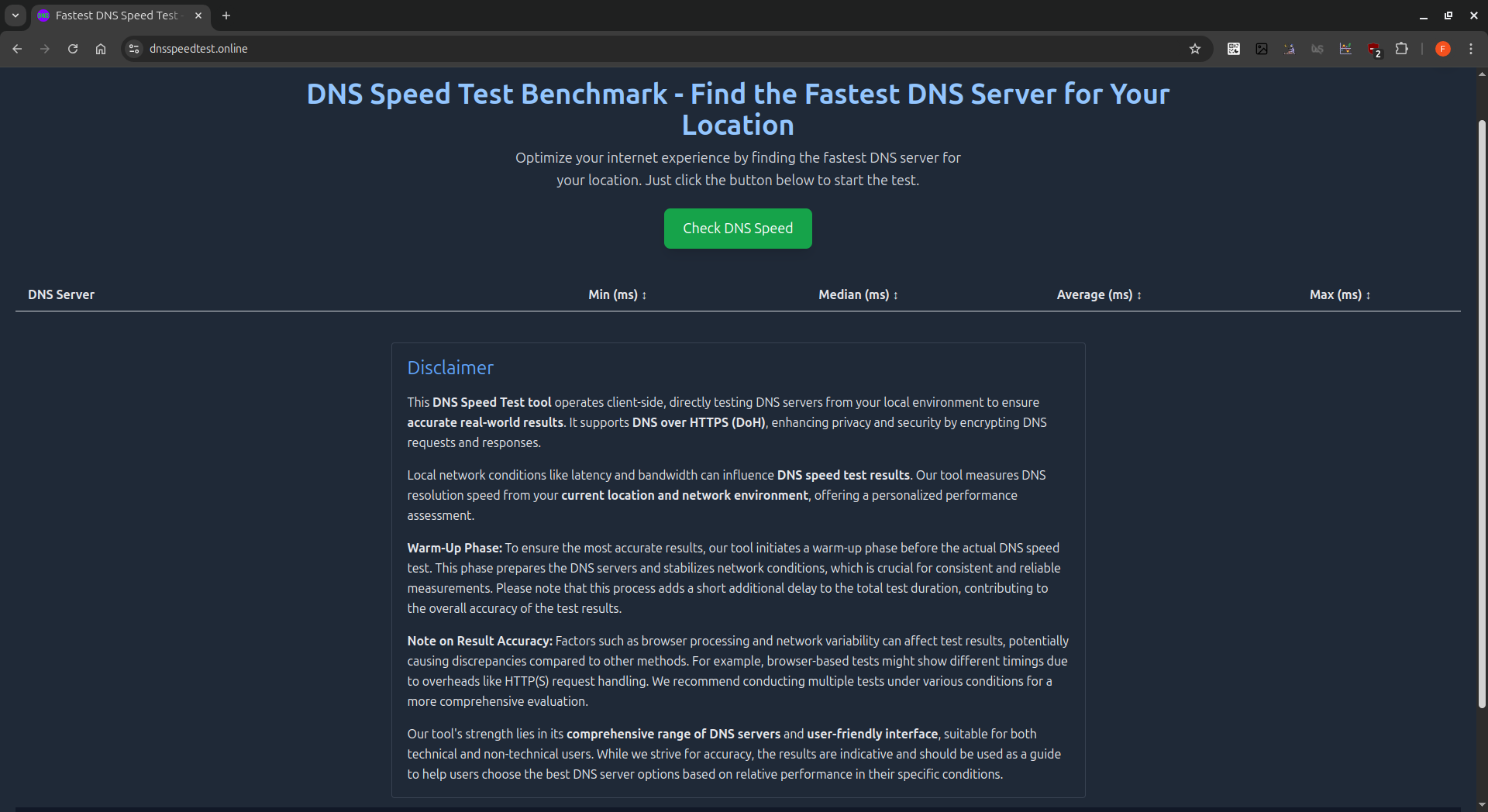
Boost Your Amateur Radio Internet Performance with the Fastest DNS Server
As an amateur radio operator, having a reliable internet connection is essential for various activities…
Reticulum: The Future of Secure and Resilient Networking
In a world where digital communication is often subject to surveillance, censorship, and centralized control,…
Raspberry Pi 5: Revolutionizing Maker Technology – An Exploration
The Evolution of a Tech Phenomenon When the Raspberry Pi Foundation first introduced their single-board…
Automating FreeBSD Container Management with Bastille
Bastille is an open-source system designed to automate the deployment and management of containerized applications…
The 9M2PJU-DXSpider-Docker Project
Revolutionizing Amateur Radio DX Clustering with Docker Amateur radio operators are always looking for ways…
9M2PJU IPv4 Calculator Chrome Extension
Are you tired of manually calculating IPv4 address details? Look no further! We are thrilled…
Unveiling Zero Trust Network Access (ZTNA): The Future of Secure Networking
In today's digital landscape, the traditional network security model is increasingly insufficient to protect against…
Exploring Network Tunnels: History, Usage, Applications, and Misuse
In the realm of computer networking, tunnels play a crucial role in facilitating secure communication,…
Unveiling Email Tracking: What You Need to Know
In today's digital landscape, email has revolutionized communication, making it convenient and efficient. However, beneath…
