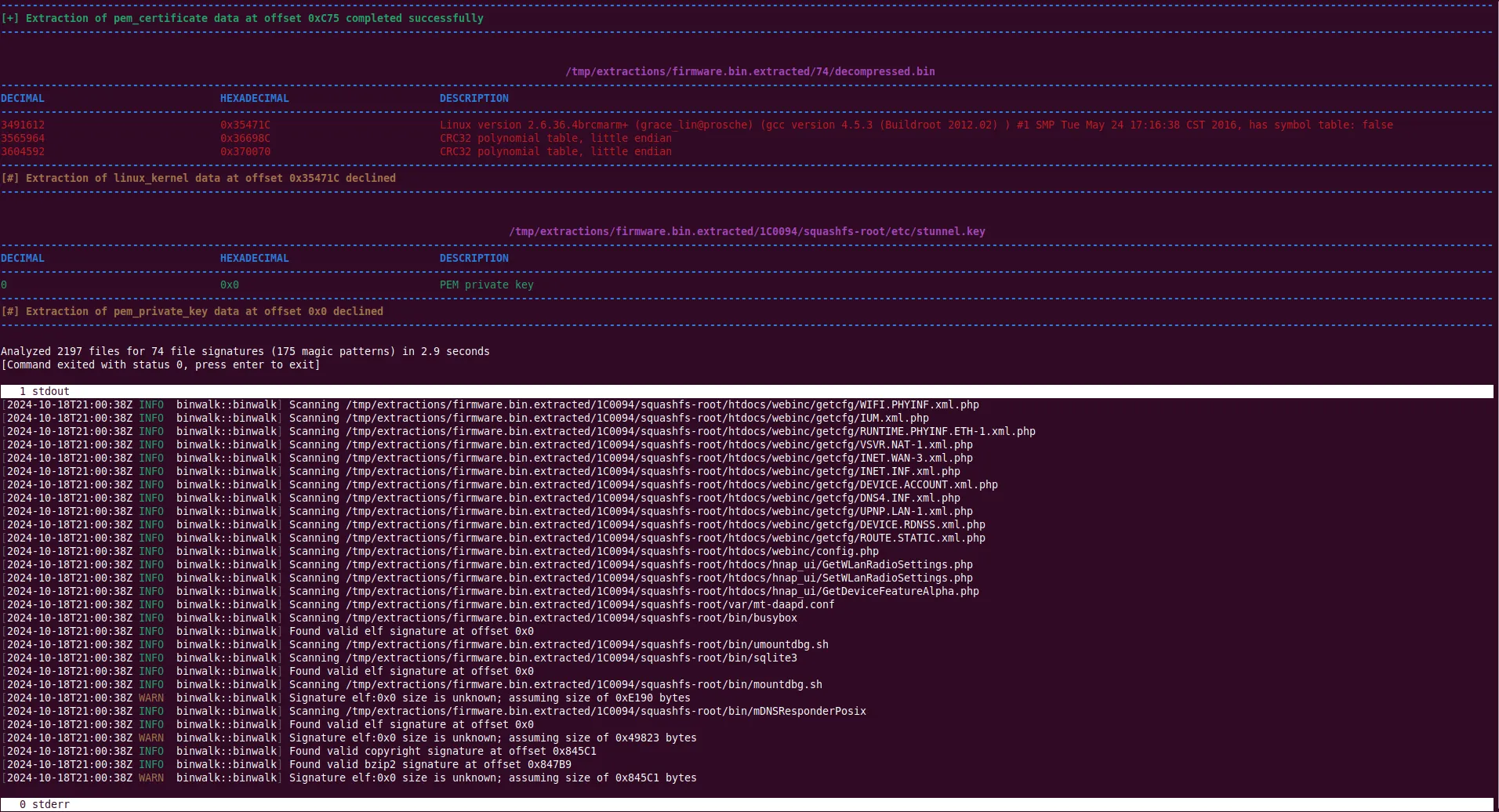
Unlocking Firmware Secrets with Binwalk: A Powerful Tool for Amateur Radio Enthusiasts
As technology evolves, amateur radio operators are increasingly exploring software-defined radios (SDRs), digital modes, and…
Reticulum: The Future of Secure and Resilient Networking
In a world where digital communication is often subject to surveillance, censorship, and centralized control,…
Automating FreeBSD Container Management with Bastille
Bastille is an open-source system designed to automate the deployment and management of containerized applications…
Snap vs Flatpak: A Detailed Comparison
Snap vs Flatpak: A Detailed Comparison When it comes to Linux software installation, Snap and…
The Tor Project: Ensuring Anonymity Online
In an age where privacy and online security are paramount, the Tor Project stands as…
Understanding China’s Social Security and Social Credit System
China's Social Security System:China's social security system is a comprehensive framework designed to provide its…
Enhancing WordPress Security with Wordfence: A Comprehensive Guide
In the dynamic world of WordPress websites, security is a paramount concern. Given the platform’s…
Unleashing CyberChef: Your Ultimate Cybersecurity Swiss Army Knife
In the realm of cybersecurity, having the right tools at your disposal can mean the…
Unlocking the Ultimate Guide: The Book of Secret Knowledge on GitHub
Introduction In the ever-evolving world of technology, staying ahead of the curve requires continuous learning…
Metasploit: A Comprehensive Guide to History, Development, Usage, and Installation on Ubuntu Linux
Metasploit is a powerful and versatile tool used primarily for penetration testing and security auditing.…
Unveiling Email Tracking: What You Need to Know
In today's digital landscape, email has revolutionized communication, making it convenient and efficient. However, beneath…
Exploring Portmaster: The Privacy-Oriented Firewall
In an era where online privacy is increasingly important, having robust cybersecurity measures in place…
Understanding WiFi Jamming Attacks: Detailed Explanation and Implications
WiFi jamming attacks represent a significant threat in the realm of wireless communication. These attacks…
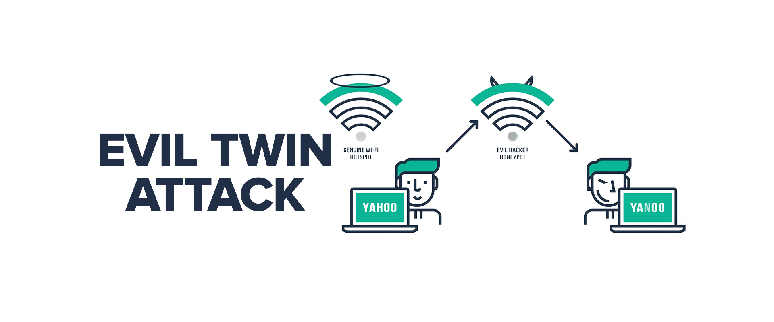
Understanding Evil Twin Attacks: History and Step-by-Step Guide to Gaining Passwords
The History of Evil Twin Attacks Evil Twin attacks are a sophisticated type of Wi-Fi…
The Air Marshal: Guardians of the Skies
Introduction In the complex and evolving landscape of global aviation security, the role of air…