Building Your Own WiFi Pineapple Tetra: A Comprehensive Guide by Samy Younsi
In the cybersecurity world, tools like the WiFi Pineapple Tetra are essential for professionals and…
Exploring Portmaster: The Privacy-Oriented Firewall
In an era where online privacy is increasingly important, having robust cybersecurity measures in place…
Understanding WiFi Jamming Attacks: Detailed Explanation and Implications
WiFi jamming attacks represent a significant threat in the realm of wireless communication. These attacks…
Understanding Firewall Policies: First Rule Win vs. Last Rule Win
Firewalls are vital guardians of network security, establishing a barrier between trusted internal networks and…
Eksesais Jaringan MikroTik dan Simulasi Pemantauan Gunung Berapi oleh Tentara Nasional Indonesia
Tentara Nasional Indonesia (TNI) telah lama menjadi contoh utama dalam menggabungkan teknologi canggih dengan strategi…
Cara Menyekat YouTube Menggunakan RAW pada MikroTik
Dalam era digital hari ini, YouTube telah menjadi platform di mana-mana untuk hiburan, pendidikan dan…
Meneroka Wireless Broadband Leaky Coaxial Cables (WBLCX)
Dalam era digital hari ini, di mana ketersambungan adalah yang terpenting, inovasi dalam teknologi jalur…
Memahami Saluran WiFi dan Mengurangkan Kesesakan
Dalam dunia yang disambungkan secara digital, WiFi telah menjadi sebahagian daripada kehidupan seharian kita. Daripada…