Unveiling the Art of Penetration Testing: Embark on Your Journey with Ubuntu
Welcome, aspiring ethical hackers and cybersecurity enthusiasts, to the exhilarating world of penetration testing! If…
Enhancing Security Posture Assessment with Open-Source Software on Ubuntu Linux
In the realm of cybersecurity, maintaining a robust security posture is paramount to safeguarding organizations…
Building Your Own Security Operations Center (SOC) Using Open-Source Software: A Comprehensive Guide
In today's digital landscape, organizations face an ever-increasing number of cyber threats. Establishing a Security…
Exploring MIPS: An Open-Source Threat Intelligence and Sharing Platform
In the dynamic landscape of cybersecurity, robust threat intelligence platforms are essential for proactive defense…
Understanding Wazuh: Installation and Configuration on Ubuntu
What is Wazuh? Wazuh is an open-source security monitoring platform that helps organizations detect threats,…
The Ultimate Guide to Tactical Pens: Everything You Need to Know
In an age where personal safety and preparedness are becoming increasingly important, tactical pens have…
Keeping Your System Secure with KernelCare: A Comprehensive Guide for Ubuntu Users
In today's digital landscape, security is paramount, especially for those managing servers and critical infrastructure.…
Securing Ubuntu with DISA-STIG Compliance
In the realm of cybersecurity, stringent measures are essential to safeguard sensitive data and critical…
Embrace Ubuntu: A Financially Savvy Guide to Ditching Microsoft Windows and Prioritizing Security, Privacy, and Savings
In an era where digital empowerment and financial prudence are increasingly intertwined, the decision to…
Understanding Firewall Policies: First Rule Win vs. Last Rule Win
Firewalls are vital guardians of network security, establishing a barrier between trusted internal networks and…
CryptoGrabber P31: Merevolusikan Keselamatan Kenderaan
Dalam landskap teknologi automotif yang sentiasa berkembang, inovasi terus mentakrifkan semula sempadan di antara kemudahan…
Enhancing Network Security with the Viasat KG-250X/KG-250X-FC: A Low-SWaP Solution for TS/SCI Communications
In today's interconnected world, securing sensitive data is paramount, especially for government agencies and military…
Unveiling the Evil Crow RF: Your Gateway to Radiofrequency Hacking
In the realm of cybersecurity, the pursuit of innovative tools and techniques to bolster defenses…
Unlocking the Doors of Security: Exploring the World of Port Knocking
In the realm of cybersecurity, where threats loom large and defenses must be ever more…