Enhancing Network Security with the Viasat KG-250X/KG-250X-FC: A Low-SWaP Solution for TS/SCI Communications
In today's interconnected world, securing sensitive data is paramount, especially for government agencies and military…
Unlocking the Doors of Security: Exploring the World of Port Knocking
In the realm of cybersecurity, where threats loom large and defenses must be ever more…
Exploring the Benefits and Trade-offs: A Comparison of Throughput and CPU Usage between WPA3 and WPA2 Security on Wireless Networks
Introduction:In the realm of wireless communication, security is paramount. With the rise of vulnerabilities like…
Understanding Bufferbloat: Causes, Consequences, and Solutions
In today's digitally interconnected world, where we rely heavily on seamless internet connectivity for work,…
Unraveling the Power of OpenWRT: A Comprehensive Guide
Introduction:In the world of networking, where flexibility, security, and customization are paramount, OpenWRT emerges as…
ARPANET and DARPANET: Pioneering the Path to the Internet Age
Introduction: In this article, we embark on a journey back in time to explore the…
Unleashing Potential: The Flipper Zero Firmware Revolution
In the ever-evolving landscape of cybersecurity and hacker culture, one device has captured the imagination…
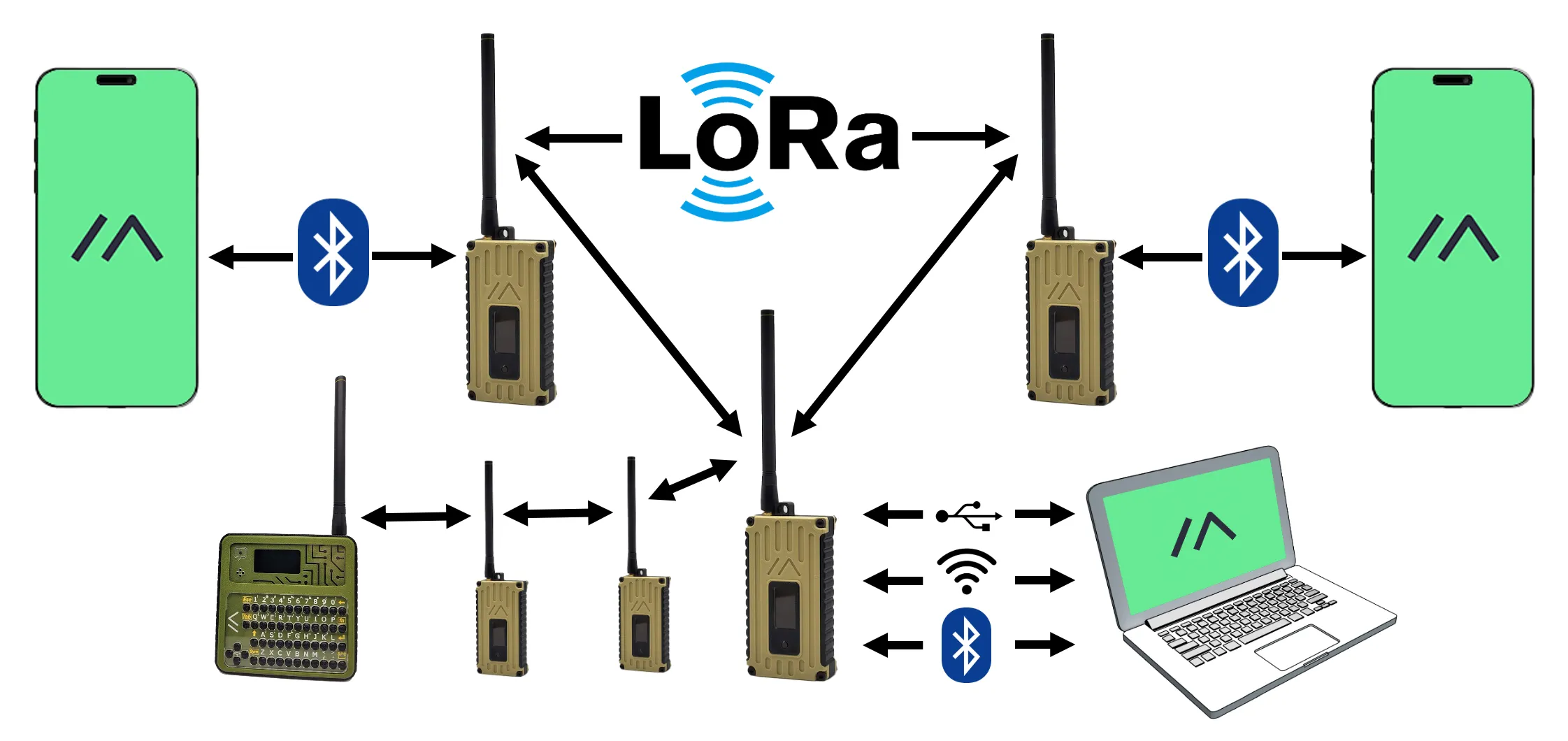
Embrace the Power of Meshtastic: Revolutionizing Communication in Remote Areas
Introduction: Greetings, esteemed readers of hamradio.my! Today, we have an exciting topic to discuss that…