Exploring the Benefits and Trade-offs: A Comparison of Throughput and CPU Usage between WPA3 and WPA2 Security on Wireless Networks
Introduction:In the realm of wireless communication, security is paramount. With the rise of vulnerabilities like…
Unveiling the Arduino Bad USB: A Closer Look at Its Capabilities and Implications
In the ever-evolving landscape of technology, innovation brings both marvels and challenges. One such innovation…
Introduction to the Proxmark Platform
The Proxmark is an RFID swiss-army tool, allowing for both high and low level interactions…
Unveiling the Powerhouse: Hamas Cyber Division
Today, we turn our attention to a group that has been making headlines in recent…
Exploring BlackArch: The Penetration Tester’s Arsenal
In the realm of cybersecurity, where the battleground is constantly shifting and evolving, having the…
Unlocking Wireless Secrets with the Universal Radio Hacker (URH)
In a world where wireless communication reigns supreme, understanding the intricate dance of signals that…
Exploring Wireless Security: WPA2 vs. WPA3
In the world of wireless communication, security is paramount. As the backbone of our interconnected…
Protecting Your Wireless Network: Understanding and Preventing PMKID Interception
In the digital age, concerns about cybersecurity are not unwarranted. With the prevalence of wireless…
Exploring the World of Wardriving: Unveiling the Secrets of Wireless Networks
In the digital age, where connectivity is paramount, the exploration of wireless networks has become…
The Birth of MonstaTek M1
"Hello World. It was only a matter of time that the imagination of tech geeks,…
Unleashing Potential: The Flipper Zero Firmware Revolution
In the ever-evolving landscape of cybersecurity and hacker culture, one device has captured the imagination…
Unleash the Power of Flipper Zero with Xtream Firmware
In the realm of hardware hacking and cybersecurity, enthusiasts are constantly seeking new tools to…
Unveiling Momentum Firmware: Revolutionizing Flipper Zero’s Capabilities
In the realm of cybersecurity and penetration testing, tools are the unsung heroes of the…
DefCon: Exploring the Epicenter of Cybersecurity at the Definitive Hacker Conference
Introduction: In this blog post, we will explore DefCon, the renowned annual security conference that…
Hak5: Revolutionizing the World of Cybersecurity with Innovative Tools and Expertise
Introduction: In today's blog post, we explore Hak5, a renowned company that has made significant…
Cloudflare WARP: Unleashing Secure and Speedy Internet Connectivity
Introduction:In an era where online privacy and security are paramount, Cloudflare WARP emerges as a…